TechnologyFebruary 2, 2021
Securing industrial networks: There must be a better way!
Your industrial network can now help you deploy IoT/OT security at scale in a much easier and cost-effective way. Unique edge computing security architecture capabilities bring the simplicity and cost saving benefits industrial organizations are looking for when deploying OT security at scale.
With operational environments increasingly digitalizing and connecting to the IT environment, industrial organizations are recognizing the need to protect operational technology (OT) and industrial IoT against cyberattacks.
Deploying firewalls to build a demilitarized zone (DMZ) between industrial networks and the IT domain is the mandatory first step. But as organizations connect more devices, enable more remote access, and build new applications, the airgap erodes and falls short of being sufficient.
Security solutions designed for industrial networks typically monitor network traffic to gain visibility on assets, behaviors, malicious activities, and threats. The process of evaluating and testing these solutions initially tends to go well – after a successful proof of concept, industrial organizations begin to deploy at scale. That’s where they begin to run into issues.
Often, it’s cost prohibitive for organizations to buy the number of security appliances they need to cover their entire operational environment. Or the networking team doesn’t have the resources to deploy, maintain, and manage a fleet of security appliances.
Traffic mirroring that is required to feed these appliances would likely necessitate a separate network, and would also require the resources to deploy, maintain, and manage it. In many deployments the added cabling cost for the separate network itself far outweighs the entire cost of the security solution.
Visibility and detection built into the network infrastructure.
Visibility of operational network
When organizations attempt to secure their IoT/OT network, they encounter two primary issues:
- A lack of visibility: As industrial networks can be quite old, widely dispersed, and involve many contractors, operators often don’t have an accurate inventory of what’s on the network. Without this, they have limited ability to build a secure communications architecture.
- A lack of control: A lack of visibility also means operators are often unaware of which devices are communicating to each other or even of communications reaching industrial devices from the outside. You cannot control what you don’t know.
The first step, then, to securing an IoT/OT network is to obtain visibility. You need to understand what devices are on the network, what they are communicating, and where those communications are going.
The technology to achieve network visibility is available today. Deep packet inspection (DPI) decodes all communication flows and extracts message contents and packet headers, providing the visibility to understand what devices you need to secure, and the policies required to secure them.
DPI allows you to gather device information such as the model, brand, part numbers, serial numbers, firmware and hardware versions, rack slot configurations, and more. It also allows you to understand what is being communicated over the network. For example, you can see if someone is attempting to upload new firmware into a device or trying to change the variables used to run the industrial process.
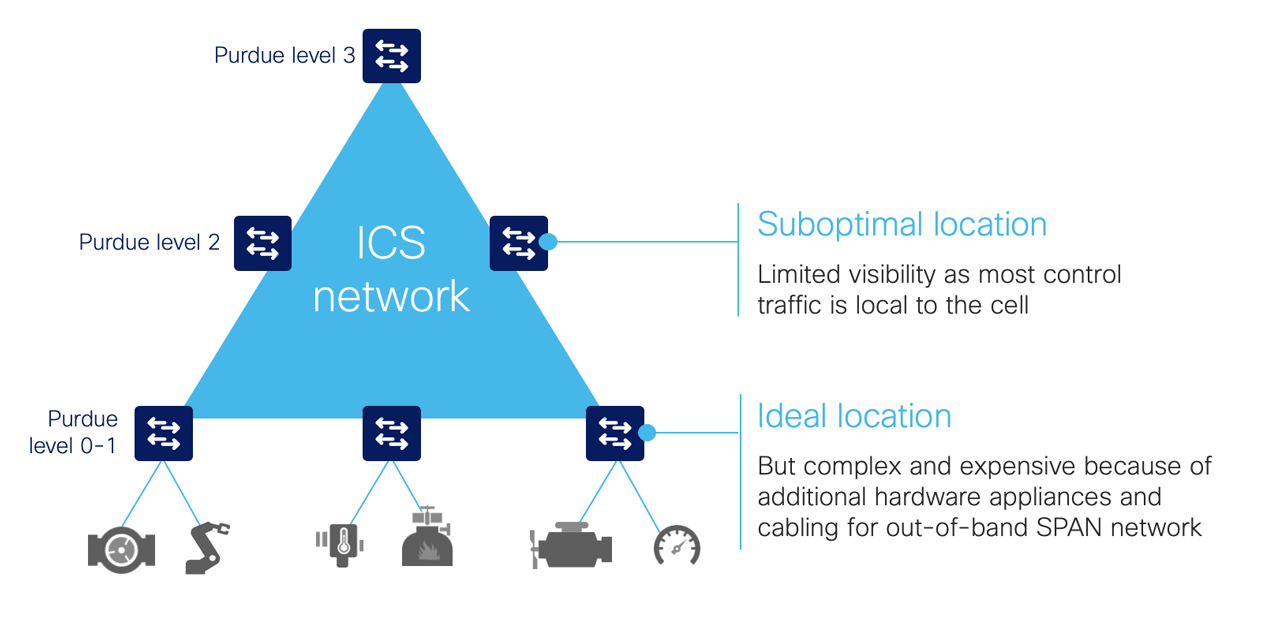
To achieve complete visibility, all network traffic must be inspected. It’s important to note that in an industrial network, most traffic occurs behind a switch at the cell layer where the machine controllers are deployed. Very little traffic goes up to the central network.
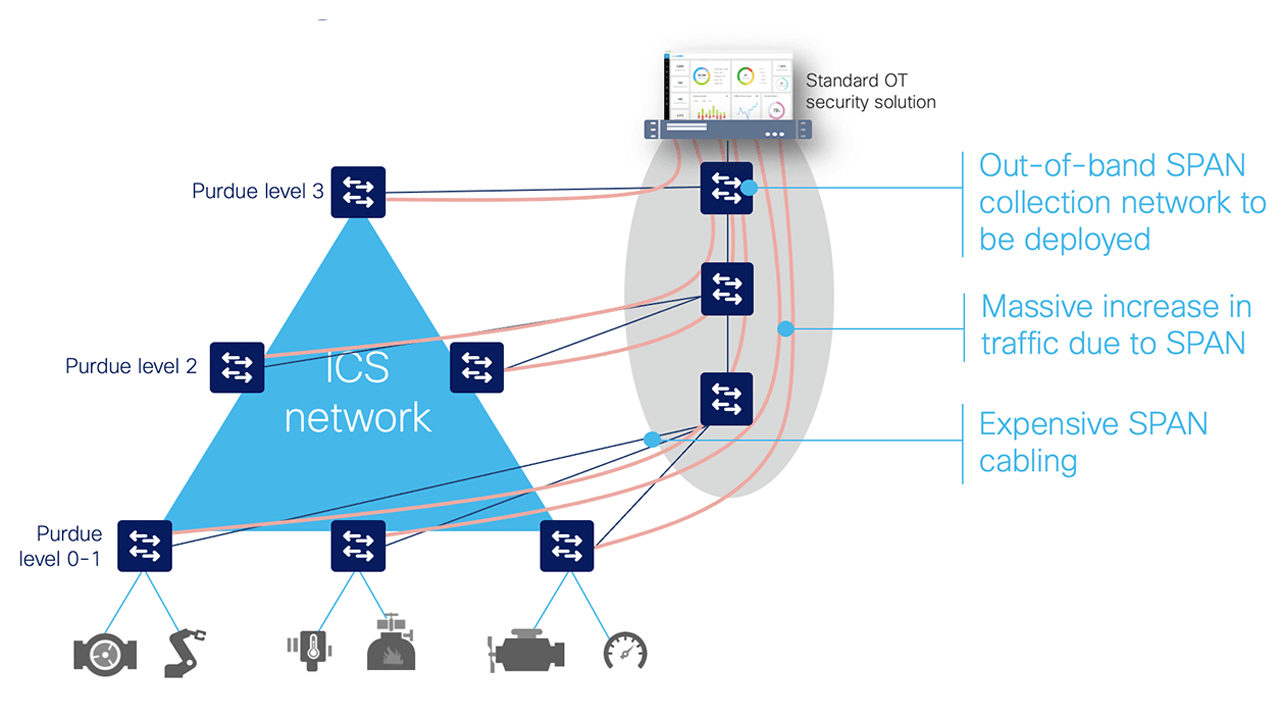
When collecting network packets to perform DPI, security solution providers typically configure SPAN ports on network switches and employ one of three architectures:
- Mirror all traffic to a central server that performs DPI
- Deploy dedicated sensor appliances on each network switch
- Mirror traffic to dedicated sensor appliances deployed here and there on the network
Visibility and detection built into the network infrastructure.
Monitor IoT/OT networks via SPAN
While these approaches deliver network visibility, they also create new challenges. Configuring network switches to send traffic to a central server requires duplicating network flows. A new out-of-band network will generally be needed to transport this extra traffic, which can be complex and costly. Although this can be acceptable for a very small industrial site, this cannot be seriously considered in highly automated industries generating a lot of ICS traffic (such as manufacturing), or when devices are widely spread in locations with no or poor network connectivity (oil and gas pipelines, water or power distribution, etc.).
Connecting sensor appliances to network switches addresses the issues associated with duplicating network traffic. The appliance collects and analyzes network traffic locally and only sends data to a server for additional analysis. However, installing, managing, and maintaining dedicated hardware can quickly lead to cost and scalability issues. And because most industrial traffic is local, gaining full visibility requires deploying appliances on each and every switch on the network, raising cost and complexity to intolerable levels.
Some technology providers attempt to address this problem by leveraging remote SPAN (RSPAN). RSPAN allows you to duplicate traffic from a switch that doesn’t have a sensor appliance to a switch that has one.
While this approach reduces the number of appliances required to provide full visibility, it still increases the amount of traffic going through the industrial network. Traffic is multiplied because you’re duplicating traffic to SPAN it to a remote switch. And the more traffic on the network, the slower it becomes, resulting in jitter — often an unacceptable compromise in industrial networks where processes need to run faster and machines must be timely synchronized.
Alternatives to SPAN
Instead of SPAN, organizations can use network TAP, port aggregators, or virtual switches, but these alternatives come with a few caveats of their own: 1) organizations must still source and deploy dedicated appliances, 2) configuration and management aren’t necessarily easy, and 3) sending traffic to the OT security platform requires an out-of-band network to avoid impacting the production network.
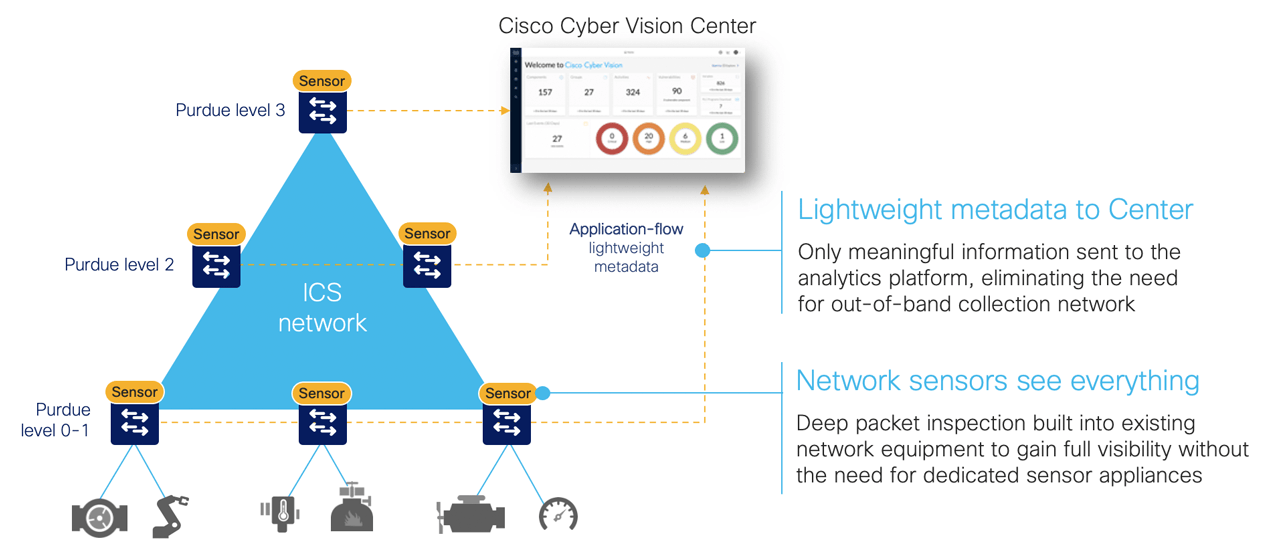
There is a better way to achieve full network visibility: embed DPI capability into existing network hardware. An industrial-grade switch with native DPI capability eliminates the need to duplicate network flows and deploy additional appliances. Obtaining visibility and security functionality is simply a matter of activating a feature within the network switch, router, or gateway. Cost, traffic, and operational overhead are all minimized.
A DPI-enabled switch analyzes traffic locally to extract meaningful information. It only sends lightweight metadata to a central server, which runs the analytics and anomaly detection. This additional traffic is so lightweight (3-5% of general traffic), it can be transferred over the industrial network without causing congestion or requiring extra bandwidth.
Embedding DPI in network equipment affords both IT and OT unique benefits. IT can leverage the existing network infrastructure to secure industrial operations without having to source, deploy, and manage additional hardware.
Because these network elements see all industrial traffic, embedded sensors can provide analytical insights into every component of the industrial control systems. As a result, OT can obtain visibility into operations that it has never had before.
However, not all network equipment can support the embedded sensor feature. Gaining visibility on these local communications will require hardware sensor appliances. Beware that not all appliances are created equal – to maintain the benefits of not deploying a SPAN architecture, these appliances should 1) be centrally managed (so they are easy to deploy and maintain), 2) have limited analytics features (so they can run on low-cost hardware), and 3) only send metadata to the central console (so they don’t need extra network resources).
Gaining the visibility that will enable a truly effective IoT/OT threat detection strategy requires capturing network traffic at the cell layer. Leveraging edge computing to embed deep packet inspection in network equipment enables comprehensive visibility.
With its wide range of industrial switches, routers and gateways running Cyber Vision, Cisco offers unique edge computing security architecture capabilities that bring the simplicity and cost saving benefits industrial organizations are looking for when deploying OT security at scale.


