TechnologyJanuary 3, 2026
2025 State of Industrial Cybersecurity Solutions

The current landscape of industrial cybersecurity technology solutions is rapidly evolving to meet the growing complexity and scale of cyber threats in smart manufacturing. In this special report, industry experts weigh in on the current state of affairs and how networking technologies and AI are strengthening security solutions.
BEST OF 2025
For our 2025 report on cybersecurity, the Industrial Ethernet Book reached out to industry experts to get their perspective on the trends driving new developments in industrial cybersecurity. A summary of these opinions illustrates a broad consensus on cybersecurity solutions. AI-driven threat detection is cited as a driving force along with use of “zero-trust” security architectures and advanced network segmentation. The result: integrated security spanning both the IT and OT domains.
IT-OT convergence is playing a role from advanced endpoint protection to OT-calibrated network monitoring. And industrial cybersecurity is also being reshaped by regulatory frameworks, the NIS2 Directive and Cyber Resilience Act (CRA), increasing the need for product standardization and international specifications. Read on to learn more.
AI technology driving new cybersecurity solutions
Solutions aim to keep up with the pace of innovation on the attackers’ side.
“Enhancements in artificial intelligence (AI) is currently the biggest driving force towards modern industrial cybersecurity solutions,” Andrew McPhee, Senior OT Security Solutions Manager at Cisco told IEB recently. “HackerGPT for example, is an AI tool created specifically for ethical hackers and research teams, but like anything else, it can be exploited by malicious actors. For example, if I present a CVE to HackerGPT, it can help build the code to exploit it. Industrial networks are known for being insecure, and now attackers don’t even need to understand how to code to create the perfect exploit.”
“The newest wave of industrial security solutions must keep up with the pace of innovation on the attackers’ side, and to combat AI threats, we need to figure out quickly how to use AI for cyber defense,” McPhee said.
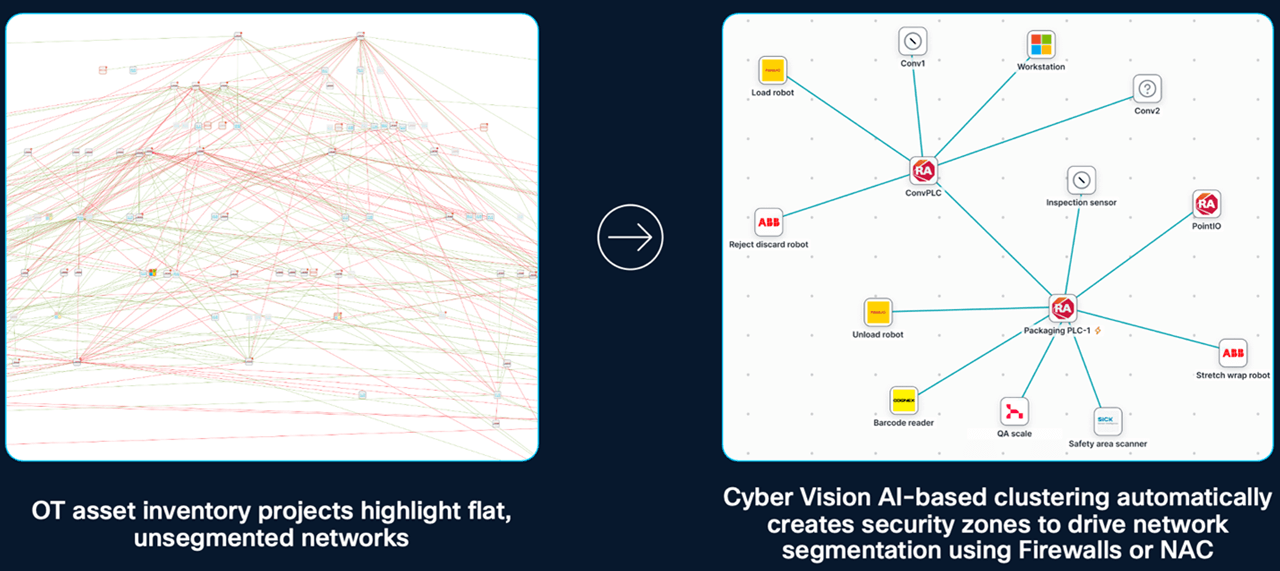
Smart manufacturing impact
He added that smart manufacturing networks have seen the rise of the industrial data center. What was once a server room located somewhere in the plant has now become a key compute environment for hosting critical applications as traditional operational workloads get virtualized and hosted in a traditional IT manner. This has led to tighter collaboration between IT and OT teams, who are required to deploy preventative solutions, not just threat detection.
New cybersecurity solutions offering preventative measures, such as creating a real time asset inventory and segmenting the network into zones and conduits, and ensuring secure remote access, make sure that if the “greenfield” elements of a plant network, for example a new body shop in a vehicle assembly plant were to be compromised, the impact of that does not cross into the rest of the assembly plant, the “brownfield” sectors. Additionally, having accurate and real-time visibility of the plant enables alerting on anomalous activities taking place, for example, a new unauthorized IoT device being added to the network, unusual device activity, or suspicious remote user activity.
Cybersecurity solutions
“Cybersecurity solutions produce a lot of data, across many different data sources, and trying to make sense of this data is difficult,” McPhee said.
Cisco Cyber Vision for example is embedded within Cisco Industrial Ethernet Switches which enables complete visibility coverage across the operational network. Switches connecting industrial assets also profile them, score their risks, and map their communication activities. However, this may result in observing thousands of devices, and even more communications. Pair that with the outcome for visibility driven segmentation, it becomes an operational nightmare.
AI promises to do many things, but one thing machines are great at doing is processing numbers and performing pattern recognition, and cutting-edge cybersecurity technologies should be using these advancements to process this vast amount of data and present it to the users in a form that is easily consumable. Cyber Vision as an example groups the communication data it observes in the industrial network and automatically organizes it into a “zones and conduit” model, which can be used as the starting point for a zero trust network segmentation project.
Applications
McPhee said that zero Trust is not a new model that in cybersecurity, but one that is becoming a reality for industrial networks. Organizations are taking the threat of remote access more seriously, replacing legacy remote access VPNs with zero trust network access (ZTNA) solutions to provide access to only the assets that are necessary, during a scheduled time window, and recording each session for auditing. ZTNA is also being enhanced with technology such as identity threat detection and response (ITDR) which provides insights if identities have been compromised. ITDR answers questions such as: is a user logging in from an unusual country, are they using a new device, are they logging in during irregular hours?
Zero Trust within the industrial network can also be realized with the implementation of the IEC62443 Zones and Conduits model. Visibility solutions such as Cyber Vision are being used as the starting point for a network segmentation project, helping organizations understand their existing communication patterns and make informed decisions on how to divide their network into logical zones of trust. These products then integrate into network access control (NAC) solutions such as Cisco Identity Services Engine (ISE), enabling segmentation to be driven by OT context. Using Cyber Vision to document assets that are part of each network segment helps drive collaboration between IT and OT teams. OT can leverage a user interface that understands the industrial process and IT gets pre-configured groups in their NAC. OT stays in control and IT enforces policies that will not disrupt production.
Industry challenges
“There is continuous skill shortage within the cybersecurity market, and even less of those people who have a deep understanding of the unique requirements faced by operational networks, McPhee said. “Cybersecurity is critical to protecting these networks, and the tools, techniques and guidance can often lead to a steep learning curve to implement them correctly. Organizations should turn to solutions, rather than products, to make sure each security capability that may be required – visibility, segmentation, remote access, identity and access management, SIEM, SOAR, etc. – can all operate as one cohesive solution. My advice is to focus on the outcomes, not on the latest buzzword in the security market.”

“One of the biggest trends changing industrial cybersecurity is zero-trust architecture. You stop assuming anything is safe, just because it’s inside your firewall. Every connection between devices should be authenticated and encrypted. When your HMI connects to your PLC, both sides should verify who they’re talking to,” — Dan White, Director of Technical Marketing, Opto 22.
Zero-trust architecture
All connections between devices should be authenticated and encrypted.
According to Dan White, director of technical marketing at Opto 22, “one of the biggest trends changing industrial cybersecurity is zero-trust architecture. You stop assuming anything is safe, just because it’s inside your firewall. Every connection between devices should be authenticated and encrypted. When your HMI connects to your PLC, both sides should verify who they’re talking to.”
“That level of verification is done using certificates—like checking IDs at both ends of the conversation. TLS encryption with proper certificate management protects data everywhere it travels. You’re not just using passwords that can be guessed or stolen. Each device has its own cryptographic certificate that proves its identity. Even if someone intercepts your data, they can’t read it or pretend to be your equipment,” White said.
Edge-originated, outbound-only communications solve another huge cybersecurity problem. Instead of external systems reaching into your networks and controllers to pull data, your edge devices push data out when it’s ready. You publish data through MQTT Sparkplug B to whoever needs it, but nobody can reach back in to mess with your controls. Your equipment becomes impossible to hack remotely because it doesn’t accept incoming connections.
Technology solutions
“You’re trying to protect your plant without slowing down operations or making life harder for your operators and maintenance team. But smart manufacturing depends on sharing data between systems. Zero-trust architecture and edge-originated communications help make it safer to share that data,” White added.
White said that zero-trust with proper certificates means you know exactly what’s talking on your network. That temperature reading from Tank 1? You know it actually came from Tank 1’s sensor, not from someone spoofing data to cause problems. Your operators can trust what they see on their screens because every piece of data is cryptographically verified.
Edge-originated communications give you a huge benefit; your control systems keep running even if your IT network gets compromised. Since your PLCs and edge controllers only push data out through MQTT Sparkplug B, attackers can’t reach in to change setpoints or force outputs. When that ransomware attack hits the front office, your production lines don’t even notice. Outbound-only publishing makes the difference—your MES gets production data without having any ability to control equipment.
MQTT Sparkplug B
According to White, the MQTT Sparkplug B with TLS reduces network traffic and helps secures data. The MQTT publish/subscribe architecture eliminates polling noise that clogs industrial networks. Instead of hundreds of clients asking a controller “what are your values?” every second, devices publish data only when values change. You cut network traffic by 90% or more compared to traditional poll/response protocols like OPC UA or Modbus/TCP.
When an edge controller comes online, it publishes data with a birth certificate that defines every tag, its data type, and its engineering units. Subscribers to that data know exactly what they’re getting and get only what they need. The TLS layer encrypts everything and verifies certificates at both ends. Even if someone taps the network, they see only encrypted gibberish.
These cybersecurity technologies work for both greenfield and brownfield applications. For legacy equipment that can’t handle these modern, cybersecure communications, edge gateways create secure proxies. Your 20-year-old PLC talks normal Modbus to the gateway. The gateway then wraps that data in encrypted, authenticated MQTT Sparkplug B messages. You get modern security without touching working control logic.
Applications
“You face different security challenges depending on your industry. Here are some industries where modern cybersecurity solutions make the biggest difference,” White said.
Water and wastewater systems have remote sites everywhere—lift stations, pump houses, treatment plants miles apart. Edge controllers with MQTT Sparkplug B and cellular connections securely handle remote installations. Each remote site publishes its data outbound through encrypted channels. Nobody can hack in through the cellular connection because the device doesn’t accept incoming connections. You monitor everything centrally while each site stays protected.
Oil and gas operations need to protect both pipeline SCADA and refinery controls. Zero-trust architecture helps here because you stop trusting devices just because they’re on your OT network. Every flow computer, every RTU, every control valve actuator must authenticate itself. When contractors bring in equipment for maintenance, it can’t talk to your systems without proper certificates.
Digital transformation and Unified Namespace (UNS) projects create new security challenges. You’re connecting hundreds of diverse machines—different ages, brands, protocols—into a single data architecture. Edge devices with certificate-based MQTT become your security layer. Each machine publishes to your UNS through encrypted channels while legacy equipment stays protected behind edge gateways. Your 1990s equipment joins your Industry 4.0 initiative without compromising security.
Engineering challenges
“Your biggest worry when adding cybersecurity? Breaking something that works. Your 20-year-old PLC runs perfectly. You can’t risk production downtime to add security features it wasn’t designed for. Modern edge gateways resolve this worry—they sit beside your existing equipment, monitoring and securing communications without touching your control logic,” White added.
He added that legacy equipment creates real headaches. Older devices don’t support certificates or encryption. They speak over serial networks or use Modbus/TCP and other protocols that have no built-in security. But edge devices with built-in protocol translation can speak to your old equipment and publish data securely on your network using encrypted MQTT Sparkplug B communication. Your legacy gear stays untouched while gaining modern security protection.

“The dominant trend in the adoption of industrial cybersecurity solutions is IT and OT convergence. The increasing interconnectivity of IT and OT networks and the growing coordination between traditional IT security teams and the OT security team or process control team has allowed for a range of sophisticated cybersecurity solutions,” — Patrick O’Brien, safety and cybersecurity engineer, exida.
Impact of IT-OT Convergence
Increasing interconnectivity of IT and OT networks.
“The dominant trend in the adoption of industrial cybersecurity solutions is IT and OT convergence. The increasing interconnectivity of IT and OT networks and the growing coordination between traditional IT security teams and the OT security team or process control team has allowed for a range of sophisticated cybersecurity solutions that would have been impossible for all but the most mature sites to implement 10 years ago from advanced endpoint protection to OT calibrated network monitoring solutions,” said Patrick O’Brien, safety and cybersecurity engineer at exida.
O’Brien added that, within cybersecurity solutions, the buzzword of AI is being incorporated into every marketing brochure and presentation. With all of the claims being made about AI it is important to separate the noise from the new ground. AI has a number of different sub-categories that are often confused or mis-represented. Some categories like supervised machine learning have been incorporated into common security solutions for years and are undergoing a rebranding effort to highlight that they are part of the AI boom, while in some technologies and platforms newer advances like unsupervised machine learning and Generative AI support tools for users are being implemented.
Technology benefits
“When machine learning is applied for a cybersecurity solution from anti-virus/ endpoint protection to network monitoring (whether it is a network monitoring solution, SIEM, or Security Operations Center (SOC)) the primary benefit is the ability to make inferences beyond the known data set,” O’Brien said. “For anti-virus software it is limited based on the frequency of virus table updates (and compatibility with the control system in use) and may go months to years without ever being updated.”
This greatly reduces the effectiveness of the control as the solution will not be able to identify newer strains, and even the most diligently updated system is unable to detect novel strains. The hope with incorporating machine learning is that the systems will be much more robust for detecting new variants that have yet to be incorporated into the virus table.
On the network monitoring side, he said that one of the primary challenges with traditional network monitoring solutions and SIEMs is the sheer volume of data and alerts being collected. We have worked with sites who are very proud of their state-of-the-art solution, only to quickly find that they are overwhelmed with a high volume of alerts for normal activity, making it challenging to identify where a real threat may exist. Security Operations Centers (SOCs) with dedicated and competent security analysts helps to address some of these concerns, but better event correlation and tuning will help to further manage the load of information being collected and highlight the scenarios that require response actions.
Machine learning impact
“Understanding the different categories of AI being used in cybersecurity solutions is key to communicating the benefits effectively. For this discussion we will group technologies into three categories: supervised machine learning, unsupervised machine learning, and Generative AI,” O’Brien added.
Machine learning particularly supervised machine learning has been implemented for tasks like malware identification and intrusion detection systems for years. Supervised machine learning excels at identifying patterns from large data sets which makes it a good choice to identify new malware variants based on similarities to previous malware variants or common characteristics or identifying suspicious traffic patterns.
Using unsupervised machine learning or a hybrid model (combination of supervised and un-supervised) is human behavior analytics that are sometimes incorporated into a System Information and Event Management system. Unlike malware design, human behavior changes over design and can vary significantly in the realm of “usual” site support for industrial facilities making it much more difficult to discern the malicious from the benign. The final area where AI is being incorporated into cybersecurity solutions is the use of Generative AI in cybersecurity platforms to provide a new user interface that is easier to query ask for trends and access the massive amounts of data being collected in a more user-friendly way.
The computing power for the further analysis of event logs and traffic patterns using machine learning (particularly unsupervised) is almost never done directly in the factory environment instead collectors are deployed to gather the information from the factory network and communicate out to the business network or cloud platform. Correctly configuring and deploying the cybersecurity solution to function as intended without negatively impacting operations is one of the key challenges facing automation engineers with these new technologies.
Applications
‘For the application of machine learning, we have seen this become a focus for almost every cybersecurity solution including anti-virus/ endpoint protection, network monitoring, SIEMs, and SOCs. The ability to more effectively detect unusual or malicious activities in fundamental to many cybersecurity protection technologies and is a natural fit,” O’Brien said.
For Gen AI the deployment has been a bit broader in what areas it can support. Ultimately Gen AI is providing a new easier way for security analysts to access information with the goal of lightening the load on existing security analysts to complete the many tasks necessary for achieving security. This could take the form of making it easier for them to interrogate the information collected by the SIEM to understand related event logs that tie back to the same incident to asking their security platform to generate report out on security metrics. Any time intensive manual task for security engineers is a prime candidate for Gen AI to address when implemented at the platform level, and many organizations are viewing this as the way forward for achieving better visibility and maintainability in their security program overall.
Engineering challenges
For all industrial facilities, O’Brien said that the number one priority is maintaining the safety and availability of the facility. Because of this once a control system and site network is reliably running many automation engineers are very hesitant to make changes. Certain technologies like Intrusion Prevention Systems (IPS) or automatic anti-virus updates or patch deployment which are commonly employed in IT systems would be a non-starter for many industrial sites. In some cases, even network monitoring or SIEM systems which are not supposed to have a very limited impact on network communications load have actually led to loss of availability of certain devices or in one case a trip of the production network due to misconfiguration.
Additionally, automation engineers are often overloaded with the ongoing maintenance and support activities for the site, and dedicating even 4 hours a week solely to cybersecurity can be a challenge.
“This is where IT/OT convergence can be a significant advantage. If the combined cybersecurity team has a common understanding of the objectives for security in the industrial site (safety and availability first), the knowledge and experience of the IT team with these technologies and solutions can be a great help in correctly configuring and deploying the solution,” O’Brien concluded.

“Cybersecurity is a problem that industrial equipment operators have to address whether it is because of attacks against industrial installation or government regulation such as the EU CRA. Deploying a secure system can be expensive and there is a need to control costs by managing the security configuration of factory networks using centralized tools based on open standards,” — Randy Armstrong, Chair of the OPC UA Security Working Group.
OPC UA Standard APIs
Implementing factory networks using centralized tools based on open standards.
Randy Armstrong, Chair of the OPC UA Security Working Group, said that “cybersecurity is a problem that industrial equipment operators have to address whether it is because of the increasing number of attacks against industrial installation or government regulation such as the EU CRA. However, deploying a secure system can be expensive and there is a need to control costs by managing the security configuration of factory networks using centralized tools based on open standards. OPC UA defines standard APIs that are suited for this purpose.”
OPC UA standard APIs
OPC UA defines standard APIs for security configuration that allows equipment from different vendors to be centrally managed by an off-the-shelf security management service designed to run locally on the factory network. This service ensures the security of all devices is kept up to date and adapts to changes in the factory environment. OPC UA greatly reduces the cost of deploying secure solutions by reducing the need for human administration and not forcing the factory operator to commit to a proprietary, single vendor solution.
“Modern security requires the management of public key infrastructure (PKI) which is used to distribute certificates to devices and applications,” Armstrong said. “The certificate allows them to authenticate themselves when connecting to other applications. The OPC UA standard is being deployed in factories around the world to automate management PKI during initial set up and while the factory is operating.”
The OPC UA certificate management APIs are suitable for any manufacturing environment that has devices communicating over TCP/IP based networks.
Engineering feedback
“The feedback the OPC Foundation has gotten is the cost of managing PKI is a major barrier to adoption of the modern cybersecurity practices. OPC UA provides an open standards-based solution that allows factory operators to manage the PKI in the factory without being locked into expensive single vendor solutions,” Armstrong said.
He added that another concern is the need for access to cloud base systems that a lot of IT centric systems require. The OPC UA model presumes that the management service is running locally within the factory network and only needs to manage the devices on the local network.

“The EU Cyber Resilience Act (CRA) mandates cybersecurity requirements for all products with digital elements. This includes any hardware or software that processes digital data and connects to other digital systems. The extensive scope of CRA covers IT, IoT, industrial control systems (OT), embedded devices, machinery, and more,” — Dr. Al Beydoun, ODVA President and Executive Director.
CRA cybersecurity standards
Global impact due to product standardization and international specifications.
According to Dr. Al Beydoun, ODVA President and Executive Director, “the EU Cyber Resilience Act (CRA) mandates cybersecurity requirements for all products with digital elements. This includes any hardware or software that processes digital data and connects to other digital systems. The extensive scope of CRA covers IT, IoT, industrial control systems (OT), embedded devices, machinery, and more.”
Starting December 11, 2027, any digital product sold in the EU must adhere to the cybersecurity standards set by CRA. Even earlier, on September 11, 2026, manufacturers must have a process in place to report vulnerabilities and security incidents for their digital products. To indicate compliance, manufacturers must apply the CE mark, a certification already recognized for ensuring safety in various products.
“This standardized approach aligns cybersecurity regulations across the EU, integrating digital products into existing harmonization laws. While this regulation doesn’t cover all world areas, it’s likely that the CRA will have a substantial global impact because of product standardization and international specifications,” Beydoun said.
Industrial cybersecurity solutions
“For most digital devices and software, companies can conduct their own assessments to confirm compliance. Most products incorporating Common Industrial Protocol (CIPTM) technologies will fall into this lowest risk category, allowing manufacturers to apply the CE marking independently,” Beydoun said.
However, products with higher security risks (defined as Important Class I or Important Class II within CRA) must meet specific harmonized standards, and the most critical category (defined as Critical within CRA) will require independent third-party evaluation before being approved for sale. By December 11, 2027, every digital product made available in the EU must adhere to the CRA, regardless of when it was originally developed or launched. This includes both existing products on the market and products available after that date. Harmonized standards are expected to be developed to support CRA implementation.
Technology innovations
Beydoun added that, starting December 11, 2027, manufacturers of industrial Ethernet devices, including EtherNet/IP products, will need to adhere to documentation, development practices, and cybersecurity measures to comply with the EU CRA.
Manufacturers and vendors bear full responsibility for ensuring that Technical Documentation, End-User Documentation, and Secure Development Practices are integrated into the secure product development lifecycle. These processes must be tailored to the specific product, department, manufacturer, the product’s intended use, and the company’s development framework.
Regarding Vulnerability Management Requirements, the primary responsibility lies with the product manufacturer. Each vendor must establish a structured process for vulnerability reporting, management, disclosure, and the distribution of security advisories and updates. For vulnerabilities related to CIP technologies, ODVA has developed a vulnerability management framework that aligns with CRA requirements, ensuring that any identified weaknesses are addressed and disclosed appropriately.
While most of the CRA’s 13 cybersecurity requirements (listed in Annex I, Parts 1 and 2) apply directly to product design and fall outside the scope of CIP technologies, four specific requirements are influenced by CIP technologies. In all cases, CIP Security, an EtherNet/IP network extension, leverages widely adopted security standards such as TLS and OpenID Connect, as well as proven encryption algorithms.
Key CRA Requirements Addressed by CIP Security
Secure by Default (Annex I, Part 1, 2b) Requirement: CIP Security Contribution: The CIP Security Pull Model is designed to function automatically by default. Devices implementing this model can independently locate a certificate authority and request provisioning certificates. Once deployed, all security configurations can be automatically retrieved from a server and applied to the device. Furthermore, devices must have non-TLS/DTLS ports disabled by default. End users may enable these non-secure EtherNet/IP ports later, based on their risk assessment, using the TCP/IP Interface Object. Port 44818/UDP, used for ListIdentity, can likely remain open by default, as it is solely intended for device identification purposes.
Protection Against Unauthorized Access (Annex I, Part 1, 2d) Requirement: CIP Security Contribution: CIP Security offers multiple layers of protection against unauthorized access. The EtherNet/IP Confidentiality Profile supports authentication via both certificates and pre-shared keys, using mutual TLS. Additionally, for enhanced security, the CIP Security User Authentication Profile enables Role-Based Access Control and allows integration with external identity providers.
Confidentiality of Transmitted Data (Annex I, Part 1, 2e) Requirement: CIP Security Contribution: CIP Security ensures secure data transmission using TLS and DTLS protocols, requiring AES encryption – a globally trusted standard. Users can configure cipher suites based on security needs, though all CIP Security-compliant devices must support confidentiality measures. While CIP Security secures data in transit, encryption for stored data falls under the manufacturer’s responsibility.
Integrity of Transmitted Data (Annex I, Part 1, 2f) Requirement: CIP Security Contribution: Data integrity within CIP Security is ensured through TLS and DTLS, with all cipher suites defined by CIP Security incorporating strong integrity protections via SHA-based HMACs. Additionally, specific data elements – such as digital certificates and access tokens – are further protected using digital signatures. While CIP Security provides robust integrity measures for data in transit, ensuring data integrity at rest is the manufacturer’s responsibility.
Engineering challenges
Beydoun said that the CRA introduces comprehensive cybersecurity regulations for digital products in the EU, requiring compliance by December 11, 2027. Covering a broad range of products and markets including Operations Technology (OT), the CRA mandates strict security standards, vulnerability management processes, and robust documentation practices. Manufacturers are responsible for implementing secure development processes, maintaining technical and end-user documentation, and ensuring proper vulnerability handling mechanisms.
“For CIP products, including EtherNet/IP, compliance with CRA requirements is critical,” Beydoun said. “CIP Security helps meet key regulatory obligations by leveraging industry standards like TLS, OpenID Connect, and strong encryption protocols. Specifically, CIP Security enhances protection against unauthorized access, ensures secure data transmission, and supports integrity mechanisms, aiding manufacturers in meeting CRA’s cybersecurity mandates. As the enforcement date approaches, companies must proactively align their cybersecurity frameworks with CRA requirements to maintain market access and enhance digital resilience across industrial automation and connected systems.”
For more details, download the CIP Security: A Valuable Tool for CRA Compliance white paper: https://www.odva.org/technology-standards/distinct-cip-services/cip-security/

“AI and automation are two of the most prominent technology trends that are driving the newest industrial cybersecurity solutions. Most manufacturers, 95%, have either already invested in AI or plan to in the next five years. As AI is being used to improve security posture, the same technology is also being used by attackers to automate intrusions and evade detection,” — Natalie Kalinowski, OT Cybersecurity Consultant, Rockwell Automation.
Impact of AI and Automation
Technologies driving the newest industrial cybersecurity solutions.
“AI and automation are two of the most prominent technology trends that are driving the newest industrial cybersecurity solutions,” Natalie Kalinowski, OT Cybersecurity Consultant at Rockwell Automation told IEB recently.
Kalinowski said that most manufacturers, 95%, have either already invested in AI or plan to in the next five years. As AI is being used to improve security posture, the same technology is also being used by attackers to automate intrusions and evade detection. As a result, companies are increasingly testing this technology to catch unusual device activity or predict when a vulnerability might become a serious issue. AI is also being implemented to take over tedious, repetitive monitoring tasks, letting security teams focus on higher value tasks.
“Another trend driving the newest solutions is accelerated IT/OT convergence,” Kalinowski said. “By blending IT’s ability to handle data with OT’s focus on operations, companies are finding ways to work smarter, faster and more efficiently. But this growing integration expands the attack surface and opens the door to new cybersecurity vulnerabilities. However, real-time monitoring tools can help teams catch issues early and minimize them before they cause significant disruptions.”
Critical infrastructure operators have increasingly adopted cloud-connected systems — such as analytics platforms, remote monitoring tools and supply chain management platforms — to stay competitive. However, as operations adopt hybrid architectures, we’re seeing threat actors pivot from traditional IT infiltration to abusing misconfigured cloud access, remote connections and weak credential controls. This is a massive operational risk, and it’s only continuing to accelerate. The assumption that cloud environments are secure by default is a dangerous one, especially when attackers are “logging in” instead of “breaking in.” These aren’t just IT problems anymore. When attackers move laterally from compromised cloud credentials into operational networks, we’re talking about potential impacts on safety systems and process control.
Cybersecurity solutions
“Industrial cybersecurity solutions aren’t just about protection,” Kalinowski added. “They help enable smart manufacturing at scale. Since many manufacturers rely on legacy systems that weren’t designed for today’s modern cyber threats, they’re often prime targets for threat actors that can cause financial burdens, pose health and safety risks and contribute to downtime. Industrial cybersecurity solutions can help detect threats in real-time, quickly deploy patches and decrease downtime.”
Additionally, they can assist with obsolescence planning projects where operational environments can use risk prioritization to identify key areas for modernization projects to update and secure their infrastructure. According to a recent State of Smart Manufacturing report, 53% of manufacturers cite that securing OT assets is one of the primary reasons for investing in AI, and more than half of respondents are already adopting security at-scale. This digital transformation shift recasts security leaders as growth enablers. Hardened networks can also help serve as the foundation for predictive maintenance, helping reduce risk and protect revenue from costly impacts.
Industrial cybersecurity solutions allow for secure remote access for third-party and internal use, network segmentation to limit attack surfaces and security monitoring and response. Manufacturers are also embedding security into hardware as a standard practice, enabling layered, robust security measures that minimize risk and bolster resiliency. Solutions have evolved to meet the modern threat landscape. Where it used to be about locking down the perimeter, it’s now about real-time threat intelligence across a distributed infrastructure.
Newer solutions can also translate cyber scenarios into financial terms to support data-driven decision-making. Executives and the insurance agencies that underwrite their risk now expect precise metrics. Security leaders can use these advanced solutions to translate the technical vulnerabilities into business terms so executives can weigh cybersecurity spending against other capital priorities.
Impact on operational technology
“Industrial cybersecurity solutions are specifically unique to industrial and operational technology (OT) environments, designed for the specific realities of the factory floor without focusing on repurposing specialized IT tools,” Kalinowski said. “This OT specialization helps these solutions integrate seamlessly with existing infrastructure and reduce implementation challenges. Not to mention, most typical IT security tools can’t fully solve the challenges and threats that are present in OT environments.”
By implementing cybersecurity solutions that combine secure-by-design principles, network segmentation and real-time threat detection, organizations can protect critical assets without disrupting production. Real-time monitoring and threat visibility help industrial organizations receive a detailed look into all of their connected assets, helping to prioritize risks as well as identify and respond to key vulnerabilities. This real-time insight also helps organizations quickly respond to security threats and address resource gaps and operational inefficiencies.
Often, industrial organizations are understaffed, overwhelmed by alerts and struggling to make sense of what’s actually happening across increasingly connected environments.
Security monitoring and response solutions can provide alert optimization and response guidance. By ingesting a wide range of data sources including behavioral analytics and correlation, OT-specific logic can help detect true positives and suppress the noise. When bolstered by the expertise of a trusted partner, newer cybersecurity solutions can go beyond just detection, delivering a clear, contextualized response plan that helps internal teams act quickly and effectively.
Applications
These solutions are targeting several areas in OT environments and are helping to minimize the increased cyber risks in multiple industries, including critical infrastructure, automotive, food and beverage, consumer packaged goods, and more. The newest solutions help these organizations focus on centralizing asset inventory, correlating configuration data and assessing network segmentation. As a result, they can uncover high-risk paths from IT into OT, move toward implementing mitigation steps such as secure remote access controls and network segmentation.
“Solutions are also applied to offer plants automated patching, centralized alerting and improved endpoint visibility. The improvements help to bolster defenses against a range of modern risks, including those associated with cloud-based services, remote access and identity management,” Kalinowski said.
“Additionally, by monitoring sensors and production, companies can free their information from “functional silos,” detect anomalies and threats and contain cyber incidents before they compromise the entire supply chain. Frequent asset inventory audits help secure operations and preserve product quality and safety.”
Addressing engineering challenges
When implementing industrial cybersecurity strategies, Kalinowski said that one of the major concerns companies are facing is gaining comprehensive asset visibility. On the factory floor, there are many devices in play, some that may be hard to spot right away. Limited visibility makes it hard to protect all assets. This can slow or complicate the deployment of cybersecurity strategies. Without a comprehensive map, troubleshooting a suspected breach feels like searching for a single misplaced bolt in a vast warehouse.
In plenty of plants, older machines still serve as a backbone for production. Unfortunately, those same systems may also be the least prepared to deal with modern cyber threats. They were built for stability, not for advanced security. This can bring inherent compatibility issues and complicate integrating industrial cybersecurity solutions, all while trying to keep systems up and running. You can’t simply tack on encryption or multi-factor authentication if the hardware isn’t equipped to handle it.
“Bridging the IT/OT divide is also a concern, as IT pros see the world through data confidentiality and software patches and OT teams focus on uptime, worker safety and consistent production,” Kalinowski said. “It’s not hard to see how these differing viewpoints might clash. A quick software patch might be child’s play for IT, but a single system reboot can halt an entire production line on the OT side. Without a shared language or framework, both sides might struggle to coordinate on a response plan for potential attacks.”
“The convergence of Information Technology (IT) and Operational Technology (OT) is a rapidly evolving trend in the industrial sector. As companies increasingly look for ways to optimize their operations and improve efficiency, the need for seamless communication between traditionally separate systems becomes paramount,” — Michael Metzler, Vice President, Horizontal Management Cybersecurity for Digital Industries, Siemens.
IT-OT Convergence
AI-driven threat detection, zero-trust architectures, advanced network segmentation.
According to Michael Metzler, Vice President, Horizontal Management Cybersecurity for Digital Industries at Siemens, “the convergence of Information Technology (IT) and Operational Technology (OT) is a rapidly evolving trend in the industrial sector.”
“As companies increasingly look for ways to optimize their operations and improve efficiency, the need for seamless communication between traditionally separate systems becomes paramount. It lays the foundation for data-driven decision making,” Metzler told IEB recently. “The integration of IT and OT systems requires a robust communication infrastructure that can handle the demands of both realms.”
Current technology trends in industrial cybersecurity include the increased adoption of AI-driven threat detection, zero-trust architectures, and advanced network segmentation. To this end, Siemens – a major supplier for industrial cybersecurity – is offering solutions that offer real-time monitoring, automated response capabilities, and enhanced visibility across both IT and OT environments. These solutions are designed to be scalable, allowing companies to protect both modern and legacy systems without significant overhauls.
Technology impact
Metzler said that industrial networks are the nerve pathways in production – they are becoming in sum ever more complex. Hardware alone no longer determines their performance. Software-based network management and the use of cybersecurity tools have become indispensable.
New industrial cybersecurity solutions offer several benefits, including improved threat detection, reduced response times, and enhanced protection against both internal and external threats. These solutions can significantly reduce the risk of costly downtime due to cyber incidents, thereby improving overall operational efficiency. The potential impact on manufacturing networks is substantial, as these solutions enable a more resilient and secure production environment, which is crucial in an era of increasing cyber threats.
“The risk of cyberattacks on industrial plants is real – and the frequency continues to increase. To comprehensively protect industrial plants against cyberattacks from inside and outside, all levels must be addressed simultaneously – from the operational to the field level, from data protection to secure communication,” Metzler said. “With Defense in Depth, Siemens provides a multi-layered security concept that offers industrial plants comprehensive and far-reaching protection in accordance with the recommendations of the international IEC 62443 standard.”
It is aimed at plant operators, integrators and component manufacturers and covers all relevant aspects of industrial cybersecurity. Cutting-edge cybersecurity technologies in industrial environments are characterized by their ability to seamlessly integrate with existing systems, including legacy OT devices. Technologies such as machine learning-based anomaly detection, industrial firewalls with deep packet inspection, and secure remote access solutions are being applied in factories to provide real-time threat detection and automated incident response. What makes these technologies unique is their focus on the specific needs of industrial environments, where uptime and safety are paramount.
Application targets
Metzler said that the newest industrial cybersecurity solutions are specifically targeting areas such as critical infrastructure protection, secure remote access for industrial control systems, and the protection of industrial IoT devices. These solutions are also being applied to ensure compliance with stringent regulatory requirements and to safeguard sensitive production data.
“With the increasing convergence of IT and OT, traditional defense concepts are increasingly reaching their limits. Software-based network management and the use of cybersecurity tools have therefore become indispensable,” Metzler said.
To be able to detect potential vulnerabilities in OT networks at any time, Siemens has designed a complementary tool set for plant operators with the SINEC software family. The SINEC Security Inspector determines the security status of individual components or entire production networks. The SINEC Security Monitor analyzes network traffic and detects anomalies through passive, non-intrusive continuous security monitoring. One of the newest tools in the SINEC portfolio is the SINEC Security Guard, an intuitive cloud-based software-as-a-service that displays vulnerabilities for OT-Assets and enables optimized security management for industrial operators without dedicated cybersecurity expertise. The SINEC NMS network management system also enables centralized monitoring and configuration of networks as well as security through encrypted data communication and local documentation.
Focus on OT
Metzler said that the special framework conditions in Operational Technology (OT), including continuous operation, high performance requirements, and availability, demands an in-depth understanding of industrial processes so that security concepts can be optimally introduced and implemented. For many companies, this task has become too complex. They need a partner who is familiar with and has mastered the special requirements of industry and cybersecurity.
When implementing industrial cybersecurity strategies challenges include protecting legacy systems that were not originally designed with cybersecurity in mind, ensuring the secure integration of IT and OT (Operational Technology) networks, managing the growing complexity of industrial networks, and addressing the shortage of skilled cybersecurity professionals. C Additionally, companies must ensure that all components, including new and legacy devices, are equipped with robust security functionalities. This includes implementing technologies like industrial firewalls, intrusion detection systems, and secure remote access solutions that are specifically designed for industrial environments. Companies must also balance the need for robust security with the requirement for minimal disruption to production processes and safety systems.
“Beyond technology, the correct handling of cybersecurity measures by personnel is crucial,” Metzler said. “This involves training staff to adhere to defined policies and procedures, such as incident response protocols and regular security audits. A lack of cybersecurity awareness or poor adherence to security protocols by employees can undermine even the most advanced technical defenses. Overall, the shortage of skilled cybersecurity professionals presents a challenge, making it essential for companies to not only invest in technology but also in ongoing training and education for their workforce.”

“The industrial cybersecurity landscape is being reshaped by regulatory frameworks such as the NIS2 Directive and the Cyber Resilience Act (CRA). These initiatives drive companies to adopt security-by-design principles, integrate real-time vulnerability management, and enforce supply chain security,” — Thomas Rummel, Managing Director, Softing Industrial Automation GmbH.
NIS2 Directive and Cyber Resilience Act
Industrial cybersecurity landscape being reshaped by regulatory frameworks.
Thomas Rummel, Managing Director at Softing Industrial Automation GmbH, told IEB that “the industrial cybersecurity landscape is being reshaped by regulatory frameworks such as the NIS2 Directive and the Cyber Resilience Act (CRA).”
“These initiatives drive companies to adopt security-by-design principles, integrate real-time vulnerability management, and enforce supply chain security. Another major trend is the adoption of the IEC 62443 standard, which provides structured, risk-based security for automation systems,” Rummel said. “Technological enablers include network segmentation, secure communication protocols, and identity and access management. Vendors are also increasingly embedding long-term update mechanisms into IIoT devices to ensure resilience. Collectively, these trends reflect a shift from reactive to proactive security strategies, designed to align IT and OT teams and ensure compliance across global supply chains.”
Industrial cybersecurity solutions
Rummel said that the latest industrial cybersecurity solutions bring multiple benefits for smart manufacturing. First, they enhance operational resilience by reducing the likelihood of successful cyberattacks through network segmentation and encrypted communications. Second, they increase visibility into industrial assets.
For example, Softing’s plantPerfect Monitor enables real-time inventory of devices and firmware, which is essential for patch management and regulatory compliance. Third, they strengthen supply chain trust by enforcing standardized security processes, making collaboration easier across global supply chains. The impact on smart manufacturing is substantial: more secure networks allow for the safe integration of IIoT and cloud analytics, thereby supporting efficiency, predictive maintenance, and data-driven optimization.
“Ultimately, cybersecurity is no longer just a defensive measure but an enabler of digital transformation,” Rummel said.
He added that cutting-edge industrial cybersecurity solutions are characterized by their integration into core automation systems. One example is Softing’s smartLink HW-PN, which provides a secure access point to PROFINET networks. The device ensures segmentation by isolating higher-level application networks from field-level devices, while using OPC UA with certificates for encrypted and authenticated communication. What makes them unique is the balance between OT integration and adherence to IT security principles, ensuring that cybersecurity does not hinder but rather facilitates operational performance.
Application areas

Softing’s smartLink HW-PN allows for secure parameter setting and state monitoring of field devices.
Rummel said that new cybersecurity solutions are targeting several critical application areas. Asset management is a major focus, where tools like Softing’s smartLink HW-PN allow secure parameter setting and state monitoring of field devices. Network monitoring and process analysis are also key areas, enabling companies to identify abnormal behaviors and prevent disruptions in IIoT environments. Additionally, real-time inventory through solutions like Softing’s plantPerfect Monitor ensures companies can align as-built device configurations with planned security policies. Beyond these, secure communication channels and segmentation architectures are being applied in industrial control networks to isolate critical systems and reduce attack surfaces. Together, these applications form the backbone of secure, connected manufacturing ecosystems that meet NIS2 and CRA requirements.
Overcoming engineering challenges
“Automation engineers face several challenges when implementing cybersecurity strategies. Legacy systems often lack modern protection and must be upgraded or isolated,” Rummel said. “Management workload is another concern: implementing continuous monitoring, vulnerability patching, and regulatory reporting adds complexity.”
He added that there are also training gaps, as staff must be educated to confidently apply new standards like IEC 62443. Moreover, companies must navigate the tension between IT and OT priorities. Where IT focuses on strict security policies, OT emphasizes uninterrupted operations. Supply chain security is equally pressing, as vulnerabilities can propagate through third-party devices and services. Addressing these concerns requires not just technology, but a holistic approach combining processes, people, and tools, aligned with NIS2 and CRA obligations.

“The industrial cybersecurity landscape is rapidly evolving, driven by several key technology trends that are shaping the newest solutions. The ongoing convergence of Information Technology (IT) and Operational Technology (OT) creates new attack surfaces but also enables more integrated security approaches if a holistic security strategy that spans both domains is used,” — Georg Stoeger, Senior Principal Customer Solution Architect, TTTECH.
Holistic security strategies
More integrated security approaches spanning both the IT and OT domains.
Georg Stoeger, Senior Principal Customer Solution Architect at TTTECH, said that “the industrial cybersecurity landscape is rapidly evolving, driven by several key technology trends that are shaping the newest solutions. The ongoing convergence of Information Technology (IT) and Operational
Technology (OT) creates new attack surfaces but also enables more integrated security approaches if a holistic security strategy that spans both domains is used.”
Stoeger said that another significant trend is the adoption of Artificial Intelligence for advanced threat detection and response. AI-powered solutions can analyze vast amounts of data from industrial control systems (ICS) and OT environments to identify anomalies, which can be used for threat detection in real-time to enable early response to ongoing attacks. We need to consider AI as an enabler for new levels of threat to cybersecurity, but also as a critical component for maintaining cybersecurity.
The “Zero Trust” security model is also gaining traction. This approach, which assumes no implicit trust or safe “firewalled” network zones and instead verifies every access request, is particularly relevant in networked environments where granular control over access to critical assets is essential.
He added that the increasing adoption of cloud technologies and the Industrial Internet of Things (IIoT) is pushing for more robust and scalable security solutions that can protect distributed and interconnected systems. The need for secure-by-design principles, as mandated by regulations like the EU’s Cyber Resilience Act (CRA), is also a major factor influencing the development of new cybersecurity solutions.
Enhanced operational resilience
“A key requirement and also a primary benefit of state of the art cybersecurity solutions for industrial systems is enhanced operational resilience. As threats to system integrity such as zero-day exploits and advanced persistent threats (APTs) evolve and become more complex, real-time visibility into industrial control systems (ICS) and OT environments is necessary to allow organizations to proactively identify and mitigate these threats, minimizing the risk of downtime and production disruptions,” Stoeger said. “Managing system integrity starts with asset inventory, extensive access and event logging, and real-time exposure management across all assets. Based on these (often very large) amounts of data, AI-powered solutions can detect sophisticated attacks that traditional security tools might miss.”
Apart from technical capabilities, new solutions also need to support compliance with emerging regulations like the EU’s Cyber Resilience Act (CRA) and the NIS2 directive. Certified platform solutions can help organizations meet these stringent requirements. Scalability, flexibility and openness of smart manufacturing systems and networks is essential to support digital transformation such as the adoption of IIoT and cloud technologies, but the security challenges that come with this flexibility and openness require a very capable and wide-reaching security architecture that is equally scalable and adaptable. This goes beyond securing the actual infrastructure and must include supply chain integrity, maintenance and update procedures, and interaction with any third-party system.
“In the age of IIoT and the edge-cloud continuum, industrial cybersecurity technologies need to address operational technology (OT) requirements, IT environments, and their interactions over datacenter networks, on-premise networks, and edge-local networks,” Stoeger said. “Unlike IT systems, OT systems often consist of legacy equipment with long lifecycles, proprietary network interfaces and protocols, and a high sensitivity to latency. T
herefore, modern industrial cybersecurity solutions are designed to be non-intrusive and passive, using techniques like deep packet inspection (DPI) to monitor network traffic without affecting operations.”
He added that OT security solutions that can focus on operational context are capable of not only identifying vulnerabilities but also understanding the criticality of assets and processes, allowing for risk-based prioritization of security measures. For example, a vulnerability in a critical production-line controller would be prioritized over a similar vulnerability in a non-critical system. In factory environments, these technologies can perform continuous monitoring and threat detection, providing real-time alerts on suspicious activities.
As mandated by IEC 62443, solutions for industrial cybersecurity also need to support creating security zones and conduits to limit the spread of attacks. Even when proper segmentation is achieved in this way, secure remote access for maintenance and support may still be needed, using granular access controls and monitoring to prevent unauthorized actions. Edge computing solutions provide capabilities to achieve segmentation, secure remote access and management of industrial assets in a single comprehensive platform.
Application areas
Although cybersecurity cannot be applied selectively to just a few critical areas in the industrial system, Stoeger said that there are indeed some applications that have the strongest need for cybersecurity because they protect critical infrastructure and manufacturing operations from a growing number of cyber threats. One primary application area is the protection of the “brains” of the production systems – Industrial Control Systems (ICS) including Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), and Programmable Logic Controllers (PLCs). These systems are the backbone of industrial automation and are increasingly being targeted by attackers.
Another key application area is the security of the Industrial Internet of Things (IIoT). As more and more devices are connected to industrial networks and add attack surfaces, securing these devices and the data they generate is crucial. This includes providing visibility and control over the traffic between IT and OT systems to prevent threats from spreading from the IT network to the OT network.
Last but not least, the protection of legacy systems is a significant application area. Many industrial organizations still rely on older systems that were not designed with security in mind and may not even have basic authentication or encryption capabilities, and industrial edge cybersecurity solutions need to provide a layer of protection for these vulnerable assets.
Engineering challenges
“One of the biggest concerns is the potential for disruption to operations. Unlike IT environments, where a system reboot or a temporary outage is often acceptable, in OT environments, any disruption can lead to significant production losses, safety risks, and financial damage,” Stoeger said.
“Therefore, ensuring that security measures do not impact the availability and reliability of control systems is a top priority. This includes deploying certificates, cryptographic keys, security patches and software updates in a way that does not make the control system unstable.”
He added that another major concern is the complexity of industrial environments. They often consist of a heterogeneous mix of new and legacy equipment from different vendors, using a variety of protocols. This complexity makes it challenging to implement a unified and consistent security strategy.
“The skills gap is another significant concern. There is a shortage of cybersecurity professionals with expertise in OT environments, which makes it difficult for companies to find the talent they need to implement and manage their security programs,” Stoeger said.
“Finally, the cost of implementing and maintaining a robust cybersecurity program is a major concern for many companies, especially small and medium-sized enterprises,” he added. “Balancing the need for security with budget constraints is a constant challenge.”


