TechnologyMay 30, 2021
Reboot network security to enable digital transformation

Digital Transformation in manufacturing can deliver business value by improving operations and using innovative services. The greatest risk lies in the manufacturer’s ability to secure the production environment and the end-to-end connectivity between the plant and the cloud-based services and remote users.
Security risks and threats to industrial environments have not abated in 2020 and into 2021, but have continued with vigor. The impact includes significant loss of production availability and effort expended to identify and respond to these compromises. These are not new challenges, but the pandemic and its effects certainly have not reduced or remedied the situation.
As operations continue to drive further convergence with IT and OT, and look to improve operational efficiencies and productivity with new market trends and capabilities, such as cloud; they also need to consider a comprehensive multifaceted security approach at the core of the architecture. Security attacks and events are a board-level concern for most, if not all, major industrial operators, given the impact of lost revenue, costs and impact to reputation.
Even before the drastic changes we saw in 2020, manufacturers were under pressure to improve operational efficiency through digital transformation. While investments in digital transformation pay dividends, they also compound long-standing cybersecurity risks. When manufacturing operations are digitized and interconnected, there’s more potential exposure and a greater need for forward-looking protection. After all, a single cybersecurity incident can drive downtime and revenue loss, rack up operational expenses and damage a manufacturer’s reputation in the market.
And yet, even as cybersecurity continues to remain a board-level concern, many manufacturers continue to address the risks with patchwork approaches. Security can’t be achieved with point solutions. It takes an end-to-end approach starting with the network in production. But it does not end there: as digital transformation requires the integration of production environments with cloud-based applications and resources.
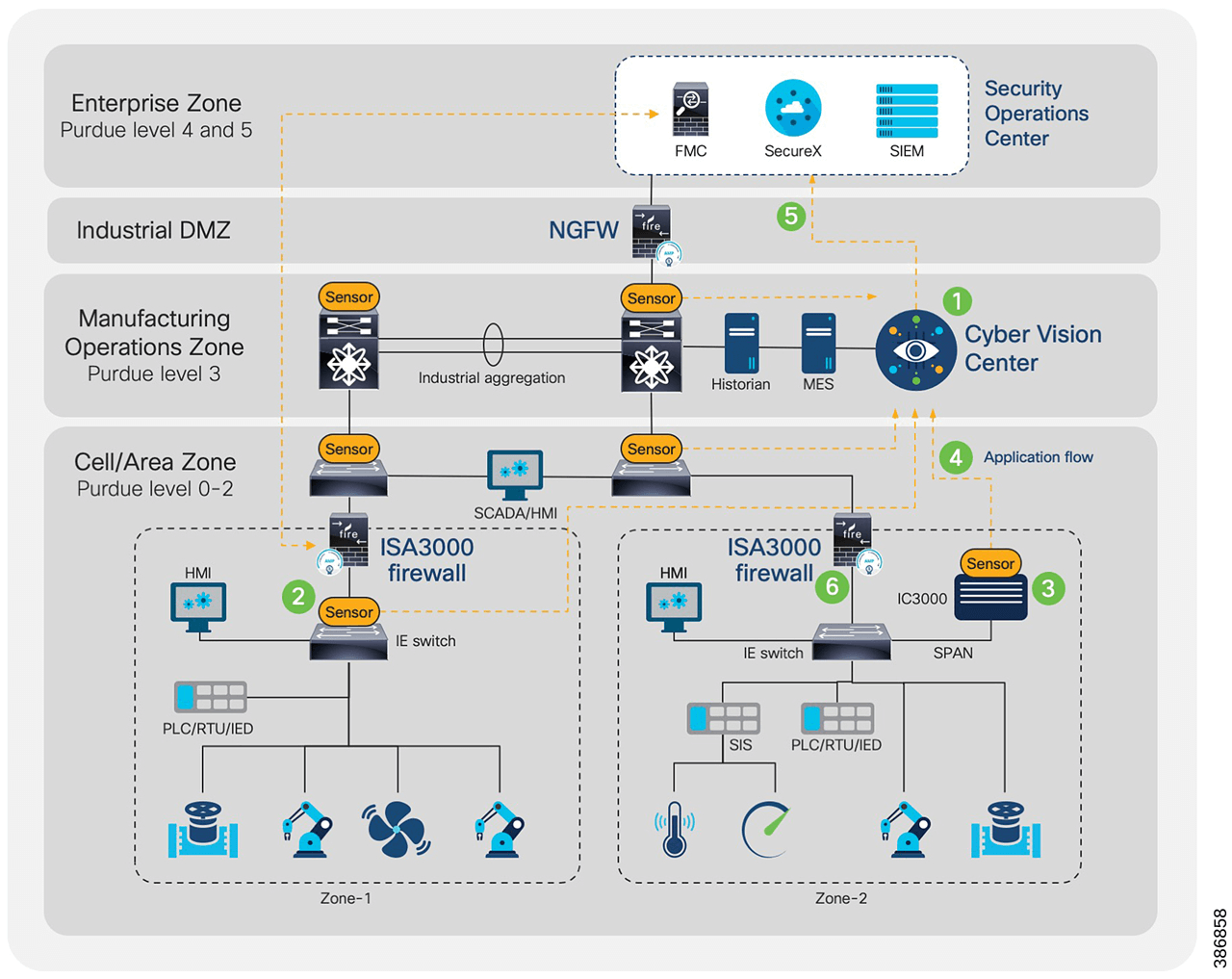
This diagram depicts a manufacturing architecture that includes security controls and applications throughout all layers of the architecture.
Yes, there are some excellent cybersecurity tools designed especially for operational technology (OT) environments. They promise to identify devices and their communication patterns, thereby surfacing cybersecurity risks. But these tools are only as effective as the network they’re monitoring. Legacy networks often make it complex to gain the needed visibility and impossible to automate application and enforcement of security policies. And adding a cloud-perspective requires extending the cybersecurity envelope further.
To enable secure digital transformation, manufacturers need to reboot production network security, embracing a concerted more integrated security strategy and extending those security capabilities beyond the four walls of the operation. This journey starts with the transformation of legacy production networks and introducing hardware and network components that fully enable and efficiently leverage available cybersecurity tools.
Once the planning and design is complete, the next step is to deploy industrial cybersecurity to protect the production network. Digital transformation often introduces remote or cloud-based resources and applications, so the cybersecurity considerations must also include the extended cloud environment, helping ensure end-to-end protection. As an example, the following diagram depicts a manufacturing architecture that includes security controls and applications throughout all layers of the architecture.
Switching for security
For any manufacturer, the production network is the foundation of a secure and reliable production environment. The network should provide security tools with seamless access to production systems and their communications, without interfering with the operation. With the proper network hardware and software, security tools can serve as security “eyes and ears” – sensing and analyzing industrial automation and control systems (IACS) devices and communications at the edge. What’s more, the security tools should be able to perform that work without placing undue burden on the network itself.
As it does in enterprise networks, a robust security strategy in the production network can also play a critical defensive role. With access to IACS devices and communications, OT security tools can help “profile” device behaviors and communication flows. Manufacturers can use these profiles to develop security policies, which can later be enforced via the network infrastructure.
Using those same profiles, software can apply dynamic network segmentation – making it easy to protect a flat industrial network from anomalous communication flows and malicious traffic.
Of course, transforming an existing network is not a trivial undertaking. Given the 24/7/365 operational tempo of many production environments, there is significant risk if a migration is poorly executed. Before displacing any existing network devices, manufacturers need to perform sufficient planning, testing and preparation to reduce potential downtime (planned and unplanned). This includes the development of a backout strategy, should a migration experience obstacles hindering its timely completion; as well as, establishing the success criteria for a migration with the associated checks and validation.
When planning a transformation, start with a thorough understanding of all requirements for the applications and services the production network supports. Dive deep into all protocols and associated KPIs and metrics required by the deployed endpoints and analyzing industrial automation and control systems (IACS) devices, many of which tend to be sensitive to network latency and loss. Once the requirements are well understood, it’s possible to develop role-based templates and network device configurations. These configurations will reflect the protocols and features necessary to support deterministic behavior, application SLAs and current device connectivity.
After the device configurations are developed, the next step is testing and validating the viability of those configurations in the new switches. This can be achieved by executing a limited proof of concept in a controlled “sandbox” or by testing within a limited production environment. In either case, the key is to execute tests and expose the equipment to the rigors and network characteristics found in the operational environment while reducing any impact to operations. Using clear pass/fail criteria for each feature, validates requirements are being met and that the network performs as expected. After completing all tests – and resolving any punch-list items – it’s time to displace the legacy switches.
Different situations and operations may dictate how the displacement or migration needs to be executed. This, too, requires strict planning and preparation. To properly execute the migration and help ensure successful repeatability for subsequent devices, create a standard operating procedure (SOP) or methods of procedure (MOP) document. This document defines the step-by-step process and correct sequence for performing the necessary tasks. As such, it helps mitigate risk and reduces impact to operations – by defining not only the proper procedures for executing the displacement, but also the backout procedures should something unexpected be encountered.
To further contain costs and impact, default to reusing existing cabling and power, which usually represent the most significant cost and time to deploy a production network. Using existing power and network cable-plant helps reduce the time required to swap network infrastructure hardware.
While manufacturers often possess the staff and experience in performing these tasks, resources may be spread thin. In that case, consider investing in a service contract from a reputable vendor as a force multiplier, mitigating risk and helping drive success. A service team can take responsibility for some or all of the tasks discussed to help achieve the desired outcome, such as reducing operational downtime and/or reducing costs and keeping the project on schedule.
Integrated industrial cyber solutions
Once a legacy network is displaced with a security-capable network infrastructure, manufacturers can move more readily on the journey to secure production environments. With the necessary hardware and software, a manufacturer can accelerate the deployment of cybersecurity solutions that lead to more uptime, secured assets and products, and ultimately decreased operational risk.
Here are five ways to start:
- Deploy an industrial demilitarized zone (iDMZ) between the operational zone and enterprise applications.
- Monitor IACS devices and communication and identify risks. Leverage cybersecurity applications such as Cisco Cyber Vision to analyze data collected by the new network equipment to gain ubiquitous visibility.
- Leverage a tool such as Cisco Cyber Vision to profile industrial devices, group them into production cells and define security policies between those cells.
- Monitor communications between production cells to confirm that security policies are properly defined and can be enforced without compromising production.
- Deploy security policies to be enforced by the new industrial network and provide ongoing improvements with a network management solution, such as Cisco DNA Center.
Integrate these steps with other key cybersecurity initiatives that rely on the transformed production networks. These may include policy management, secure remote access, enhanced industrial demilitarized zones, malware protection throughout the environment, and intrusion detection and prevention (IDS/IPS) at key conduits within the production zone.
The current fragmented cybersecurity approach in industrial environments is not keeping pace with the rate and sophistication of threats and attacks. To avoid downtime, revenue loss and reputational impact, manufacturers should consider transforming legacy production networks and migrating to a more capable infrastructure.
As an example, the Cisco Catalyst IE3x00 series together with Cisco Cyber Vision provides deep insights and visibility of IACS devices and communication patterns. This approach also enables segmentation and defense tailored to the existing IACS by leveraging increased visibility to derive tailored cybersecurity profiles. These profiles can later be used to define and instantiate security policies.
With a modern network and more integrated security tools and features, manufacturers can expect to upgrade and deliver a more comprehensive and cohesive cybersecurity posture throughout the lifecycle of the IACS and production networks.
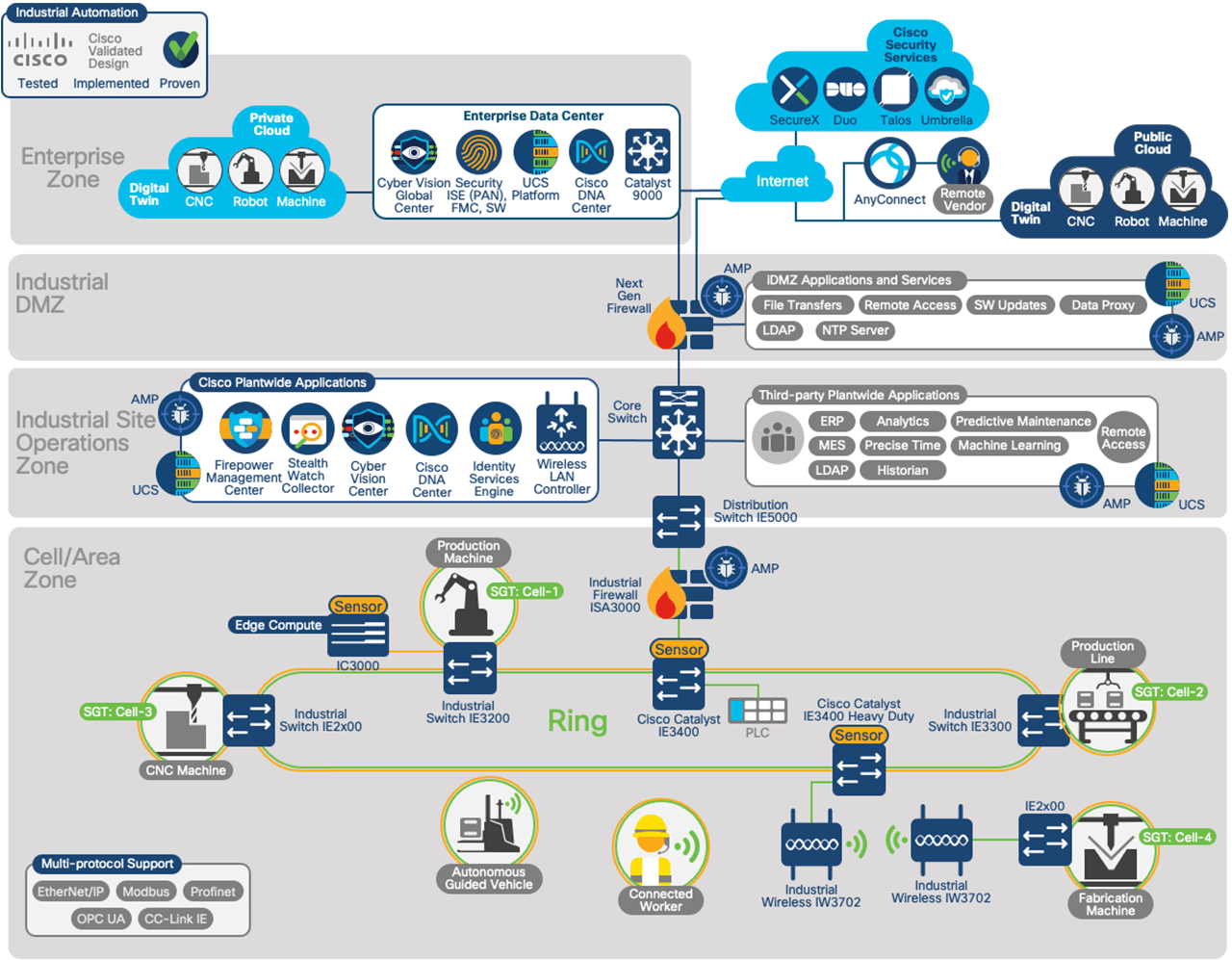
Integrating Industrial Cybersecurity tools at all levels of the network provides not just visibility of the IACS devices, systems and communication but also leverages that knowledge and insight into dynamic and automated policy management and enforcement.
Extending Security to the Cloud
Digital Transformation and leveraging more modern network capabilities to drive efficiency or produce a competitive advantage can be a significant differentiator for a manufacturer. Providing connectivity and access to remote experts, or OEMs pulling telemetry data from critical equipment for predictive maintenance, or even leveraging new services and applications hosted by an ecosystem partner off-prem, all extend the threat landscape, and potentially expose the operation to more risk. Therefore, when embarking on newer initiatives, and extending connectivity beyond the four walls of the operation, such as cloud services, security needs to remain at the core of any solution.
Cloud, and how to leverage the benefits and capabilities it offers, is absolutely a consideration for most industrial operators. Cloud-based services can be achieved via different means. In some instances, cloud connectivity can be achieved via direct connectivity between an operator and a cloud provider. In other cases, communication may rely upon open internet services. With both these options, each presents its own set of unique challenges. However, protecting that communication, resources and application availability are critical to help ensure services remain operational and protected from risks and threats.
It should be noted that services and applications placed in the cloud should be evaluated for their criticality to the continuity of operations. Cloud-based services should be considered a noncritical extension of the operation, and therefore only include applications that are considered unnecessary to ongoing production if connectivity is lost for periods of time.
However, securing the cloud infrastructure is equally as important as securing on-prem networks. Many of the same security strategies and tools leveraged on-prem, may need to be employed in the cloud. Key considerations when considering security for the cloud can include:
- Perimeter security, macro-segmentation and stateful inspection and visibility of applications and flows transitioning to and from the cloud.
- Confidential communication via encryption protects cloud-based and on-prem communication and traffic flows with site-to-site VPN connectivity, or secure individual client connectivity.
- Use of multi-factor authentication technology to verify the user identity before granting access reduces the risk of compromised passwords and help ensure only appropriate users are granted access to the network.
- Adding protection against malware and viruses propagating into production environments from cloud-based and external sources with anti-malware protection built into a production environment’s network infrastructure and application servers.
- Ensure systems residing in the cloud are regularly patched and updated and users are accessing the appropriate services with DNS protection.
Consider a scenario where an operator is interested in providing connectivity to a third party OEM or partner, who would like to pull telemetry and usage data from machines and other onsite hardware for the purposes of predictive maintenance. Extracting telemetry into the cloud may be one way of addressing this use case. By leveraging the right combination of security features and applications previously mentioned, this use case can be accomplished without putting the operation at additional risk while providing additional cost savings and operational efficiencies.
As the Industrial Digital Transformation starts to rely on cloud-based services and capabilities, manufacturers could also leverage cloud-based security services to increase visibility, accelerate detection of threats and compromises, as well as speed reactions and responses to those threats. The demarcation point between critical and noncritical assets does not have to exist on-prem. In addition, this model allows for the centralized enforcement of security policies, which promotes consistency, and repeatability, and facilitates the on-boarding of additional sites, as an operator looks to scale out this method of connectivity. This may be important for operators considering driving more onsite automation and managing multiple operations from a regional operations center (ROC). A regional iDMZ between operational zones and the enterprise would enable:
- Cybersecurity workflows and automation of Security Orchestration services to simplify, integrate, automate and scale security operations
- Coordinated visibility and insights across multiple locations from a single security operations center hosting extended detection and response (XDR) tools.
- Enforcing consistent security policies across multiple operational zones.
- Ease of administrative burden and the potential to be delivered as a service by a managed service provider.
Summary
To summarize, the promise of Digital Transformation in manufacturing delivers significant business value through improved operations, better services and products and creating and using innovative services. The greatest risk to achieving those benefits lies in the manufacturer’s ability to secure the production environment and the end-to-end connectivity between the plant and the cloud-based services and remote users. Three key steps we outline to overcoming those cybersecurity challenges include:
- Reset the cybersecurity foundation in production environments by accelerating adoption of modern network infrastructure that provides key visibility and security for Industrial Automation and Control systems
- Integrate the deployment of Industrial Cybersecurity tools to provide not just visibility of the IACS devices, systems and communication but also leverage that knowledge and insight into dynamic and automated policy management and enforcement.
- Protect the cloud-based and on-prem assets, as well as the communication flows between the production environment and cloud-based applications and services with a holistic security strategy, comprised of a robust set of cybersecurity technologies and tools.
Paul Didier, Kevin Turek and Andrew McPhee, Cisco Systems