TechnologySeptember 20, 2024
Cybersecurity basics: industrial security fundamentals

The fundamentals of industrial cybersecurity are based on key principles including confidentiality, integrity and availability. Cybersecurity often seems like an invincible Hydra but, with practical guidelines, users can setup systems and create strategies that significantly strengthen the security of company networks.
Cybersecurity is a bare necessity, that much is clear. What is less clear, however, are the basic principles that form the foundation of a strong and effective cybersecurity strategy. If they are missing, the entire concept is rickety.
Part One: Confidentiality, Integrity and Availability
C.I.A. – these three letters stand for the classic understanding of cybersecurity. Even if others are sometimes added, these three form the core. The C stands for confidentiality. This means that only the authorised parties involved are allowed to read the content. The I stands for integrity, which states that the content of a message may not be changed. In addition, the A is availability: a message must be available for exactly as long as necessary, neither longer nor shorter.
When it comes to IT security, these three aspects are considered equally important. In the area of OT, though, availability is the top priority. After all, if there are interruptions in a production line, this can result in vast financial costs. In an operating theatre, it can even be a matter of lives. This means that in the area of OT, not only the threat must be evaluated, but also the effects of security measures.
In an OT network, Principle C (confidentiality) requires the data flow between sensors, controllers and other devices in an OT network to be encrypted, e.g. by using TLS/SSL, so that no unauthorised party can access sensitive information. This might also include the encryption of firewall configurations that contain confidential details about the network’s security design. I for integrity demands that only subscribed or purchased operating systems and software are run on the hardware – also known as secure boot. Moreover, A for availability refers to a network concept that guarantees redundancy to rule out a single point of failure (SPOF).
Controlling access to information ensures confidentiality and integrity. Here, it is important to distinguish between authorisation and authentication. Authentication is the process of checking whether a person or computer is actually who they say they are. This ensures everyone knows with whom they are sharing information. Authorisation, on the other hand, regulates the access rights or privileges of a person or software. Both – clearly defined authorisation guidelines and the systematic authentication of users – are crucial for preventing intrusions.
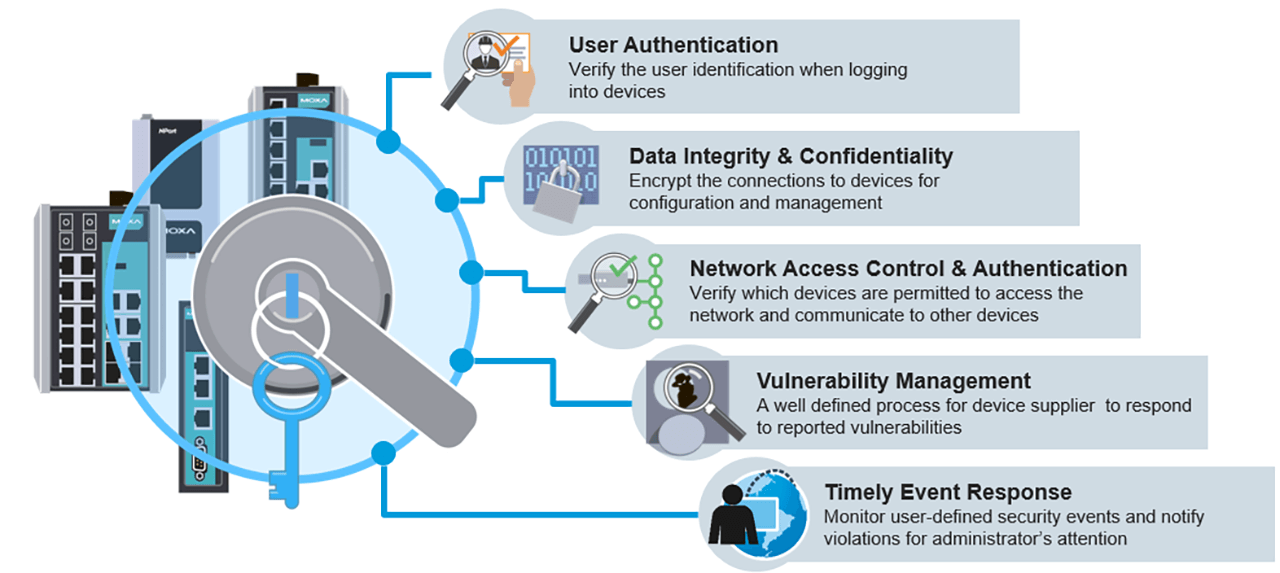
Following the fundamentals of cybersecurity management creates the discipline required within an organization.
Types of threat – meaning well does not always equal doing well
The basis of a cybersecurity strategy also includes defining possible dangers. Obvious examples are powerful hacker organisations, international espionage and warfare. Still, this doesn’t mean that anyone who isn’t connected to the internet or company network is safe: around a fifth of threats arise from internal hazards. All it takes, for example, is a disgruntled, dismissed employee whose password hasn’t been changed. In Maroochy, an administrative area of Australia, for example, a worker hooked up the network of a water treatment plant to a Wi-Fi router before switching jobs. Years later, when he was rejected for a position at the town hall, he flooded the park with 1,000 litres of wastewater.
Yet, even with good intentions, employees can cause harm. In terms of security, it makes no difference whether the intention is malicious or not – it is the result that counts. With the dramatic rise in sophisticated social-engineering and deepfake-phishing attempts, the risk of an employee trying to help their manager in a supposedly threatening situation that is actually fake and malicious is growing. In 2019, a major American bank made headlines when it accidentally exposed over 800 million private data records, including driving licence details and bank statements.
Another myth that needs to be invalidated is the idea that it takes powerful supercomputers and the latest technology to cause significant damage. The reality is much simpler: crime is already offered “as a service”. According to Forbes , paralysing an internet-based asset for an hour on the darknet only costs USD 165, while you can obtain a valid credit card number linked to an account with at least USD 10,000 for as little as USD 25.
Cat-and-mouse game
The rapid development of criminal cyberattacks with ever more complex and precise forms of intrusion poses a challenge for protective measures to keep pace. While brute-force attacks are still common, ransomware continues to grow and social engineering is becoming more sophisticated. Advanced persistent threats (APTs) are used to secretly collect private data over a longer period of time.
Once an attacker has found an easy victim, it is quite possible that they will look for further vulnerabilities. It is a well-known fact that it takes some time to make a weak infrastructure secure. However, even rudimentary cybersecurity measures can significantly reduce the potential extent of damage and the consequences of a successful attack.
Dealing with vulnerabilities
In this context, it’s important to know how weak points are currently handled. During the development of a network component, they can be recognised at an early stage with static tests or peer reviews. Automated tests are used to check the system’s resistance to common attacks. Intrusion tests are also common practice, in which a third party attempts to systematically and exploratively circumvent the defence measures. Should a vulnerability be discovered in a new product, the manufacturer can fix it immediately. If the product is already on the market, the person carrying out the test usually notifies the manufacturer and gives them time to create a patch before publicising the problem via groups such as MITRE. Although such responsible disclosure is not required by law, it is standard practice in the security industry.
Not only are vulnerabilities publicly available, there are even free search engines that can be used to look for network equipment based on vulnerabilities. This means that weak points in devices and software are known to the public. It is crucial to identify which ones need a firmware update and to execute it in a timely manner.
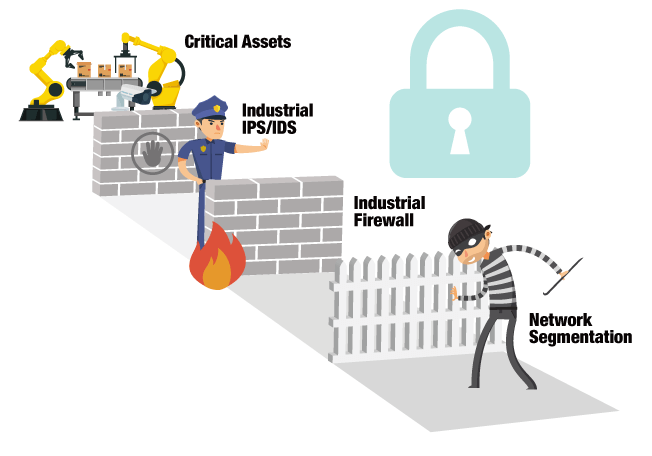
Fundamentals of Defense in Depth strategies.
Protection mechanisms
One common shield against online threats is encryption. It prevents information from being intercepted during the communication between two nodes. For example, a Wi-Fi connection can be tapped, but if it uses WPA encryption, the transmitted content cannot be deciphered. Communication via open networks, e.g. in hotels or airports, must be encrypted to maintain confidentiality. However, even if the communication is private, e.g. between employees working from home, all intermediate networks that make up the internet must be considered a threat.
Another encryption application is signatures. In contrast to symmetric encryption, which uses the same key for encryption and decryption, asymmetric methods use different keys. This means that a communication can be encrypted with a secret key and anyone who decrypts it with the publicly available key can read its content. In addition, the recipient knows that the document originates from the owner of the secret key as the document bears a signature. This way, digital certificate authorities (CAs) can provide entities with certificates certifying the authenticity of this entity. This is the case, for example, with websites that use HTTPS. If their certificate is invalid, it cannot be decrypted with the CA’s public key. In this situation, the browser cannot verify the identity of the website and doesn’t display it. The reason is that the website could be an imitation of the original or a malicious intermediary between the user and the original website.
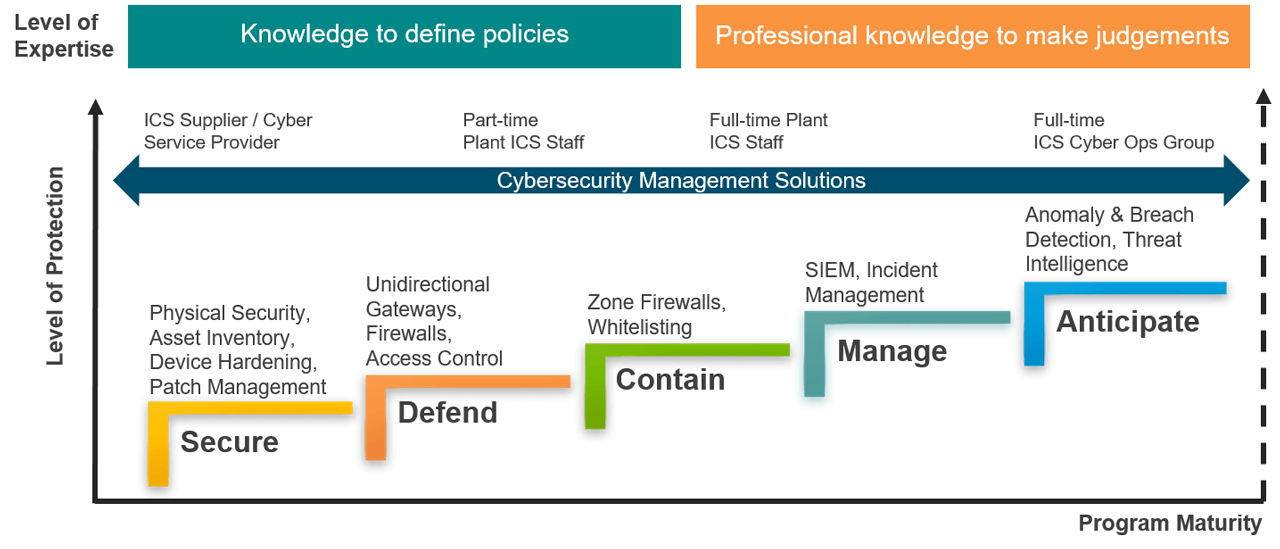
ARC Cybersecurity Maturity Model.
Security at network topology level
There are further measures that make network topologies resistant to cyberattacks. In the OT sector, air gapping is frequently found. The internal network and the globally networked outside world are separated. Nevertheless, air gapping is no longer considered sufficient because many potentially dangerous actors are located internally. If no physical access control is used in conjunction with air gapping – i.e. control over who can enter the building – anyone can join the network via a USB stick or the Wi-Fi. And do the network engineers have a list of all the computers that have activated Bluetooth? Most of them do not. This means the network is open and connected.
The expression “castle with moat” uses a medieval metaphor to describe a network with extremely robust perimeter security. It is based on the assumption that the outside world is hostile, while the inside is secure. Unfortunately, this model is no longer up to date. Since the COVID pandemic at the latest, many people have been using VPNs to work from home. This blurs the “secure perimeter”: Does it include the home network? Is that secure?
A more advanced design is “defence in depth” with a multi-layer principle: each layer is slightly more secure than the last, with the most important operations and data that must not be compromised under any circumstances in the middle. The “defence in depth” method is the foundation for the Purdue model, which is also recommended in EU cybersecurity guidelines.
One modern architecture is SASE (Secure Access Service Edge). Here, all security functions, including authentication and authorisation, are not located in a central system, but at the edge of the network.
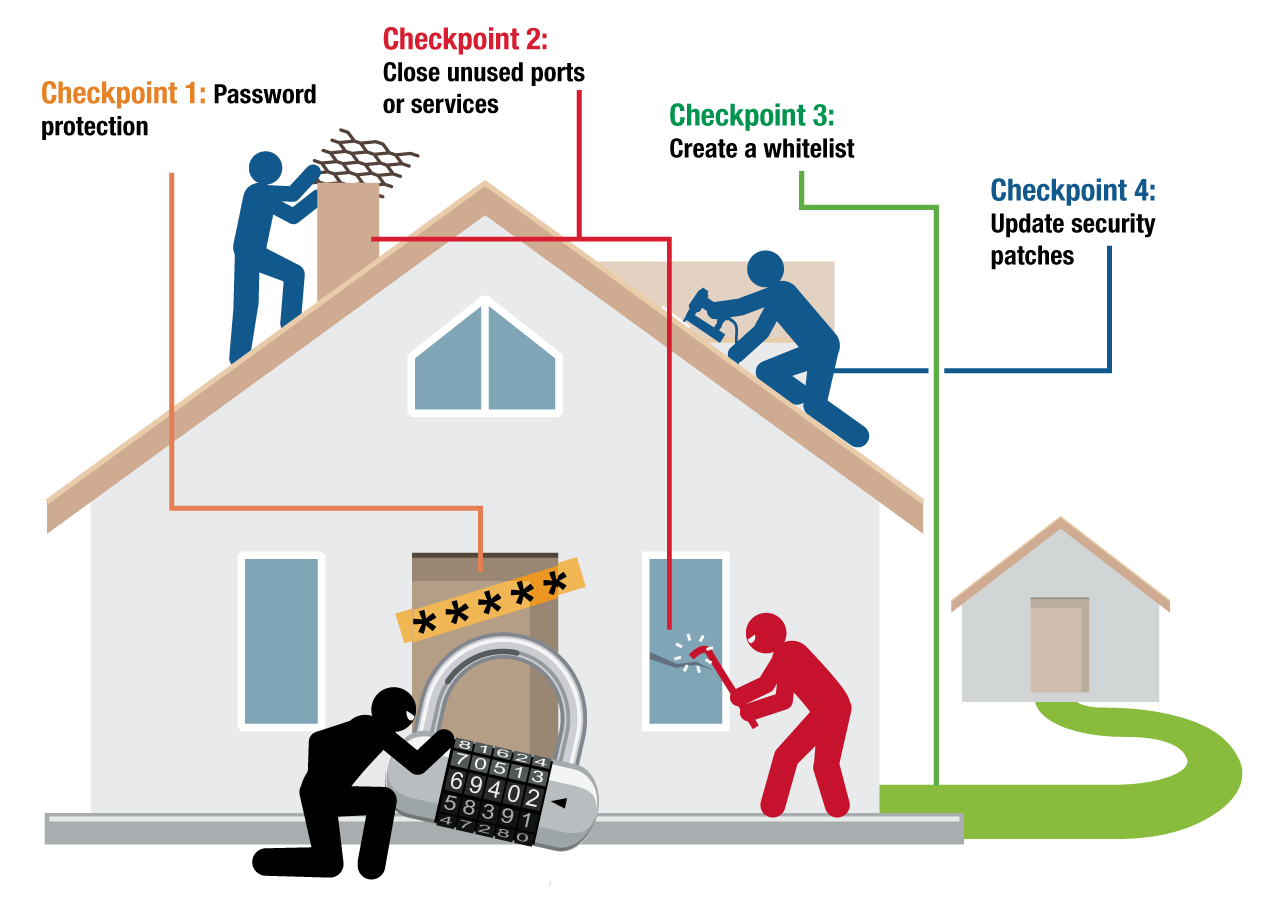
Device security checkpoints.
Part Two: specific steps for more security in industrial automation
Cybersecurity often seems like the invincible Hydra, constantly growing new heads as soon as one has been cut off. However, with practical guidelines, you can defeat it and significantly strengthen the security of the company network.
Threat modeling
The first step towards a stable cybersecurity framework is gaining a detailed overview of the existing network and identifying the potential vulnerabilities. To do this, it is advisable to catalogue critical assets, including all machines, systems, and areas in which intellectual property and/or confidential information is saved.
This is followed by a thorough assessment of the direct and indirect consequences of potential threats, allowing you to define a response strategy that reduces immediate risks and prevents long-term consequences. To this end, the risks associated with each identified threat are categorized. Possible responses are considered for each threat:
- Acceptance: some risks may be considered acceptable; thresholds are then used to determine the point up to which the risk is tolerable and monitoring is sufficient.
- Damage containment: a strategy to reduce the likelihood or impact of potential threats may include implementing security measures, protocols, and redundancies.
- Elimination: structural changes to the network, the integration of advanced security technologies and the removal of vulnerable components help eliminate risks from the start.
Directives, laws, and standards
Compliance with EU directives, national laws and industry-specific cybersecurity standards is a must. However, by keeping up to date with regulations and guidelines, companies not only fulfil their legal obligations, but also increase their own security.
On this basis, it is also important to define governance rules. These should include the policies, procedures and protocols that govern day-to-day operations of industrial automation. Effective cybersecurity governance includes solid risk assessment, ongoing identification of cybersecurity risks and up-to-date guidelines based on industry standards. Integral components include access controls, defined responses to incidents, and the sensitization and training of employees.
Once the governance rules are in place, it is important to monitor them continuously and carry out regular security checks and assessments. This is the only way to identify and resolve new vulnerabilities.
Setting up a resilient network
The fundamental step to a secure industrial automation network is to carefully assess the security requirements for each segment. Segmentation involves dividing the network into separate segments or zones to control traffic, improve security and mitigate potential attacks. Each segment can have its own security policies and access controls to increase security and minimize the risk of threats. This allows for a targeted security strategy focusing on specific parts of the network while improving overall system security.
When assessing each segment, consider the organization’s critical assets and confidential information, identify potential vulnerabilities, and assess the potential impact of security breaches on each segment. That way, each segment can be assigned a security level based on the probability and possible impact of a successful attack. Resources can thus be allocated effectively and protection prioritized where it is most urgently needed. On this basis, a plan for a secure network model can be created step by step.
To start with, it is advisable to begin with simple hygiene measures. These include regular software updates, password management, and basic access controls, e.g. restricting the use of certain resources to individual MAC addresses.
The next step will show solutions that are more sophisticated. According to the defense-in-depth principle, several layers of security measures can be combined to create a multi-layered defense strategy. A mix of firewalls, intrusion detection systems, and encryption is recommended.
By separating the floor plan from the corporate network with a DMZ (demilitarized zone), a buffer network, direct communication between the corporate and floor network is prevented and access is controlled with firewalls.
In addition, the isolation of critical segments is an important aspect for minimizing the movement and therefore the spread of threats within the network. To this end, the number of access points and the number of neighboring networks that can communicate with the most secure segments are kept to a minimum. This maintains the integrity of the entire network, even if one area is compromised.
Furthermore, authorization mechanisms should be adapted to the functional roles to ensure that people only have access to resources that are necessary for their tasks. It is advisable to separate administrative roles from other functions and thus strictly limit access to critical configurations and sensitive information.
Software upgrades
It makes sense to approach the topic of software upgrades with a meticulous inventory of the firmware versions of all important devices. This demands caution, professionals should check the authenticity of upgrades with the respective provider. Otherwise, the door is open for counterfeit malware.
The upgrade process should be carried out in stages so that the effects of upgrades can be monitored and evaluated on a smaller scale before they are applied to the entire network.
In many cases, an immediate firmware update is not possible. The recommended alternative is virtual patching. This involves implementing security measures at network or application level so that no changes to the firmware are required. Hence, network traffic can be actively monitored, malicious patterns identified, and vulnerabilities prevented from being exploited by outdated firmware.
Foster security awareness
In addition to technical measures, the human factor is crucial. Teams must be equipped with the necessary resources to master the intricacies of different types of attack. This starts with creating checklists and step by step procedures that act as practical guides for each type of attack. These materials should be simple and practical, and complex security measures should be broken down into practicable steps. This will enable cybersecurity specialists to empower other teams to respond effectively to threats.
In order to embed cybersecurity awareness in the minds of employees, regular training programs are needed that cover theoretical aspects as well as practical exercises on real-life scenarios.
The corporate culture is also an important pillar for security awareness, emphasizing an environment where team members can report security concerns without fear of reprisals, which is crucial. Placing blame for security incidents is counterproductive. Instead, the focus should be on understanding the causes and taking corrective action. Praise is also an effective way of encouraging positive behavior. Recognizing vigilance and responsiveness encourages employees to actively contribute to the safety of the company.
Security in the ecosystem
A solid security strategy also takes all of the company’s partners into account. This starts with defining clear rules. Authentication should be one of the non-negotiable security aspects, as it is proof of the legitimacy of interactions within the industrial ecosystem. Of course, authentication protocols must comply with industry standards and regulations. Apart from that, partner assessments, audits and security practices should be continuously scrutinized by experts.
Based on the principle “Together we are stronger”, actively sharing threat intelligence and best practices is also recommended to ensure that security measures are mutually reinforcing.
Network monitoring
The first step of network monitoring is gaining a comprehensive understanding of the activities within the industrial ecosystem. With the help of modern tools and technologies, network traffic, device interactions and communication patterns can be observed in real time. This allows anomalies, potential vulnerabilities, and unauthorized access to be detected.
Monitoring security breaches requires robust intrusion detection systems, log analysis, and an active search for signs of unauthorized access, malware, or other security breaches. This is where the aforementioned culture of encouraging employees to report security incidents comes into play.
Every security incident should be meticulously documented, even (seemingly) minor incidents. It is helpful to develop a standardized process for recording the details of the incident, the measures taken, and the lessons learned. Such documentation not only ensures compliance with regulations, for example during audits, official inspections, or internal reviews, but also provides valuable insights for the continuous improvement of cybersecurity.
Continuous improvement
Cybersecurity is a never-ending task. With defined processes for continuous improvement, organizations create the preconditions for a continuous improvement cycle. This should include the regular review and refinement of security protocols, incident response procedures, and monitoring mechanisms. The evaluation should involve team members from different departments and hierarchical levels, and suggestions should be considered without reservation. Training programs, awareness campaigns, and collaboration frameworks should also be part of continuous improvement.
At the same time, the threat landscape is constantly changing. Active participation in threat intelligence networks and industry forums as well as continuous training help prepare people for evolving threats.


