TechnologySeptember 23, 2024
Industrial cybersecurity experts weigh in on the future

Cybersecurity has become the number one issue for factory networks. Experts predict that artificial intelligence and machine learning will make an impact, the IT and OT worlds will grow closer together and that resilient network infrastructure and structured frameworks will strengthen industrial cybersecurity solutions.
THE FUTURE OF INDUSTRIAL CYBERSECURITY is dependent on the development of new technologies that will make the next generation of industrial networks more intelligent and more secure than ever before.
For this special report on Industrial Cybersecurity, IEB reached out to a series of industry experts to get their perspective on the technologies that are shaping present and future industrial cybersecurity solutions.
Seven leading companies have responded with their take on the trends for industrial cybersecurity, what they see as the most potent solutions available, the challenges that automation engineers are facing and what promises to be the leading industry applications. Here is what they have about the technologies and trends shaping the next generation of industrial networks.
Keys to protecting industrial environments
OT visibility, software-based segmentation, zero-trust remote access, and unified IT/OT security platform.
According to Fabien Maisl, Marketing Lead, Industrial Security at Cisco, “the key technology trends in industrial cybersecurity include the adoption of enhanced OT visibility, software-based segmentation, zero-trust remote access, and unified IT/OT security platform. Vendors are addressing these concerns with innovative solutions designed to protect industrial environments effectively.”
Enhanced OT Visibility: Identifying and profiling OT assets is key to reduce the attack surface and build effective security policies. Traditional OT visibility solutions require deploying dedicated appliances or SPAN networks which are proving too complex and expensive. OT visibility capabilities can now be embedded in networking equipment to easily capture east-west traffic and gain comprehensive visibility on all OT assets.
Software-based Segmentation: Segmenting industrial networks in small zones of trust is an efficient way to protect operations and avoid attacks to spread. But in many cases, it can be too complex to modify the network, deploy zone-based firewalls, and ensure assets are placed in the proper segment without disrupting production. Software-based segmentation leverages networking equipment to easily enforce access policies that can be centrally configured and dynamically updated. Combined with enhanced IT visibility, this helps IT and OT work together to easily build a segmentation strategy.
Zero-Trust Remote Access: Machine builders, maintenance contractors, and the operations teams need remote access to OT assets for maintenance and troubleshooting. Cellular gateways or software products that IT is not controlling are security backdoors.
VPNs are too complex to manage at the scale of OT. Organizations are starting to deploy Zero-Trust Network Access (ZTNA) solutions to simplify the remote access workflow. Remote users log into a web portal where access policies are defined and enforced for the entire infrastructure, making it easy to define credentials and control access. The portal communicates with routers and switches in the infrastructure to ensure that remote users are only granted access to selected equipment which they need to configure, not to the entire network.
Unified IT/OT Security: Industrial operations are no longer working on air gapped environment. Industry 4.0 and OT digitization require seamless communications between OT, IT and cloud resources. As IT and OT networks are converging, IT and OT security also needs to converge. Organizations need to enable a cohesive security strategy that includes having global visibility on both IT and OT environments to detect modern threats faster, unifying security policies to avoid gaps in defense, and leveraging IT security tools and practices to enable advanced protection of OT assets and orchestrate faster remediation and recovery.
Technology benefits
Maisl said that the newer solutions offer specific benefits for industrial cybersecurity offer, and potential impact on manufacturing networks. These benefits include:
Enhanced OT Visibility: Embedding OT visibility capabilities in networking equipment allows manufacturing networks to gain comprehensive insights into all OT assets. This leads to improved asset management, better threat detection, and streamlined security operations, making the network more secure and resilient.
Software-based Segmentation: Implementing software-based segmentation in manufacturing networks enables the creation of small, manageable zones of trust without extensive network modifications. This minimizes production disruptions, enhances collaboration between IT and OT teams, and improves the containment of cyber threats, thereby protecting critical operations.
Zero-Trust Remote Access: Deploying Zero-Trust Network Access (ZTNA) solutions in manufacturing networks simplifies remote access management. It ensures that remote users only access necessary equipment, reducing the risk of unauthorized access and enhancing overall security. This streamlines the management of remote access policies and credentials and safeguards OT assets from potential threats.
Unified IT/OT Security: Converging IT and OT security strategies in manufacturing networks provides global visibility across both environments, enabling faster threat detection and unified security policies. This results in improved defense against modern threats, seamless communication between IT, OT, and cloud resources, and a cohesive security posture that enhances overall operational resilience.
Cutting edge cybersecurity
“To gain visibility on OT assets and their activities, you need to capture network traffic to extract information from communication flows,” Maisl said. “Traditional security solution providers typically configure SPAN ports on network switches to duplicate traffic and send it to a central server or dedicated appliances. Not only is this complex to manage, it’s also very expensive to deploy at scale as you would need to SPAN traffic from all switches to gain visibility on east-west traffic in addition to north-south traffic.”
He added that, with Cyber Vision, Cisco embeds visibility capabilities into switches and routers, eliminating the need to duplicate network flows or to deploy additional appliances. Obtaining visibility is a matter of activating a software feature. Cost, traffic, and operational overhead are all minimized.
“Segmenting industrial networks is key to protect operations and avoid attacks to spread. It is a key requirement of the ISA/IEC62443 security standard. Firewalls are perfect for building an industrial demilitarized zone (iDMZ). But deploying rugged firewalls in each product cell in factories leads to deployment issues like those IT faces with visibility appliances. Not only can it be very expensive, maintaining these firewall rules can become a challenge,” Maisl said.
Solutions such as Cisco Identity Services Engine (ISE) work with your network switches, routers, and wireless access points to restrict communications according to the zones and conduits you have defined. It leverages groups defined in Cyber Vision to allow or deny communications for each asset. When a change is required, you can just move the asset to another group in Cyber Vision. ISE will automatically instruct the network to apply the corresponding security policy.
When it comes to remote access, in many cases machine builders, maintenance contractors, or the operations teams themselves have installed their own solutions: cellular gateways or software products that IT is not controlling. These backdoors are at odds with the OT security projects undertaken by the IT/CISO teams and create a shadow-IT situation that makes it difficult to control who is connecting, what they are doing, and what they can access. On the other hand, VPNs have the drawbacks of being always on, with all-or-nothing access, and requiring complex configurations to control what remote users have access to.
With Secure Equipment Access (SEA), Cisco is solving the challenges of deploying secure remote access to OT at scale. It embeds the gateway function into Cisco industrial switches and routers. Enabling remote access is now a software feature to activate. There is no dedicated hardware to install and manage. Configuring and enforcing security policies is done in a central console, making it easy to control who can access what and when across all sites. Distributing the gateway functionality anywhere in the network enables remote access to any assets, even those being NAT boundaries. The switch or router that provides connectivity now also provides remote access to these assets. And the same network equipment can enforce segmentation policies to prevent lateral movement to other assets.
Responding to challenges
Maisl said that one major concern for customers is the lack of visibility into OT assets. Many organizations do not have a complete inventory of all their OT and ICS devices, making it difficult to monitor and secure them effectively. This lack of visibility can lead to blind spots in the network, where vulnerabilities may go undetected, or unknown assets becoming the source of an attack. Without a detailed inventory of assets and their roles in the industrial process, it is becoming almost impossible to design and enforce security policies that will effectively protect the environment without disrupting production.
Another concern is the complexity and diversity of industrial environments which generally include legacy systems that were not designed with cybersecurity in mind. Protecting these systems is a significant challenge and requires precise mitigation measures you can only implement if you have a detailed asset inventory.
Additionally, the convergence of IT and industrial networks increases the attack surface, requiring comprehensive security measures that address both domains. Gone are the days when OT security could be managed in its own silo. Organizations now also need to converge their IT and OT security practices and implement a unified cybersecurity strategy. However, there is still a lack of collaboration between IT and OT teams. This siloed approach makes it challenging to design, implement, and maintain effective cybersecurity strategies.
Targeted applications
“As manufacturers accelerate digitization of their factories, they realize that both industrial networking and cybersecurity technologies are growing in complexity,” Maisl said. “As they increasingly use data to drive software-defined industrial operations and adopt AI technologies, there is a clear need for a converged strategy that incorporates not only IT and OT but also security.”
He added that, to enable smart manufacturing operations, the factory network must adopt modern IT technologies. Only this can simplify managing and reconfiguring the infrastructure, virtualize functions that used to run on dedicated hardware, support the fast and reliable transmission of large volumes of data to AI applications, and more. This IT infrastructure must be supported by comprehensive cybersecurity capabilities that are made simple and cost effective to deploy at scale.
Cisco is converging network and security functionality to reduce complexity, enable unified IT/OT security practices, and help accelerate adoption of AI-driven factories. Our network designs include centralized management of networks and security policies, unified visibility into both OT and IT, automated network segmentation, zero-trust remote access, and more… all embedded into rugged industrial networking equipment purpose-built for the constraints of advanced manufacturing operations.

“The integration of IT and OT systems requires a robust communication infrastructure that can handle the demands of both realms. Current technology trends in industrial cybersecurity include the increased adoption of AI-driven threat detection, zero-trust architectures, and advanced network segmentation,” Michael Metzler, Vice President Horizontal Management Cybersecurity for Digital Industries, Siemens.
IT-OT Convergence
Robust communication infrastructure needed to handle the demands of both realms.
Michael Metzler, Vice President Horizontal Management Cybersecurity for Digital Industries at Siemens said that “the convergence of Information Technology (IT) and Operational Technology (OT) is a rapidly evolving trend in the industrial sector. As companies increasingly look for ways to optimize their operations and improve efficiency, the need for seamless communication between traditionally separate systems becomes paramount. It lays the foundation for data-driven decision making.”
“The integration of IT and OT systems requires a robust communication infrastructure that can handle the demands of both realms. Current technology trends in industrial cybersecurity include the increased adoption of AI-driven threat detection, zero-trust architectures, and advanced network segmentation,” he said.
To this end, Siemens – a major supplier for industrial cybersecurity – is offering solutions that offer real-time monitoring, automated response capabilities, and enhanced visibility across both IT and OT environments. These solutions are designed to be scalable, allowing companies to protect both modern and legacy systems without significant overhauls.
Solutions for industrial cybersecurity
“Industrial networks are the nerve pathways in production; they are becoming in sum ever more complex. Hardware alone no longer determines their performance. Software-based network management and the use of cybersecurity tools have become indispensable,” Metzler said.
He added that new industrial cybersecurity solutions offer several benefits including improved threat detection, reduced response times, and enhanced protection against both internal and external threats. These solutions can significantly reduce the risk of costly downtime due to cyber incidents, thereby improving overall operational efficiency. The potential impact on manufacturing networks is substantial, as these solutions enable a more resilient and secure production environment, which is crucial in an era of increasing cyber threats.
“The risk of cyberattacks on industrial plants is real – and the frequency continues to increase. To comprehensively protect industrial plants against cyberattacks from inside and outside, all levels must be addressed simultaneously – from the operational to the field level, from data protection to secure communication,” Metzler said.
With Defense in Depth, Siemens provides a multi-layered security concept that offers industrial plants comprehensive and far-reaching protection in accordance with the recommendations of the international IEC 62443 standard.
It is aimed at plant operators, integrators and component manufacturers and covers all relevant aspects of industrial cybersecurity. Cutting-edge cybersecurity technologies in industrial environments are characterized by their ability to seamlessly integrate with existing systems, including legacy OT devices. Technologies such as machine learning-based anomaly detection, industrial firewalls with deep packet inspection, and secure remote access solutions are being applied in factories to provide real-time threat detection and automated incident response. What makes these technologies unique is their focus on the specific needs of industrial environments, where uptime and safety are paramount.
Customer concerns
A key issue is addressing the primary concerns that automation engineers and companies are facing when implementing industrial cybersecurity strategies.
“The special framework conditions in Operational Technology (OT), including continuous operation, high performance requirements, and availability, demands an in-depth understanding of industrial processes so that security concepts can be optimally introduced and implemented,” Metzler said. “For many companies, this task has become too complex. They need a partner who is familiar with and has mastered the special requirements of industry and cybersecurity.”
He said that when implementing industrial cybersecurity strategies, challenges include protecting legacy systems that were not originally designed with cybersecurity in mind, ensuring the secure integration of IT and OT (Operational Technology) networks, managing the growing complexity of industrial networks, and addressing the shortage of skilled cybersecurity professionals.
Additionally, companies must ensure that all components, including new and legacy devices, are equipped with robust security functionalities. This includes implementing technologies like industrial firewalls, intrusion detection systems, and secure remote access solutions that are specifically designed for industrial environments. Companies must also balance the need for robust security with the requirement for minimal disruption to production processes and safety systems.
“Beyond technology, the correct handling of cybersecurity measures by personnel is crucial,” Metzler said. “This involves training staff to adhere to defined policies and procedures, such as incident response protocols and regular security audits. A lack of cybersecurity awareness or poor adherence to security protocols by employees can undermine even the most advanced technical defenses. Overall, the shortage of skilled cybersecurity professionals presents a challenge, making it essential for companies to not only invest in technology but also in ongoing training and education for their workforce.”
Critical infrastructure protection
Metzler said that the newest industrial cybersecurity solutions are specifically targeting areas such as critical infrastructure protection, secure remote access for industrial control systems, and the protection of industrial IoT devices. These solutions are also being applied to ensure compliance with stringent regulatory requirements and to safeguard sensitive production data. With the increasing convergence of IT and OT, traditional defense concepts are increasingly reaching their limits. Software-based network management and the use of cybersecurity tools have therefore become indispensable.
To be able to detect potential vulnerabilities in OT networks at any time, Siemens has designed a complementary tool set for plant operators with the SINEC software family. The SINEC Security Inspector determines the security status of individual components or entire production networks. The SINEC Security Monitor analyzes network traffic and detects anomalies through passive, non-intrusive continuous security monitoring. The latest tool in the SINEC portfolio is the SINEC Security Guard, an intuitive cloud-based software-as-a-service that displays vulnerabilities for OT-Assets and enables optimized security management for industrial operators without dedicated cybersecurity expertise. The SINEC NMS network management system also enables centralized monitoring and configuration of networks as well as security through encrypted data communication and local documentation.

“Artificial intelligence and machine learning—tools enabled by the vast power of cloud computing—are where we are headed. The problem is that these solutions are only useful with huge amounts of consistent, quality data from the plant floor,” Dan White, Director of Technical Marketing at Opto 22.
Impact of AI and machine learning
Tools enabled by the power of cloud computing.
Dan White, Director of Technical Marketing at Opto 22 told IEB that “artificial intelligence and machine learning—tools enabled by the vast power of cloud computing—are where we are headed. The problem is that these solutions are only useful with huge amounts of consistent, quality data from the plant floor.”
He added that, in response, automation vendors have developed sophisticated control platforms that not only securely transmit data to the cloud but also ensure its accuracy right from the source. Edge controllers, positioned directly at the data origin, play a crucial role in this process. They filter and process raw data on-site, ensuring only relevant and refined information is sent to the cloud. Using a modern publish/subscribe protocol like MQTT Sparkplug, which also supports SSL/TLS security certificates, companies can rest easy knowing their plant data is getting to the cloud safely and securely.
More data at the edge
“As more data is collected at the edge of the network, from the plant floor and remote equipment, and moved into cloud computing platforms, AI tools and algorithms can make sense of it far more quickly and effectively than humans,” White said. “Finding operational anomalies, predicting equipment failures, and optimizing energy and raw material usage are just a few examples of the benefits.”
For too long, manufacturing networks have been isolated from the outside world. Companies now understand that manufacturing data must be democratized within the organization to unlock cost and efficiency savings. Manufacturing networks need to be reimagined to incorporate secure democratization of that data, which today’s modern edge gateways and PLCs can achieve.
White added that the “cutting-edge” cybersecurity technologies that factory environments are now discovering have been used by IT and internet companies for years. Online banking uses secure SSL/TLS encryption and certificates. VPNs, firewalls, and MQTT pub/sub architectures have existed since the 1990s. So what makes them unique is that factory environments are now embracing them.
“Don’t forget factories have used networks since the 1970s, before Ethernet and the Internet. Those were serial networks and usually proprietary, and we didn’t have great ways to democratize data back then,” White said. “In the 1990s, Ethernet wasn’t even viewed as viable for plant floor operations due to its latency, sensitivity to noise, and nondeterminism. But the new obsession with data—and the not-yet-realized benefits that AI and ML can provide once we have a lot of data to analyze—have led the factory floor to start catching up.”
Primary concerns that automation engineers and companies are facing when implementing industrial cybersecurity strategies fall into a series of categories including support for legacy systems.
“Legacy systems, often characterized by outdated hardware, software, and security protocols, pose significant cybersecurity risks to industrial organizations. These systems were designed in an era when security was less of a concern, leaving them vulnerable to modern attack vectors,” White added.
Lack of Security Features: Most legacy systems lack built-in security features such as zero-trust user authentication, VPNs, firewalls, encryption, SSL/TLS certificate support, and network segmentation. Without security features, they’re easy targets for hackers who can exploit known vulnerabilities.
Vendor Lock-in: Reliance on legacy systems often involves vendor lock-in, which limits the options for upgrading or replacing the system, making it difficult to implement modern security measures.
Limited Scalability: Legacy systems, which typically rely on a poll/response architecture, may not be able to handle the increased data demands of modern IIoT applications, making them more susceptible to failures and security breaches.
As a result, organizations must carefully evaluate the risks associated with legacy systems and develop strategies to mitigate them. These strategies may involve upgrading to more modern systems or using modern edge devices to create a secure layer between OT and IT networks.
Targeted solutions
Application areas that the newest Industrial Cybersecurity solutions are targeting cover a variety of needs for smart manufacturers.
“Let’s look at some of the low-hanging fruit. Right away, we are seeing a huge move toward energy data collection,” White said. “Most companies don’t understand their electric bill or how peak demand charges and variable rates work for their utility. Regardless of industry—from automotive to aerospace and from agriculture to electronics—there’s one thing everyone has in common: they all use electricity. More granular analysis can help firms reduce costs and assign electricity costs to the process that’s using them.”
“After that, I would say operational equipment effectiveness (OEE). By adding a simple edge device onto an existing piece of machinery, which can be done for about $1,000, companies can start to see when and why their factory equipment isn’t running at full capacity,” he added.

“Interestingly the cybersecurity needs in the industrial area seem to be driven by the IT world. Top keywords are asset management, patch management, intrusion detection, security operations center, none of which is specific to the OT environment,” Dr. Lutz Jänicke, Phoenix Contact.
IT solutions moving to the OT world
Implementations specifically targeting the industrial environment are needed.
“Interestingly the cybersecurity needs in the industrial area seem to be driven by the IT world,” Dr. Lutz Jänicke, Corporate Product & Solution Security Officer, Phoenix Contact, told IEB. “Top keywords are asset management, patch management, intrusion detection, security operations center, none of which is specific to the OT environment. Implementations specific to the industrial environment are needed.”
Jänicke said that specialized products for OT are established, like firewalls, remote maintenance solutions, intrusion detection systems. However, the trend is moving away from “security products” to protect the OT world and the future will rather be “secure products”. These follow security by design rules and implement security functions like access control and secure communications instead of relying on add-on products.
“IT solutions are moving into the OT world. A very important topic is the management of cybersecurity in the IT as well as in the OT environment. Connected systems need to be monitored for vulnerabilities, patches and updates need to be rolled out,” Jänicke said. “Accounts needed for authentication and authorization require central management.
Communication security via secure protocols must be supported by centrally managed PKI or similar solutions, as communication does occur between IT and OT. A final ingredient for concepts like zero trust is endpoint security.”
He added that all of these measures need to be implemented in a centralized manner unless in a very large factory an OT specific setup might be possible. If this is not the case, attacks must be remediated in a central Security Operations Center and security management needs to be coordinated between IT and OT. Of course, tooling on the shopfloor might be technically different but its operation needs to be integrated into the overall security management.
Engineering challenges
“Only few automation engineers have a solid cybersecurity background and experience,” Jänicke said. “That makes it difficult to have the necessary ‘holistic approach’ within both cybersecurity and for the automation solution as a hole. Depending on the setup of the company, cybersecurity is typically organized in the IT departments, but both OT and IT need to work together. This often is a significant challenge due to different cultures.”
“However, due to the convergence of IT and OT, IT technologies will move farther into the OT world as will cybersecurity threats,” he added. “Overarching cybersecurity strategies therefore need to integrate both worlds, requiring automation engineers to fully adopt the IT world.”

“The key to effective industrial cybersecurity solutions is the development of resilient network infrastructure based on a defense in depth security approach is critical in ensuring the continuity of operations after any kind of major cybersecurity incident,” Dr. Al Beydoun, ODVA President and Executive Director.
Resilient network infrastructure
Based on a defense in depth security approach.
Dr. Al Beydoun, ODVA President and Executive Director, told IEB that that “the key to effective industrial cybersecurity solutions is the development of resilient network infrastructure based on a defense in depth security approach is critical in ensuring the continuity of operations after any kind of major cybersecurity incident.”
“The greater the number of potential hurdles that any threat actor must overcome increases the odds that a potential incident will be discovered early on and therefore will minimize the potential damage,” Beydoun stated. “Stopping attacks can come in many forms including employee training, physical security, firewalls, switch based deep packet inspection, network segmentation via separate security zones and communication conduits between zones, and end point security that supports zero trust with authentication for each connection. One potential option for automation devices is CIP Security, which provides end point security including device authentication, message integrity, traffic encryption, role-based access, and a device level firewall.”
Beydoun said it’s important to not lean too heavily on any one kind of security system and to have experts available to review logs when suspicious behavior is identified by an automated system. Even the concept of air gapping is starting to unravel with the ability to remotely detect radiation signatures from physical electronic equipment. The significant value provided from taking advantage of edge and cloud connectivity for business optimization combined with the increase in potential threat vectors make defense in depth and zero trust security vital investments for the future.
Zero Trust Approach
He added that adopting a zero-trust approach makes it much more time consuming and difficult for a bad actor to continue to expand privileges and access within a breached network given that each new connection must be authenticated. The addition of role-based access to end point authentication reduces the privileges of a given user and further limits the potential damage a cyber threat actor can inflict.
It is important to make sure that even the most privileged of root and administrative super users still must rely on the zero-trust approach to access confidential data and control potentially dangerous equipment in case their access is compromised. A systemic way to ensure a high level of network security is to rely on the ISA/IEC 62443 cybersecurity standards for industrial automation and control systems. Looking for automation networks that adhere to the security principles of IEC 62443, such as CIP Security, and devices that are certified to IEC 62433 standards is another way to bolster an organization’s defense in depth security approach.
Impact of AI
“One of the newest additions to security is the implementation of Artificial Intelligence systems to look for abnormalities in network traffic to identify suspicious behavior as early as possible,” Beydoun said. “AI systems can see if someone is accessing the network from unexpected locations, outside of normal working hours, or in areas that are not a part of an employee’s job responsibilities. While false positives are sure to come to light from dedicated workers going above and beyond, the early detection of cyber threat actors can significantly limit potential damage caused.”
The advantage of AI systems is that they can crunch vast amounts of data and see when there are deviations outside of the norm in production processes and machinery operations that would be hard to detect by a person. Experts are still required to validate the findings and to determine the next steps that need to be taken. One of the disadvantages of AI systems is that they will need to be redesigned and retrained over time as the networks change given that models are trained to fit a given set of data from a time period in the past. It’s important to note that AI will just be another tool, albeit a valuable one, in securing networks and operations.
Challenges for automation engineers
Beydoun said that controls engineers are tasked with the immense challenge of ensuring that complex networks aren’t compromised in a way that will result in the loss of throughput, quality, or proprietary information. While an automation company must work to prevent a multitude of potential entry points, a bad actor just needs to find one successful way to enter a network.
Once inside the network, whether by phishing for the credentials of a company’s trusted employee or through technical exploits, the cyber threat actor can then choose to stay silent while working to elevate their access privileges, waiting for an advantageous time like a company shutdown to initiate an attack.
A network that may appear to be secure could already be compromised, which has led to the rise of security concepts such as zero trust that always requires verification for each connection. The potential for economic, environmental, or loss of life and limb, combined with the challenge of guarding networks that have a staggering number of potential entry points, has also given rise to the importance of end point security such as CIP Security for EtherNet/IP.
Key applications focus
“Automation applications where misuse can result in harm to employees and environment or seriously jeopardize the economic viability of a company are the most important to protect in case of an cyberattack from a bad actor,” Beydoun said. “Critical application examples that require the most stringent security include metal stamping or rolling equipment, chemical mixers, oil distillation towers, and water treatment plant disinfectant and corrosion control processes.”
He added that it is imperative to utilize zero trust security to protect control devices at the lowest level for vital applications. CIP Security for automation devices offers flexible protection via profiles that can be implemented as needed, allowing for high overhead encryption for critical applications while only using authentication for other less important processes. Security has become a key enabler of automation device to cloud connectivity that is allowing for increases in productivity and growth. Therefore, security policy, training, and protections are an invaluable investment in the future of industrial operations, especially as security threats continue to grow and evolve.
“Implementing cybersecurity strategies is a very involved process. These strategies need to consider the entire landscape of the network including local networks as well as the integration of remote sites. Everything needs to be considered in a layered approach,” Mike Willet, Network Engineer, Red Lion.
Flexible hardware solutions
Integrate local networks and serve as hub of automation network.
Mike Willet, Network Engineer for Red Lion said that a “key technology trend is implementing hardware that can serve many purposes in the landscape of the topology, security and the overall industrial network.”
He cited FlexEdge from Red Lion as a key product that can be used as a firewall to secure the edge of the network, connect remote sites securely, integrate the local networks and also serve as the hub of the automation network with Crimson.
“It is an overall solution that can be the focal point of the industrial network. Red Lion is addressing these concerns with products like FlexEdge and NT5000 switches to build out the industrial network,” Willet said.
Industrial cybersecurity solutions
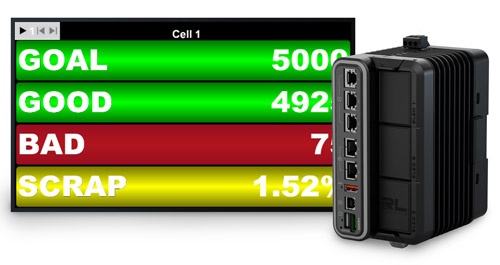
The FlexEdge Intelligent Edge Automation Platform from Red Lion is powered by the company’s Crimson Configuration Software.
Willet said that new solutions can offer advancements to security for industrial networks. Users can have the ability to better secure entry and exit points into the industrial network and also keep the local segment of the network secure. New solutions can also empower industrial network users and administrators to manage the industrial network and maintain better insight into monitoring and ongoing status of the network.
“When Red Lion products are implemented into the industrial network, users can build out a new solution for cyber security with the ease of use and functionality that the devices bring. When a FlexEdge device is installed as a firewall and automation device with Crimson, it can also monitor NT5000 switches using N-View and port statistics can be mapped to tags to view and build alarms,” Willet said.
“This solution can build a secure network with the advantage of passive monitoring to gain insight into the health of the network. Manufacturing networks can benefit from this because they can implement a secure network properly and gain the added benefits of a secure network with the ease of use factor of Red Lion products.”
Cybersecurity strategies
“Implementing cybersecurity strategies is a very involved process,” Willet said. “These strategies need to consider the entire landscape of the network including local networks as well as the integration of remote sites. Everything needs to be considered in a layered approach. So, with all of this comes quite a bit of planning.”
During the implementation of the security plan all the outside or untrusted traffic must be defined and properly secured for specific inbound or outbound connections and protocols. Also, the local and private side of the networks where end devices are connected must also be properly secured. So, the overall concerns could emerge in the development stage of the security implementation plan itself and during the configuration stage of the firewalls, routers, switches and other devices in the network. It is critical to implement the proper security measures and if Red Lion products such as FlexEdge and NT5000 switches are implemented into the network the ease-of-use factor can be very helpful while building the foundation of the network.
He added that security at various points and areas in the network is very important. Targeting the edge segments of the network are crucial because those areas are often connected to public networks and are usually connecting various sites together.
“It is important to maintain security at those points because those are the main entry and exit points from untrusted sources. But it is also important to build out a security architecture throughout the entire network,” he said. “Making sure that the network switches connected downstream in the network that are connecting end devices have the proper security measures in place is also very important.”

“One major trend is the adoption of horizontal standards like ISO/IEC 27001, NIST CSF, and IEC 62443. They provide a structured framework for cybersecurity, bridging the gap between IT and OT requirements.” Laurent Liou, Product Marketing Manager, Cybersecurity at Moxa.
Structured framework for cybersecurity
Standards including ISO/IEC 27001, NIST CSF, and IEC 62443.
“One major trend is the adoption of horizontal standards like ISO/IEC 27001, NIST CSF, and IEC 62443,” Laurent Liou, Product Marketing Manager, Cybersecurity at Moxa told IEB recently. “They provide a structured framework for cybersecurity, bridging the gap between IT and OT requirements. Vendors like Moxa incorporate these standards into their solutions, ensuring compliance with regulations while aligning with industry best practices.”
Liou said that another trend is the integration of best practices directly into cybersecurity solutions. For instance, Moxa’s adoption of IEC 62443 enhances the security of industrial control systems by addressing their unique challenges. This helps organizations build a robust cybersecurity posture that meets both regulatory and operational demands.
Advanced security features are also becoming more prevalent. Modern solutions offer features such as network segmentation, real-time traffic inspection, and secure communication protocols. They protect manufacturing networks from diverse cyber threats while maintaining operational efficiency.
“Lastly, there is a growing emphasis on embedding security measures directly into the network infrastructure. Moxa focuses on foundational elements like authentication, access control, and segmentation, enabling a robust defense-in-depth strategy. This approach ensures that security is not an afterthought but a core component of the network design, enhancing overall resilience,” Liou added.
Impact on manufacturing networks
“New industrial cybersecurity solutions offer significant benefits, particularly in terms of regulatory compliance and operational resilience,” Liou said. “By adopting horizontal standards like ISO/IEC 27001 and IEC 62443, organizations gain clarity and structure in implementing cybersecurity measures. These standards simplify compliance, helping organizations navigate complex regulatory landscapes more effectively.”
One of the key benefits is the adaptation of these solutions to the specific needs of operational technology (OT) environments. For example, Moxa’s IEC 62443-certified solutions are designed to meet the unique requirements of industrial control systems (ICS), ensuring that security measures are relevant and effective in these settings.
Another major advantage is the ability to maintain operational continuity while enhancing security. Moxa’s solutions incorporate redundant network architectures, which allow for secure maintenance and upgrades without disrupting critical operations. This approach is vital for managing risks and ensuring continuous availability in industrial environments.
Furthermore, integrating foundational security elements directly into the network infrastructure provides a solid base for additional security measures. Moxa’s solutions reduce the attack surface and support a comprehensive defense-in-depth strategy, which is crucial for improving the overall resilience of manufacturing networks.
New solutions offer a structured approach to cybersecurity, tailored to the needs of industrial environments, while ensuring continuous operations and enhancing overall network security.
Cybersecurity technologies
“Cutting-edge cybersecurity technologies distinguish themselves by integrating advanced security features directly into the network infrastructure, particularly in industrial environments,” Liou said. “These features include secure communication protocols, robust access controls, and real-time traffic inspection, all of which are designed to protect operational technology systems from a wide range of cyber threats.”
A critical component of these technologies is network segmentation and redundancy. By creating isolated network segments and utilizing redundant pathways, these solutions help mitigate the impact of potential breaches. For instance, Moxa’s IEC 62443-compliant devices are engineered to ensure continuous operational availability even in the event of a cyber incident. This segmentation also supports secure maintenance and upgrades by isolating changes from critical operations.
Lious said that another defining characteristic is the defense-in-depth approach. This strategy involves multiple layers of security controls, starting with foundational measures like network segmentation and secure communication protocols. Moxa’s solutions enhance this foundation with additional protective layers to address various attack vectors, reducing vulnerabilities across the network.
Performance and availability are also prioritized in these advanced solutions. Moxa designs its technologies to integrate security measures without compromising network efficiency, ensuring that manufacturing operations remain smooth and uninterrupted. This balance between performance and security is crucial for maintaining high productivity levels while safeguarding against cyber threats.
Primary customer concerns
The European Union’s NIS2 Directive and Cyber Resilience Act (CRA) imposes strict cybersecurity requirements, especially for critical infrastructure. Navigating these regulations can be overwhelming, particularly when considering the additional guidelines issued by organizations like ENISA (European Union Agency for Cybersecurity) and sector-specific bodies like EMSA and ENTSO-E.
Moreover, national laws such as Germany’s IT Security Act 2.0 further complicate the landscape by adding country-specific obligations. These regulations often require the integration of various industry standards, like IEC 62443, which focuses on OT security. Compliance with these standards is essential for addressing disaster recovery, safety, and secure communication protocols within industrial environments. Another major concern is maintaining operational continuity while implementing new security measures. Enhancing cybersecurity often necessitates significant changes to existing OT systems, which can disrupt operations. Ensuring that these measures integrate seamlessly without compromising performance or availability is a critical and resource-intensive task.
Automation engineers must navigate a multifaceted regulatory landscape, align with multiple standards, and ensure that cybersecurity measures do not disrupt ongoing operations, all while adapting to the specific needs of industrial environments.
Industrial cybersecurity solutions
“A primary focus is securing OT environments, which include industrial control systems (ICS) and other critical industrial networks,” Liou said. “Moxa’s IEC 62443-certified solutions are specifically designed to protect these systems from cyber threats while ensuring they operate efficiently and reliably. This is essential for industries where the integrity and availability of control systems are paramount.”
Sectors such as energy, water, and transportation face stringent regulatory requirements, and Moxa’s solutions help organizations in these industries achieve compliance while protecting essential services from cyber threats. These solutions are particularly important for maintaining the security and reliability of critical systems.
Additionally, Moxa’s solutions simplify compliance management by aligning with horizontal standards like ISO/IEC 27001 and IEC 62443. This alignment helps organizations manage cybersecurity risks more effectively and streamline the compliance process, which is crucial in regulated industries.
“By focusing on these application areas, Moxa’s industrial cybersecurity solutions enhance overall security, ensure regulatory compliance, and protect critical systems from evolving cyber threats,” Liou said. “These solutions provide a comprehensive and integrated approach to cybersecurity, supporting both operational resilience and regulatory adherence in complex industrial environments.”


