TechnologyJanuary 23, 2025
To harness the power of AI, tackle the first mile
Out of the box solutions move data easily and securely from operations to IT. IT specialists don’t always grasp the needs and challenges of their counterparts in OT. To align their needs and objectives with IT, they need surer footing to navigate today’s cybersecurity requirements and quality solutions to bring to the table.
State regulations required a major pulp The trade journals are abuzz with talk of Artificial Intelligence (AI) for industrial applications. AI platforms help tie together, analyze, and contextualize data from every corner of an enterprise. They give organizations a big picture view of how their business is performing. They drive value by empowering people in various parts of the organization to make decisions benefiting the business.
That buzz is heard in factory control rooms, head offices, and boardrooms, too. Industrial enterprises are busy figuring out what problems they can solve with AI to add value. The sales office wants new efficiencies for handling orders, shipping, and purchasing. Facilities management wants AI to improve plant safety and product quality. Accounting wants to reduce costs and eliminate waste. Line operators want to optimize forecast maintenance to ensure maximum uptime.
Before AI, these process improvements were hard to identify. Decision-makers had to sift through heaps of data manually or compare outcomes across a range of programs to find efficiencies and places to optimize. Now, modern AI systems can collect and analyze data quickly – even on the fly. They’re designed to deliver powerful results quickly. As such, they can be easy investments to make and justify. Information Technology (IT) departments are right to be enthusiastic about their potential.
There’s just one problem. To leverage the full benefit of AI, you need the proper foundation. You need data from every part of your operation, including foundational systems. That includes data from your factory floor, your remote stations, your legacy equipment. You need data from the all-important first mile of your industrial process.
Crossing the foundational first mile
Purdue Model diagram.
For many organizations, these applications and control systems have been in operation for a long time – 10, 15, 25 years or more. Acquiring data from these systems can be a challenge.
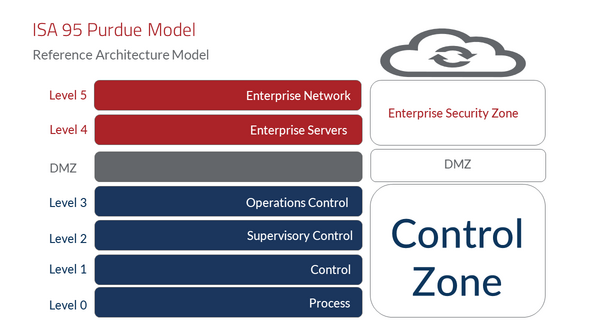
In principle, it’s not the age of the equipment. Even modern facilities have a first mile that needs crossing. To illustrate, consider the six-layer Purdue Model, an established blueprint for building secure industrial control systems.
The architecture is divided into six layers: a lower “Control Zone” which comprises the most critical OT functions, and an upper “Enterprise Security Zone, which consists of two layers for IT functions. The two areas are separated by a protective barrier, called the Demilitarized Zone (DMZ).
The first mile covers Levels 0-2 This is where an organization measures its flow of oil or gas, the amount and pressure of water going through pipes, or the number of widgets passing by a counter.
Process systems, such as motors and sensors, are at Level 0. Control systems, such as Programmable Logic Controllers (PLCs), are at Level 1. Human supervisory systems enter the system at Level 2, such as the SCADA systems that operators and decision-makers use. Level 3 is for operations control systems. These systems gather data from the levels underneath and sent it through the DMZ to the IT layers above.
AI capabilities lie in the DMZ, on Level 4, which comprises databases and servers, and Level 5, for networking and cloud connectivity. The AI application might be on a server managed by the IT department (DMZ or Level 4), with its own data models and machine learning algorithms. Or it could be in the cloud, with data models drawing information from other systems through the organizations. Processes at the Enterprise levels perform top-level analysis to connect the dots across the organization. They’re plugged into accounts payable, accounts receivable, and order processing, to contextualize the data and make decisions that benefit the organization.
Securing the first mile – right out of the box
Whether you’re running antiquated machines or brand-new equipment, data from below needs to move to enterprise levels above. But it needs to move securely, reliably, and with high data integrity.
As an example, let’s say a plant has a widget production line with a rate counter that’s been running smoothly for 15 years. The production line communicates with the rate counter through an Input/Output (I/O) device using Modbus TCP/IP. Now the plant wants to push this count data upstream for use in leading-edge AI applications, but the Modbus communication protocol doesn’t meet modern security standards. Data sent over a network via Modbus runs the risk of being changed or compromised. At the same time, the organization has no desire to change its current application.
By plugging in an intelligent automation platform to connect the plant to their data, the plant can shield its existing application without changing the existing setup.
The first mile: your deepest defense
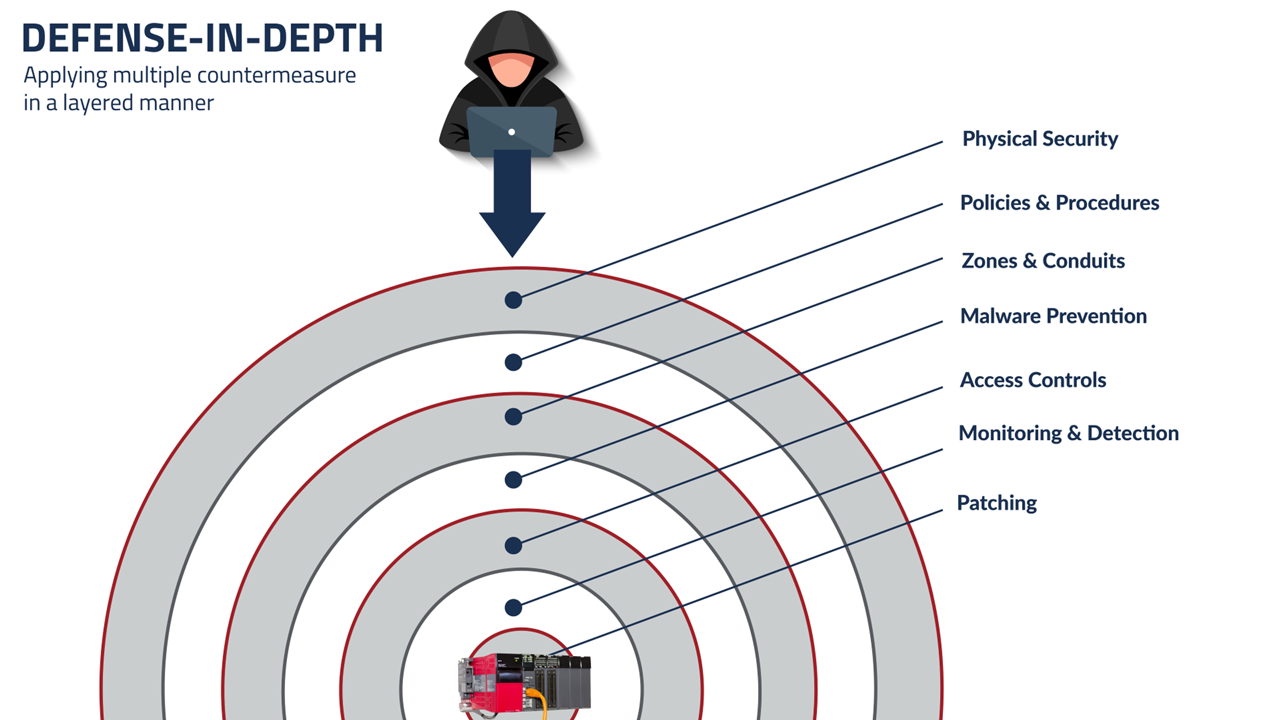
The ISA/IEC 62443 standards for OT cybersecurity, which reference the Purdue Model, are crucial for industrial organizations. A key principle of the standard series is the Defense-in-Depth strategy (see below), which layers security approaches on top of each other.

The FlexEdge® Intelligent Edge Automation Platform, powered by Crimson® is designed to connect organizations to their data. It makes first mile processing as simple and secure as possible.
Cyberattacks can come from multiple directions – malicious software, an on-site hacker with a personal laptop, or a sophisticated infiltration attempt by a nation state. Adopting a layered strategy is the best way to protect industrial applications against would-be attackers – starting with the deepest layer.
IT departments have been applying these cybersecurity principles for years at the enterprise level. However, IT often has a different view on legacy technology than OT. IT routinely swaps out laptops and PCs every three to five years. For IT, cybersecurity updates often come embedded within that new hardware.
As a result, IT specialists don’t always grasp the needs and challenges of their counterparts in OT, who have valid reasons for keeping reliable applications around for a long time. To align their needs and objectives with IT, they need surer footing to navigate today’s cybersecurity requirements and quality solutions to bring to the table. By developing a deeper understanding of these principles, OT operators and control engineers can align their systems with everything AI has to offer without putting their organizations at risk.
Barry Turner, Technical Business Development Manager, Red Lion Controls


