Industry NewsMarch 28, 2019
IoT security maturity model, practitioner’s guide released
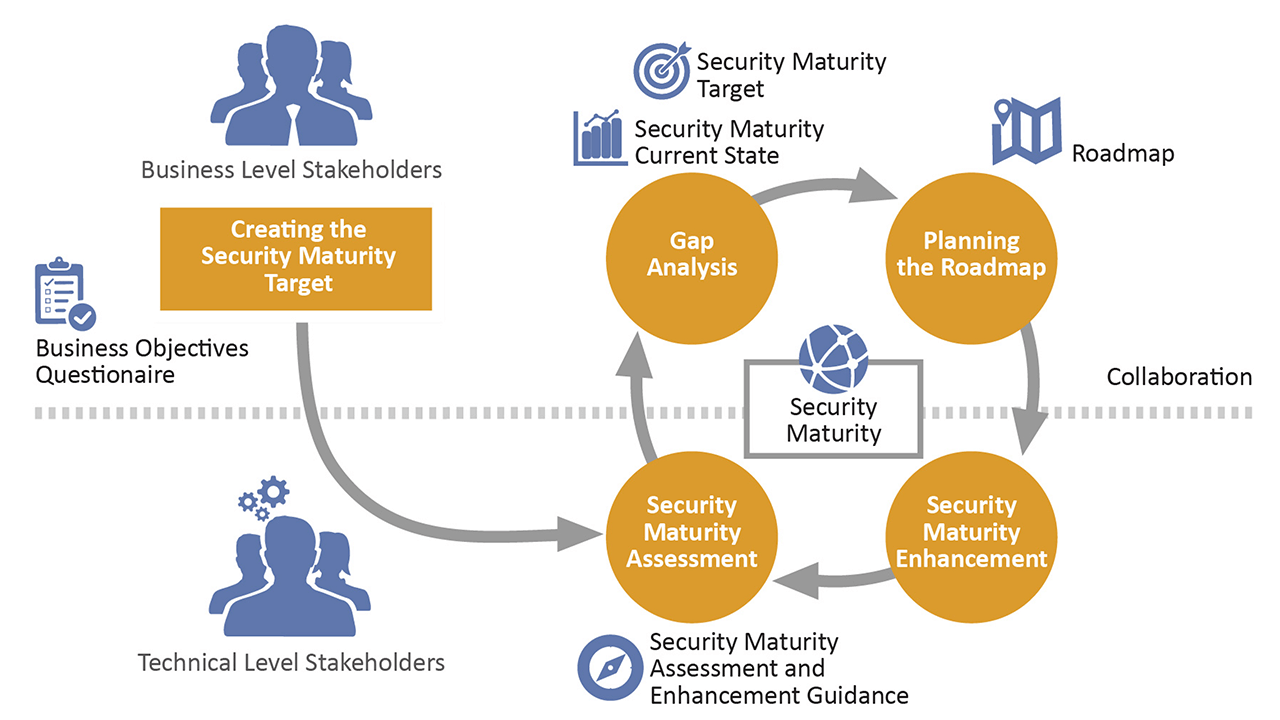
Security Maturity Model (SMM) Practitioner’s Guide provides detailed actionable guidance enabling IoT stakeholders to assess and manage the security maturity of IoT systems.
The Industrial Internet Consortium, now also incorporating OpenFog, has announced a Security Maturity Model (SMM) Practitioner’s Guide, which provides detailed actionable guidance enabling IoT stakeholders to assess and manage the security maturity of IoT systems.
Along with the publication of the SMM Practitioner’s Guide is an update to the IoT SMM: Description and Intended Use white paper, which provides an introduction to the concepts and approach of the SMM. This paper has been updated for consistency with the SMM Practitioner’s Guide, including revised diagrams and updated terminology.
As organizations connect their systems to the internet, they become vulnerable to new threats, and they are rightly concerned with security. Addressing these concerns requires investment, but determining investment focus and amount is a difficult business decision.
The SMM helps by enabling a structured top-down approach toward setting goals as well as a means toward assessing the current security state, taking into account various specific practices. The SMM allows an organization to trade off investment against risk in a sensible manner.
Building on concepts identified in the groundbreaking IIC Industrial Internet Security Framework published in 2016, the SMM defines levels of security maturity for a company to achieve based on its security goals and objectives as well as its appetite for risk. Organizations may improve their security state by making continued security assessments and improvements over time, up to their required level.
“This is the first model of its kind to assess the maturity of organizations’ IoT systems in a way that includes governance, technology and system management,” said Stephen Mellor, CTO, IIC. “Other models address part of what is addressed by the SMM; they may address a particular industry, IoT but not security, or security but not IoT. The SMM covers all these aspects and points to parts of existing models, where appropriate, to recognize existing work and avoid duplication.”
The practitioner’s guide includes tables describing what must be done to reach a given security comprehensiveness for each security domain, subdomain and practice and can be extended to address specific industry or system scope needs. Following each table is an example using various industry use cases to demonstrate how an organization might use the table to pick a target state or to evaluate a current state.
One example is that of an automotive manufacturer considering the possible threats interfering with the operations of a vehicle key fob. The manufacturer sets its target maturity comprehensiveness level to “1” as it considers some IT threats, such as a Denial of Service attack that may prevent a driver from opening the car door using the key fob. Over time, as new threats emerge, the manufacturer realizes it needs additional threat modeling and enhanced practices so raises its target maturity comprehensiveness level to a higher level “2.”
The practitioner’s guide contains three case studies that show IoT stakeholders how to apply the process based on realistic assessments, showing how the SMM can be applied in practice. The case studies include a smarter data-driven bottling line, an automotive gateway supporting OTA updates and security cameras used in residential settings.
SMM White Paper
According to the SMM white paper, the goal of the Security Maturity Model is to provide a path for Internet of Things (IoT) providers to know where they need to be and how to invest in security mechanisms that meet their requirements without over-investing in unnecessary security mechanisms. It seeks to help organizations identify the appropriate approach for effective enhancement of these practices where needed. Deciding where to focus limited security resources is a challenge for most organizations given the complexity of a constantly changing security landscape.
The audience for this document includes owners of IoT systems, decision makers, security leaders in various verticals, business risk managers, system integrators, architects, security assessors, analysts, policy and regulatory authorities, and other stakeholders concerned about the proper strategy for the implementation of mature security practices tailored to the needs and constraints of the specific IoT system.
The IIC has created the Industrial Internet Security Framework (IISF) to capture the information technology and operational technology dimensions of Industrial Internet of Things security and describes the security domains and techniques to address it.
It builds on the concepts of the Industrial Internet Reference Architecture (IIRA) and IISF and provides an additional dimension to the security techniques and mechanisms described in those documents. It also offers guidance as to which mechanisms are to be used and the maturity required to address specific IoT scenarios. All of these documents are available on the IIC website.


