TechnologyNovember 22, 2024
The role of VLANs in industrial control systems

Like many networking techniques, VLANs have made their way to industrial facilities. In this article, we'll examine the many advantages VLANs bring to industrial environments. In this environment, VLANs emerge as a key tool by meeting the dual needs of network administrators for traffic management and security.
Since the late 1990s, the virtual local area network, or VLAN, has been a crucial component of modern network strategies. Prior to VLAN development, network engineers were required to create multiple networks and build physically separate LANs whenever an organization needed to partition and isolate multicast network traffic.
VLANs enabled engineers to group end-stations into segments at the data link layer, essentially portioning a single physical LAN into multiple logical or virtual LANs, each with their own broadcast domain. Consequently, broadcast messages could be constrained to a limited number of devices, facilitating granular access control over who can access what within the network.
VLANs are widely used today in mid to large commercial networks to ease traffic congestion, improve network security, and make network configuration, administration and expansion simpler.
Like many networking techniques, VLANs have made their way to industrial facilities. In this article, we’ll examine the many advantages VLANs bring to industrial environments.
What is VLAN?
Simply put, VLANs are isolated, virtual networks within a physical network infrastructure. Each VLAN acts independently as a self-contained network with its own set of rules, security policies, network resources, and broadcast domains. Devices are grouped into a VLAN based on factors such as department, function, or security requirements.
To better illustrate the concept, let’s consider the simple example of a small manufacturing company. Assume that the company’s single physical LAN is being segmented into three isolated VLAN networks: one for production, one for sales, and one for accounting. For simplicity’s sake, we are also going to assume that each of these three departments has two network devices that need to be connected to the company’s twelve-port VLAN-enabled managed switch.
VLAN implementation can take various forms depending on operational needs. The most popular kind of VLANs, port-based VLANs, group devices based on their physical connection to a network switch. A more flexible method is provided by MAC address based VLANs, which divide the network according to the MAC address of the device.
Though less common, protocol-based VLANs offer network protocol-based segmentation, enabling more precise traffic control.
For this example, we are using port-based VLAN implementation. Here, the network administrator accesses the switch’s management interface to create new VLANs, i.e. VLAN 10 for production, VLAN 20 for sales, and VLAN 30 for accounting, and then assigns two relevant ports of the 12-port switch to one VLAN for each department. The administrator would then plug each device from the three departments into their assigned VLAN port and associate them with their corresponding VLAN ID. To mark messages as VLAN traffic, the switch inserts a VLAN tag into the frame of the IP layer header. Each VLAN has a unique VLAN ID, which is an embedded 12-bit value (from 1 to 4095) in the VLAN tag.
Ports can be either access ports or trunk ports. Host devices are connected through access ports, which are part of a single VLAN, as is the case in this example. Trunk ports are those that can be assigned to many VLANs. To transport traffic for many VLANs over a single physical connection, network equipment including switches or routers, generally build a VLAN trunk, which is a link or connection that can carry multiple VLANs simultaneously. Known as inter-VLAN routing, this will involve creating sub-interfaces for each VLAN on a router and assigning IP addresses to them.
As a company grows, new segments of the same network can be easily added, or old ones reconfigured without disrupting the entire network or additional hardware investments. VLANs enable a network to scale swiftly and cost-effectively.
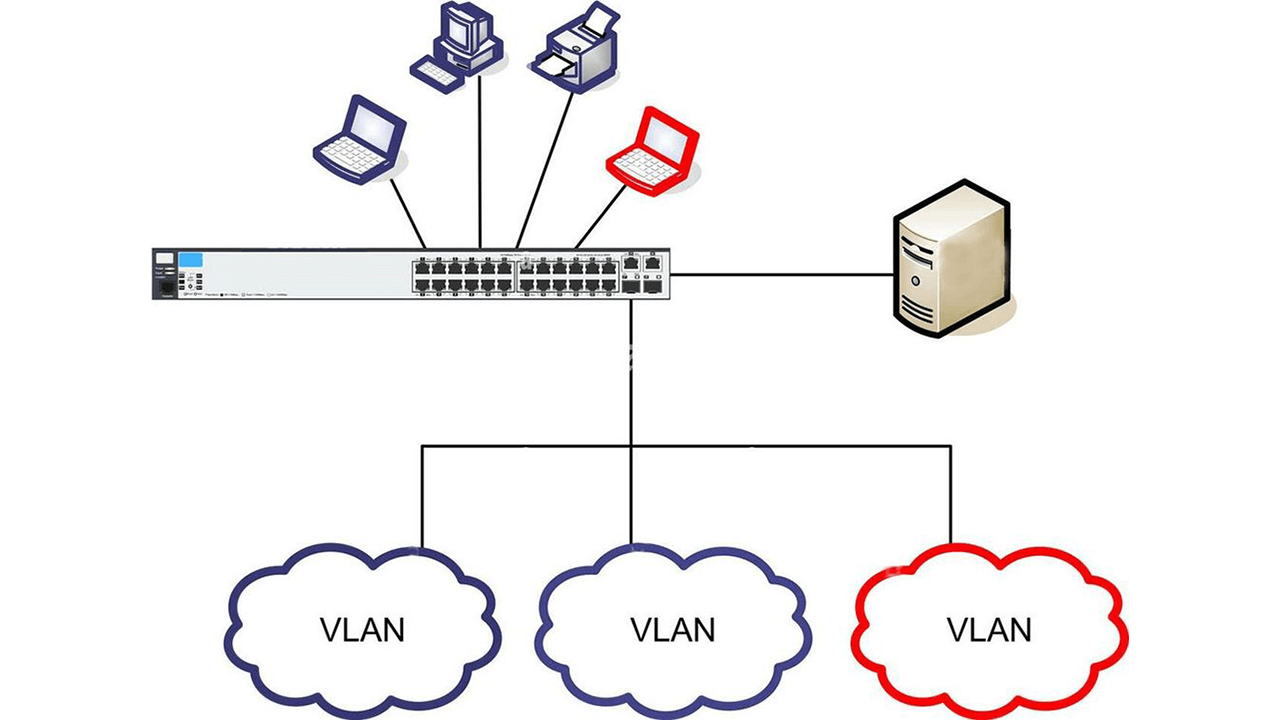
VLANs are isolated, virtual networks within a physical network infrastructure that act independently as a self-contained network with its own set of rules, security policies, network resources, and broadcast domains.
VLANS in Industrial Control Systems
In Industrial Control Systems (ICS), it is not uncommon to have hundreds of connected I/O devices, such as RTUs, PLCs, Sensors, HMI, relays, and servers for applications, engineering, front-end and archiving.
As the number of devices connected to an ICS increase, the volume of broadcast messages soars to the point that it starts to consume more of the processing bandwidth of the devices, causing congestion and impeding network performance.
In this environment, VLANs emerge as a key tool in your network arsenal by meeting the dual needs of network administrators for traffic management and security:
ICS Traffic Management: ICS responsiveness and operational productivity are directly impacted by the efficiency of network traffic management. By segmenting the network, VLANs lessen unnecessary broadcast traffic, which can be especially disruptive in ICS environments. As a result, vital applications run more smoothly on the network and experience less congestion. Real-time control systems depend on the prompt transmission of control commands and real-time data, which is made possible by the ability to prioritize traffic for vital systems via VLANs.
ICS Cyber Security: By dividing a physical network into many isolated virtual networks, VLANs help to enforce cybersecurity policies, regulate access, and restrict the spread of malicious activities to a limited area by establishing virtual boundaries. An ICS typically has a multitude of different systems and devices, all with varying levels of sensitivity and security requirements. An administrator can tailor security measures to the differing needs of each segment, improving the overall security posture without compromising the network’s operational efficiency. Additionally, VLANs can be set up to limit access according to user roles and responsibilities, which lowers the possibility of insider threats or unintentional disruption of vital systems.
Getting Started
For all their advantages, VLANs require more configuration and management than the subnetting or routing techniques you may be more familiar with. A complete understanding of the network infrastructure and operating requirements of an ICS is necessary before implementing VLANs on it.
Your first step is a network assessment, which includes identifying critical assets and figuring out the best approach to segment them using VLANs. Identifying network traffic patterns will show which devices need to communicate with each other. To prevent inter-VLAN routing delays, devices requiring real-time communication must be connected to the same VLAN. Remember, because VLANs are not limited by proximity or physical location, devices belonging to the same VLAN can be distributed throughout the ISC physical network and still function as though they are linked to the same local network switch.
Striking a balance between satisfying every requirement and avoiding complexity could be your toughest task. VLAN configurations that are too complicated may be hard to manage and monitor, which could result in security flaws.
Once in place, it is important to regularly update and examine a VLAN configuration. Changes in the ICS environment, such as the addition of new devices or the repurposing of existing ones, will require adjustments to the VLAN setup.
VLANs are isolated, virtual networks within a physical network infrastructure that act independently as a self-contained network with its own set of rules, security policies, network resources, and broadcast domains.
Antaira managed Ethernet switches are VLAN-enabled to help partition any size network into logical isolated segments – without the hassle or cost of deploying new cabling and networking devices, relocating network nodes elsewhere, or rewiring links.
Henry Martel, Field Application Engineer, Antaira Technologies


