TechnologyMay 30, 2021
Device level security for critical automation applications

Adding an extra layer of defense-in-depth security, particularly for motion applications, is an inexpensive way to make a facility a more hardened target that will discourage malicious actors in the first place and help to slow them down long enough to enable other defenses to expose and expel them from your network.
A great deal of well-deserved focus is placed on high level network security in switches and routers with machine learning driven network monitoring, deep packet inspection, abnormal behavior algorithms, and allowed listing among the many valuable defensive measures. What happens if a bad actor makes it past passwords, firewalls, and DMZs in addition to all of the aforementioned important, advanced layers of protection?
Controllers and devices that start and stop the motion of machines are a particularly high value target for threat actors and concern for end users because these devices can be misused to cause great physical and financial harm. Adding an extra layer of defense, particularly for motion applications, is an inexpensive way to make your facility a more hardened target that will discourage malicious actors in the first place and help to slow them down long enough to enable other defenses to expose and expel them from your network. This is why ODVA recommends a complete defense in depth approach, including robust device level security.
CIP Security for automation
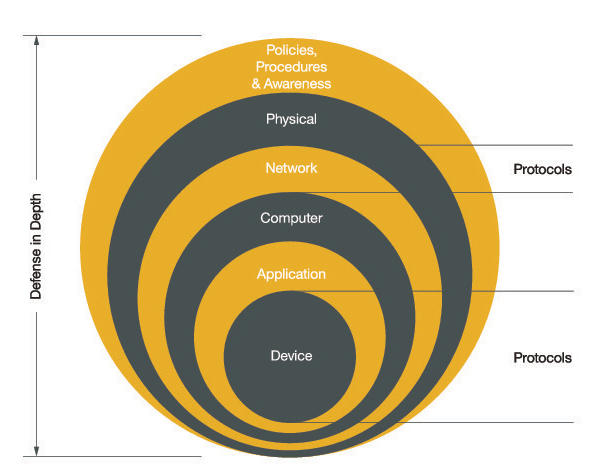
Defense in Depth Approach.
CIP Security is a cybersecurity network extension for EtherNet/IP that provides the last mile of security-related requirements and capabilities for devices. The goal of CIP Security is to enable EtherNet/IP devices to protect themselves from malicious communications. A self-defending CIP Security enabled device is able to reject data that has been altered (integrity), reject messages sent by untrusted people or untrusted devices (authenticity), and to reject messages that request actions that are not allowed (authorization).
CIP Security for EtherNet/IP devices makes use of the IETF-standard Transportation Layer Security (RFC 5246) and Datagram Transport Layer Security (RFC 6347) protocols in order to provide a secure transport for EtherNet/IP traffic. TLS is used for the TCP-based communications such as diagnostics and commissioning, and DTLS for the UDP-based transport communications such as I/O data.
Secure EtherNet/IP transport provides the following security attributes:
- Authentication of the endpoints: ensuring that the target and originator are both trusted entities. End point authentication is accomplished using X.509 certificates or pre-shared keys.
- Message integrity and authentication: ensuring that the message was sent by the trusted endpoint and was not modified in transit. Message integrity and authentication is accomplished via TLS message authentication code (HMAC).
- Message encryption: optional capability to encrypt the communications, provided by the encryption algorithm that is negotiated via the TLS handshake.
The ultimate roadmap for CIP Security development is to enable EtherNet/IP devices to become autonomous, taking responsibility for their own security and effectively securing themselves from attack.
CIP Security flexibility & options
CIP Security provides device authentication, a trust domain, device identity, device integrity, data confidentiality, user authentication, and policy enforcement (authorization). This is accomplished through three separate security profiles that provide flexibility for vendors in adding security features to their device depending on the intended application(s) and use case(s). A security profile is a set of well-defined capabilities to facilitate device interoperability and end-user selection of devices with the appropriate security capability.
The first security profile is the EtherNet/IP Confidentiality Profile, which provides secure communications between EtherNet/IP endpoints to assure data confidentiality. The second profile is the CIP User Authentication Profile, which provides Authentication at a user level for CIP communications.
This is used as a basis for Authorization and Role Based Access Control. The third profile is the Resource-Constrained CIP Security Profile, which provides a lightweight version of the protections afforded by the first two CIP Security profiles specifically for highly resource-constrained devices.
| Security Properties | EtherNet/IP Confidentiality Profile | CIP User Authentication Profile | Resource-Constrained CIP Security Profile |
|---|---|---|---|
| Device Authentication | X | X | |
| Trust Domain | Broad – group of devices | Narrow – Users/Roles | Broad; option to be Narrow via Gateway or Proxy |
| Device Identity | X | X (Identity of User) | X (via PSK) |
| Device Integrity | X | X | |
| Data Confidentiality | X | X | |
| User Authentication | X | Via Gateway or Proxy | |
| Change Detection (Audit) | |||
| Policy Enforcement (Authorization) | Fixed | Via Gateway or Proxy |
Resource-constrained devices
Despite the progress brought about by Industry 4.0 and the Industrial Internet of Things (IIoT), a large portion of the installed nodes in automation applications are still not using Ethernet.
Limitations including cost, size, and power have historically been a hindrance to EtherNet/IP pushing out to the edge of the network. The recent integration of Single Pair Ethernet has opened up the door to overcoming lower-level device constraints and ultimately to expanding the footprint of EtherNet/IP.
Adding simpler devices to EtherNet/IP allows for the benefits of additional remote diagnostics, asset information, and parameterization capability. The addition of more nodes to the network within the context of IT/OT convergence makes device level security a fundamental need to ensure that indispensable assets and people are protected from physical harm and monetary loss.
The protections offered by CIP Security are now available for EtherNet/IP networks via a resource-constrained version of CIP Security that includes fewer mandatory features. This ensures that devices with the smallest power, size, and cost budgets can be secure and enjoy the communication and control advantages of being connected to an EtherNet/IP network.
CIP Security can now provide device authentication, a broad trust domain, device identity via Pre-Shared Keys (PSKs), device integrity, and data confidentiality for resource-constrained devices such as contactors and push-buttons.
Additionally, functionality is provided to allow the resource-constrained device to seamlessly integrate with a proxy or gateway device which performs access policy enforcement on behalf of the resource-constrained device
Connectivity end state
As the inevitable march toward seamless device to enterprise connectivity plods forward, driven by Industry 4.0 and Industrial IoT, the reality is that automation devices that control the motion of motors, drives, pneumatic cylinders, etc. will be opened up to both the business benefits as well as the potential for unwanted intrusion as a result of internet connectivity. Today, many machines and skids are already connected via cellular data to allow OEMs to provide end users with remote operations support.
Even the best designed second communication channel for diagnostics can still potentially expose valuable intellectual property and trade secrets. Avoiding all external exposure of automation devices is of course possible, but then the user will not be able to take advantage of the diagnostic and prognostic benefits afforded by increased connectivity.
In the absence of this extreme measure, adding device level security is a low-cost protection that provides a last level of defense for critical motion control devices.
ODVA is committed to providing users with the most secure automation network solutions via CIP Security, which will continue to be enhanced to add new capabilities and protections as technology and threats evolve.
Steve Fales, ODVA

