TechnologyJanuary 9, 2020
Industrial edge control security design and best practices

To address security’s complex, changing nature, system designers need to understand security risks and their environment, along with the security tools they have to work with. Security experts recognize several elements of system security including physical security, policies and procedures, and network security.
The latest generation of edge control technology has been designed from the ground up to help system designers build a secure system for gathering, processing, and sharing useful data from industrial equipment. The result is industrial real-time controller technology that has been designed to maintain a high level of cyber security features and configurable options.
For all digital systems, security is a complex issue with different implications depending on the organization and systems. Security system requirements constantly change as the control system evolves, and building security into the system design is key to success. As Bruce Schneier wrote in 2000, “Security is a process, not a product.”
To address security’s complex, changing nature, system designers need to understand security risks and their environment, and the security tools they have to work with. Security experts recognize several elements of system security, including physical security, policies and procedures, and network security. Technology such as Opto 22’s groov EPIC has been designed to address network security requirements as a primary goal.
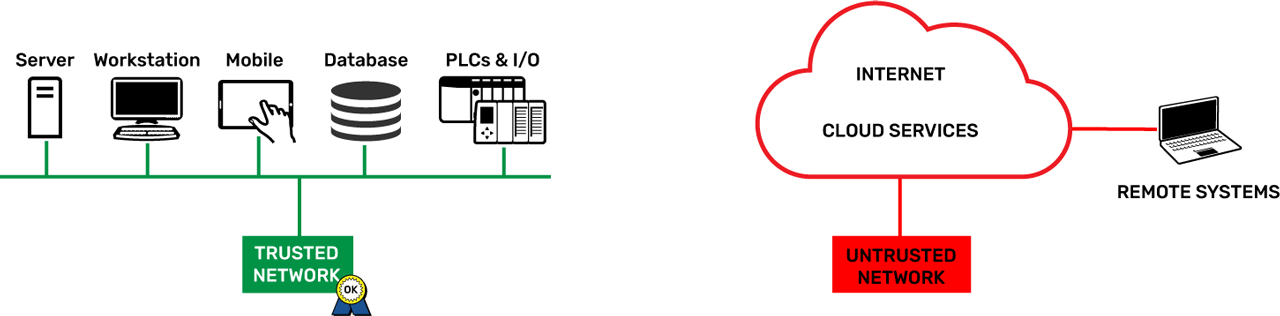
A trusted network is any network where you know exactly who has access to it. An untrusted network is any network where you don’t know who has access, like the Internet.
The objective is to provide tools and methods necessary to make the system as secure as possible from a network access standpoint, while maintaining flexibility for a variety of implementations.
The ultimate security of the system depends on adhering to system best practices and organizational discipline. This article describes security features and lists best practices for setting up a secure system along with an update on the latest technology.
Operating system
Unlike traditional controllers and computers typically used in automation or industrial internet of things (IIoT) applications, the groov EPIC processors have an open-source Linux operating system. Contrary to conventional wisdom, an open-source OS is in many ways more secure than a closed one (especially a well-known and often-attacked OS such as Microsoft Windows).
By design, this edge control technology includes only the operating system components necessary for its purpose, which reduces attack vectors. Contrast this limited vulnerability with Windows, for example, which includes components for all kinds of purposes. “The easiest vulnerability to address is the one you don’t include,” noted Ryan Ware, Security Architect at Intel, in 2017.
In addition, open source means crowd sourced. Because of the number of developers working on Linux, vulnerabilities tend to be addressed very quickly—far more quickly than they can be at an individual software company with a limited number of developers.
And most importantly, the Yocto build of EPIC Linux technology is cryptographically signed with a Private Key. That means that any firmware or software package a hacker might try to upload to the EPIC processor will not be accepted; only firmware and packages that are cryptographically signed can be loaded.
A WiFi network (a WLAN) can be added to the edge controller using an approved USB WiFi adapter connected to the EPIC processor’s USB port.
Network interfaces
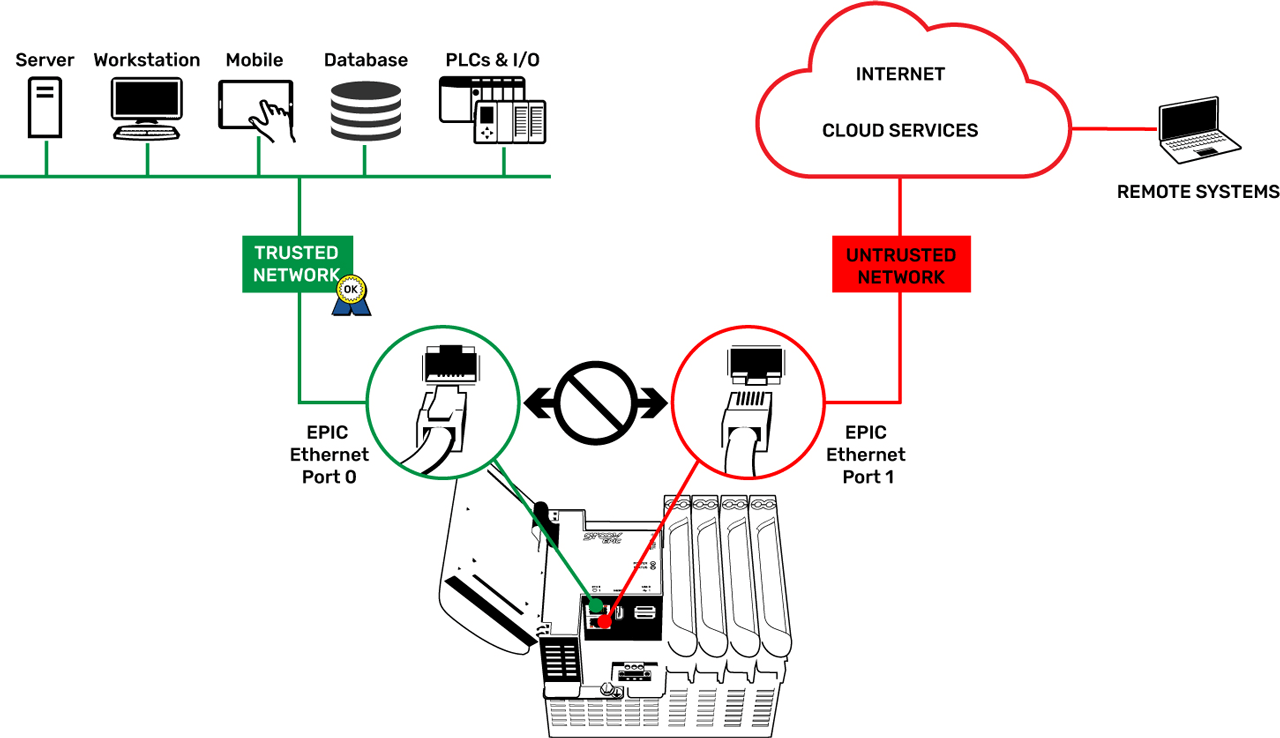
The controller architecture includes two independent Ethernet interfaces that segment trusted networks (ETH0) from untrusted networks (ETH1). A trusted network is any network where system managers know exactly who has access as with, for example, an IT-managed corporate network. An untrusted network is any network where managers don’t know who has access to it, like the internet.
The underlying groov EPIC technology and controller architecture is not a router, which functions to join two networks together. Instead, it works by keeping trusted networks isolated from untrusted networks by not routing network traffic between its network interfaces.
In addition, users can add a WiFi network (a WLAN) using an approved USB WiFi adapter connected to the processor’s USB port. The wireless network interface is independent from both Eth0 and Eth1, and does not route network traffic between any of its network interfaces.
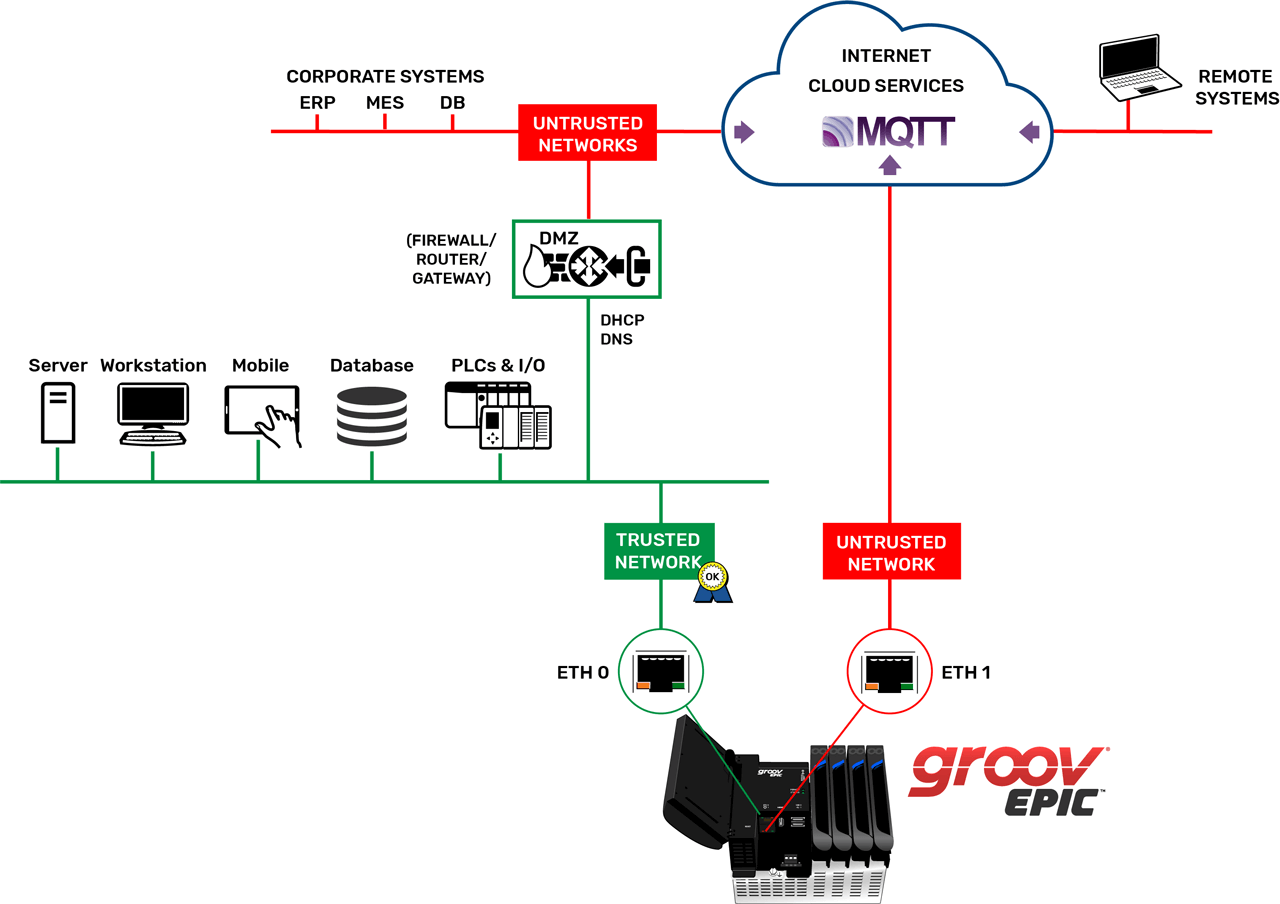
Device-originated communication may be referred to as using an outbound port. When the device must open a port to receive communications originated from outside, it may be called an inbound port. Through outbound, device-originating data communications such as MQTT, the controller technology offers a secure option that requires far less configuration.
Networking tools
On all network interfaces, the controller technology uses standard network services like DHCP which can be configured to use optional static IP configurations, if necessary, but the default is DHCP and DNS. For name resolving and outbound, device-originating access to other networks, a software management tool can be used to choose standard DNS and Gateway addresses and automatic or manual configuration.
Firewalls
Firewalls are critical in securing data communications. The EPIC processor and system design offers a configurable firewall, which is critical in addressing system security. Generally speaking, firewalls help provide security by stopping unsolicited traffic from accessing the network or device/host. Typically the only traffic they allow through is responses to traffic that originated from the inside. Device-originated connections are considered trustworthy because their origin is known. Most firewalls—including corporate firewalls (network firewalls) and the firewall in groov EPIC technology (a device or host firewall)—permit devices or services behind the firewall to originate communications outbound to external servers or services.
At the same time, these firewalls generally block all inbound connection attempts originating from devices and services outside the firewall. However, a firewall may allow inbound connections when a specific port has been configured open to allow them.
Default firewall configuration
The EPIC processor’s internal firewall default configuration assumes that users are implementing the two wired network interfaces as designed to segment trusted and untrusted networks. On the Ethernet trusted network interface (ETH0), it allows network communications through necessary but unsecure industrial protocol ports that are configured open. These ports allow communication with software and protocols in the EPIC processor, for example: PAC Control and CODESYS development tools, OptoMMP (protocol used by EPIC’s I/O) along with Modbus/TCP and Ignition Edge Designer for communication with PLCs and other devices.
On the Ethernet untrusted network interface (ETH1), the controller technology opens secure port 443 and permits only authenticated access over secure, encrypted connections. This network interface provides authenticated, encrypted access to additional software components including groov Manage, groov View, and RESTful APIs.
All other inbound connection ports on the ETH1 Ethernet network interface are blocked by default. In the system’s software tool, users can manage the configuration for each network interface is shown by application, so users can clearly see which applications are allowed access and which are denied.
Users can configure the EPIC’s firewall for each network interface to suit specific applications. For example, the default configuration can be changed to close ports for any services that won’t be used. If the system is not using Modbus/TCP, port 8502 can be closed to not allow any traffic, even on the trusted network interface.
Clients and servers
The technology has been designed so that individual controllers can act as both a client (a device that originates connections) and a server (a device that listens for requests to connect). Firewall configuration varies based on how the controller acts.
For example, MQTT and Node-RED running on the system are clients that originate communications. MQTT originates communications to MQTT brokers, and Node-RED originates communications to SQL servers, cloud-based services, and so on. No firewall configurations are needed for MQTT or Node-RED. Their communications are outbound and by default are allowed by the firewall.
The groov View software running on EPIC is a server that listens for connection requests from PCs or mobile devices running browsers. By default, its firewall is configured to open the secure port used to allow incoming connections. These connections are encrypted and must be authenticated by users.
Whether the edge controller technology is acting as a client or a server, once communications are established, data can flow in both directions as long as the connection is active.
Accounts
This edge controller technology has been designed so that users must create an administrator account with a username and password before doing anything else. The system processor does not have a default username or password that someone might be able to guess. The administrator account credentials a user creates is not recoverable.
Users can create administrator, developer, operator, REST API, and other accounts, and assign those user rights to authorized people or software services. Authentication (over an encrypted connection) is by either username/password or API token. All users can create long, complex passwords consisting of numbers, capitalization, punctuation, spaces, phrases and words in any language, and even emoticons.
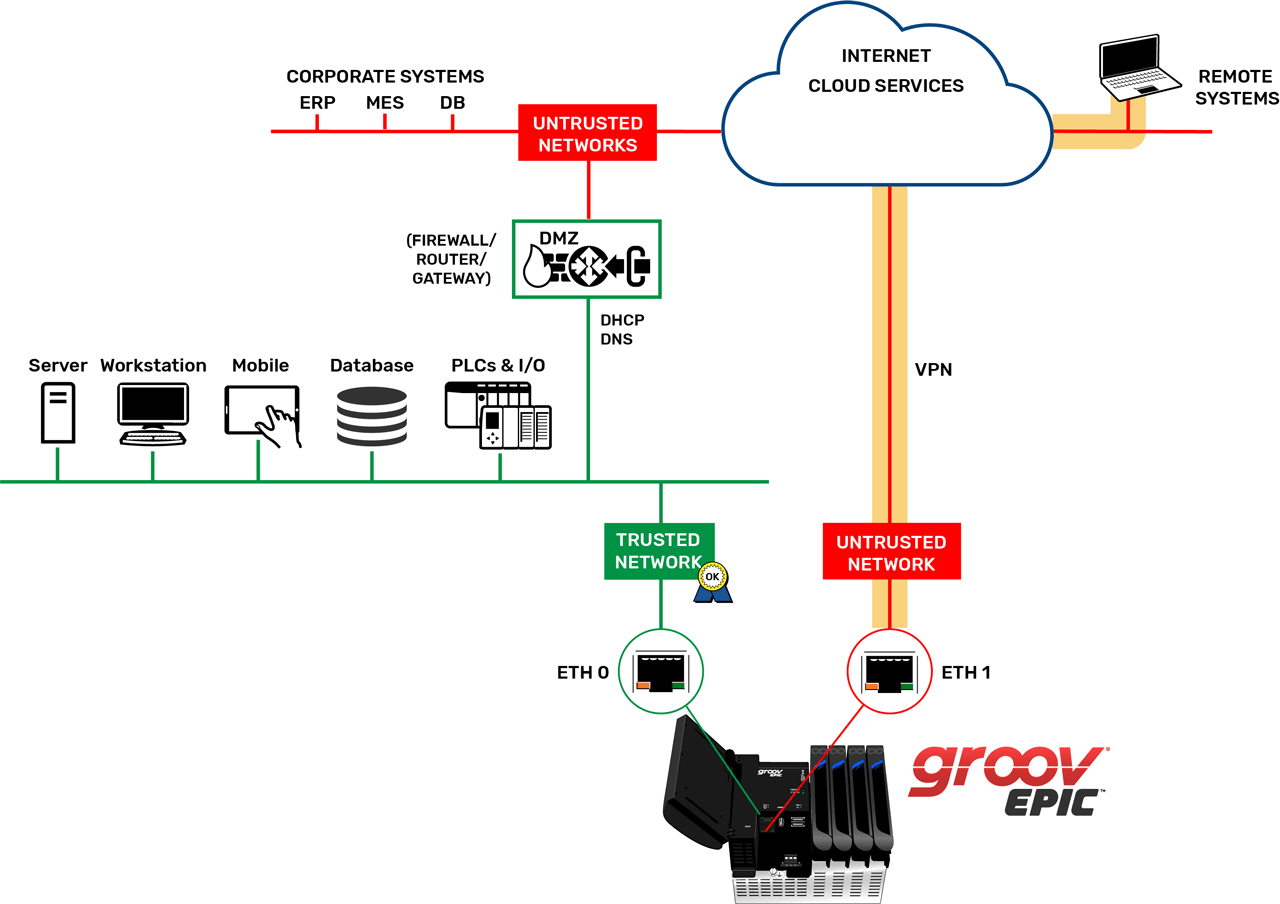
Offsite user can use software management tools to create secure VPN tunnels from the edge controller to externally configured VPN servers.
Virtual Private Networks
For offsite users, the system can be used to create secure VPN tunnels from groov EPIC to externally configured VPN servers or Opto 22 product support. If a user contacts product support for assistance, it’s possible to open a VPN tunnel so a product support engineer can temporarily access the device and help resolve the issue.
Security certificate management
Built-in certificate management provides a way that machines can identify themselves to other machines, so that when one machine tries to connect to another, it can be assured it’s communicating with the correct machine and not an impostor. The controller technology supports X.509 PKI standard certified connections to servers and from clients using SSL certificates, which can be device generated, self-signed, or registered publicly through a Certificate Authority (CA).
Data communication options
As noted in the Firewalls section, a device is inherently more secure and requires less security configuration when it initiates data communication on a port, rather than having to open a port to receive connection requests.
Publish/subscribe (pub/sub) is a communication technology that takes advantage of this greater security by using device-originated communications only. Controllers can use MQTT, a pub/sub protocol, to report status (authenticated and encrypted) to a central broker. Once connected to the broker, the connection persists, so the controller can also subscribe to any new commands for it or to status messages from other devices.
Because MQTT data flow is device originating, the firewall allows the data out, keeps track of the session status, and allows any packets coming back from the broker to pass through. With MQTT, this persistent connection acts as the critical mechanism for the MQTT broker to determine the state of client connections at all times. In a pub/sub model for supervisory control and data acquisition (SCADA) or industrial communications, users always want to be sure that clients are still connected. If a data publisher’s persistent connection is broken, the broker notifies all subscribers, so that the state of the system is known to all.
In contrast, in request/response communication, connections do not persist unless the client maintains them. For example, if Node-RED (a client) connects to a SQL server, once data is sent from the client to the server and the server responds, the connection is closed. Subsequent data transfers must be initiated by the client each time. Using the groov View software tool, the client’s browser keeps the connection open to the server (groov View) only as long as the client software is active.
Device-originated communication may be referred to as using an outbound port. When the device must open a port to receive communications originated from outside, it may be called an inbound port. Through outbound, device-originating data communications such as MQTT, the controller technology offers a secure option that requires far less configuration.
Security design for developers
The system’s design gives developers optional Secure Shell access (SSH) for developing custom applications, while maintaining security. Again, available tools help users design a secure system. A license is required to activate Secure Shell. Once users have the license, they can:
- Manage SSH access and restrict it to the trusted network only.
- Configure specific network interface ports on the controller firewall as required by custom applications.
- Install cryptographically signed packages from Opto 22’s git repository.
- Compile applications, monitor server log files, start and stop applications or services, and facilitate file transfers.
Best practices for security
Every application and situation is different and practitioners know best what access an application will need and what network architecture to use. However, as mentioned throughout this technical note, groov EPIC technology is designed to help create a secure system. Based on a specific application, users should keep these the following best practices in mind as they develop applications and deploy projects.
Networks
Best practices include:
- Configure the controller to use the ETH0 Ethernet network interface as a trusted network.
- Use ETH1 for any untrusted network. Configure exceptions in the system’s firewall only if required by the application.
- Configure the system’s firewall in groov Manage to close all unneeded network ports on all network interfaces.
Accounts - Have all users create long and difficult passwords, and instruct them not to write them down anywhere. Consider using a password manager where appropriate.
- Use a VPN if there is a requirement for remote unencrypted network connections over untrusted networks.
- To prevent unauthorized access to the groov EPIC processor, always log out of any account that has administrator privileges.
- When running the groov View HMI software on an external monitor, always put it in Kiosk mode so that only groov View is accessible.
Other best practices
If the system requirement is a completely closed system (for example, an OEM using the controller in a machine), after development is completed disable all ports in the firewall and unplug any Ethernet cables.
If someone attempts to connect an Ethernet cable to the controller to try to access the system from their computer, the ports will be closed and network access will be denied. Only an authorized user with administrator privileges can access groov Manage through the built-in display to reopen needed ports and gain network access.
Whenever possible, use authenticated and encrypted outbound, device-originated data connection methods. For example, use MQTT to publish data to an MQTT broker. Device-originated data communication methods help reduce open inbound network ports, eliminate man-in-the-middle exploits and prevent exposing sensitive credentials over the network.
Best practices for developers
If the system uses secure shell, configure SSH access with a unique and difficult username and password, different from groov Manage, groov View, or any other software running on the controller. Enable shell access only to configure and program the unit. Once the system is commissioned, disable shell access in groov software tools, so that no one else can get in. Never leave SSH access enabled once the system is in production.

