TechnologyMarch 12, 2022
How control systems benefit from integrated cybersecurity
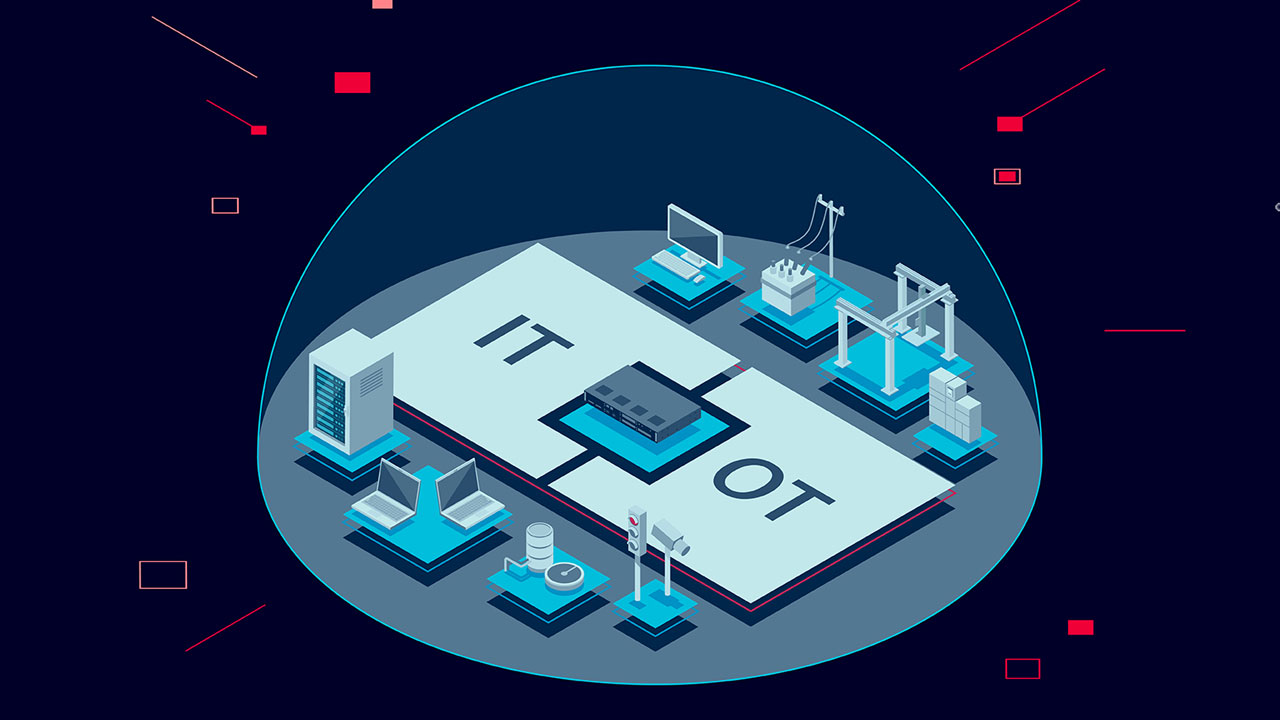
Convergence of OT and IT systems is placing higher demands on network reliability and performance. As cybersecurity threats challenging these systems become more sophisticated and impacting, industrial network owners are looking to integrated solutions to ensure both holistic security and business continuity.
Industrial control systems in critical infrastructure applications, such as electric power, transportation and other essential utilities are undergoing rapid digitalization.
The increasing convergence in OT-IT systems puts a higher demand on network reliability and performance. In addition, operational infrastructure deployed in the field for these applications must last long periods without renewal. As cybersecurity threats towards these systems become increasingly sophisticated and impacting, industrial network owners can look to integrated solutions to ensure holistic security and business continuity.
With the challenges of stricter regulations, ensuring greater network reliability and operational efficiency with lower costs faced by OT networks, a holistic cybersecurity approach is mandatory. However, the current landscape is hard to navigate; regulatory requirements and the penalties imposed on non-compliance across different regions and industrial verticals are varied and increasing, there are no standardized security solutions, and industrial control systems vary between networks, even in the same industry. Most available security offerings in the market address only a part of the security. Therefore, network owners often employ system integrators to build out customized solutions.
Benefits of technology integration over a custom solution
One of the main end-user benefits is that technology leaders are combining their domain know-how and are putting out tested and proven solutions that just work in the field. These solutions are designed to be easily deployed in an existing or new network and only require one hardware device compared to a network and a security device. This optimization makes the integrated solution easy to use and maintain, both from a hardware and software perspective.
Siemens’ Ruggedcom APE1808 industrial application hosting platform plugs in to the Ruggedcom RX1500 Multi-Service Platform, providing a future-proof, field-modular design for applications in harsh environments. The hardware reliability combined with maximum flexibility delivers a best-in-class OT networking platform.
Palo Alto Networks’ VM-Series Next-Generation Firewall (NGFW) is deployed on the Ruggedcom APE module. The Siemens hardware and operating system provide the networking capabilities, infrastructure, and processing power required for harsh environments. Palo Alto Networks NGFW furnishes the cybersecurity software required to analyze network traffic, act as a segmentation gateway, and provide application-level monitoring and threat protection.
Combining the Siemens hardware with the Palo Alto Networks VM-Series virtual firewall establishes an Intrusion Prevention System (IPS) between the WAN and the LAN (or different network segments) denying the traffic that represents known threats. Such protection is increasingly important when connecting critical OT assets and non-critical IT networks. Together with the other NGFW features like Threat Prevention, this technology supplies best-in-class security to stay ahead of fast-evolving threats. Likewise, Fortinet’s VM-based Next-Generation Firewall can also be deployed on the Ruggedcom APE.
Furthermore, Siemens cybersecurity experts have tested solutions for anomaly-based intrusion detection with Deep Packet Inspection capabilities from Nozomi Networks and Claroty. This integration helps SOC (Security Operations Center) operators have complete transparency and monitor all assets, data and behavior on the network, and respond appropriately to anomalies as they arise.
An integrated solution not only combines “Best-of-breed Technology”, it stays relevant and available for a long time when enabled by established technology leaders like Siemens and industry leaders in threat detection and prevention, who support their products over time. These solutions are engineered to scale as the network needs increase and technologies evolve.


