TechnologyJanuary 18, 2023
Basis for an end-to-end security strategy

Managing assets as part of device and update management. Due to the development of automated tools for identifying resources and threats, industrial asset management plays a vital role in many industries where security operations are required. Asset management is not just crucial for software and IT companies.
In the world of cybersecurity, the only things that can be protected are those that are known to exist. This is why managing industrial assets has proven to be important for protecting all kinds of companies from unauthorized access.
In this context, device and update management is an essential building block for a proactive, end-to-end security strategy. It provides security teams with an inventory of OT resources and the associated components.
Industrial asset management is a process that involves constantly checking the accessible components to ensure that they are up to date. This makes it possible to identify and immediately eliminate their potential security risks and vulnerabilities. The assets can come in different forms. Traditionally, assets are a control system or industrial PC. However, special IoT or automation devices and software-defined resources such as control apps or reloadable apps are also listed as assets.
In the OT area, any device, resource, or service can pose risks or possess vulnerabilities that could result in a breach of the particular resource and in turn, of the network as a whole, if hackers use the compromised resource as the gateway for a full-scale attack.
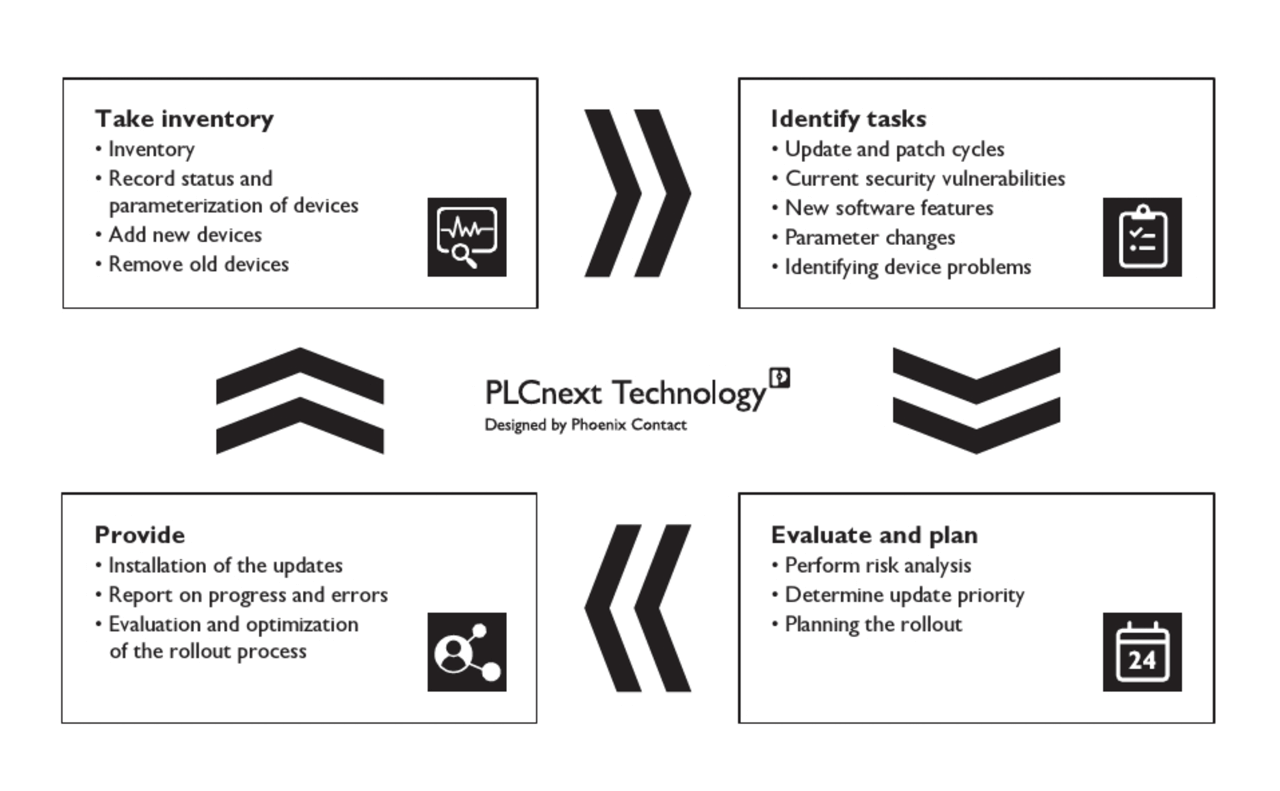
Diagram of the software update process.
The advantages at a glance
Managing industrial assets gives the entire company the visibility it needs to develop a long-range security strategy that can be used as a basis for keeping assets up to date and helping to defend against threats quickly and proactively. This type of approach offers several key advantages:
- Taking inventory: When a solid process for managing assets is in place, new OT services and resources can be identified and applied without compromising the security of the company.
- Interoperability: Companies use OT services and components from different manufacturers. It must be possible to manage these assets in the interests of cybersecurity, preferably through a central service. Device and update management using OPC UA ensures that it is possible to manage industrial assets regardless of the manufacturer.
- Consistent updates: Device and update management is capable of implementing both security-critical and functional updates for all directly accessible assets. This also applies to the underlying assets connected to the main assets.
- Easy and secure receipt of updates: Those responsible for assets or security teams must be informed about updates from the asset manufacturers in good time. For this purpose, device and update management can connect to the update repository provided by the manufacturer and search it for new versions of the deployed assets at regularly defined intervals. If an update is available, it can be obtained directly and without loss of integrity and used in device and update management.
- Flexible use: Device and update management can be deployed in a range of environments. Depending on the application, it can be used as an app on an industrial PC, software on a PC, or an IT container. Depending on the application, it can be used with the identical functionality.
In the ways described above, device and update management puts companies in a better position to detect and react to security risks. Although industrial asset management is only one component of an effective cybersecurity strategy, in most cases it is impossible to implement proactive security measures without central asset management.
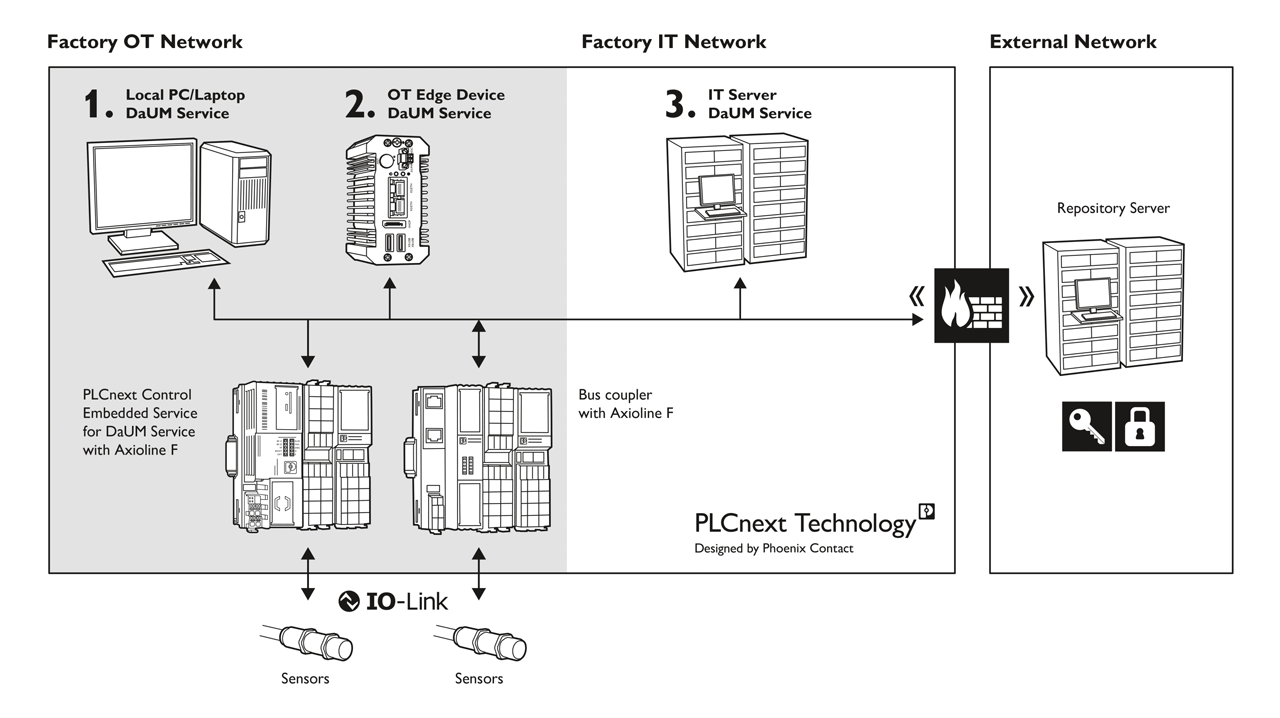
Overview of the components for device and update management.
Consequences of inadequate management or no management at all
Poorly implemented device and update management or the complete lack of industrial asset management complicates more than just security procedures. It also creates critical risks for the entire company, including a higher risk of business interruption.
If key data or systems are no longer available due to a security breach, the company might not be able to operate any longer. Such interruptions damage a company’s reputation and also lead to serious financial consequences. Inadequate device and update management also interferes with a continuous and accurate inventory of OT resources.
If operators do not know where each asset is located in their company, they can never really know the areas that pose the greatest risks. This lack of certainty makes it difficult to apply security resources efficiently when risks occur.
Similarly, ineffective industrial asset management erodes the ability of security teams to operate effectively. Security operations are difficult to automate if operators do not have an accurate list of existing resources and risks.
Instead, their security teams have to rely on locating and securing devices manually, which is an inefficient use of time and money.

Risks in the context of protection against unauthorized access.
Numerous continuous activities
Since there are many forms of OT resources and security risks, device and update management is a process that involves numerous activities. The industrial asset management approach varies from company to company, depending on the kinds of resources at risk. The pillars of the process for a typical company are presented below:
- Identifying devices: By identifying and assessing each critical point in the network for security vulnerability, teams can take immediate action to fix problems.
- Identifying tasks: Industrial asset management provides support for identifying tasks in order to close security gaps or roll out new features.
- Planning implementation: As updates can have different levels of urgency, device and update management offers the option of starting an update immediately or at a specific time.
- Installing updates: After the tasks have been scheduled and prioritized in the industrial asset management system, the update is installed on the assets. In this context, the security team can choose whether the update should be applied immediately after the transfer or later.
It is important to remember that many of the resources described above constantly change. Network devices can come and go. This is why industrial asset management processes must be executed on an ongoing basis to keep pace with rapidly evolving environments.

Using OPC UA technology in the process industries.
Updating Software with OPC UA
The software update model defined in the OPC UA 10000-100 specification is used to manage the software of an industrial asset. This can involve installing new software, updating existing software, updating firmware, and performing a limited backup and recovery of parameters and firmware as needed for the update.
The OPC UA standard can be used for the following applications, among others, regardless of which manufacturer is involved:
- Updating devices by using software update client software. To address domain-specific constraints, this may involve domain-specific client software. For example, this software stops a machine from updating in the production area while a redundant device needs to be activated in the process area.
- The software update can be applied to any device or software component that is exposed in the address space of the server.
- If multiple connected devices are to be updated in a machine or plant, they must first be switched to a specific mode in which they wait for the update to start and do not resume operation.
- Backup and restore for fast (re-)commissioning after a possible system failure or device replacement: The data that was backed up beforehand is transferred to the (new) device, and the original state is restored.
Conclusion
In the past, industrial asset management was not a high priority for companies. This is because there were no suitable tools for automating industrial asset management processes. Manual continuous inventory management was not practical. Today, due to the development of automated tools for identifying resources and threats, industrial asset management now plays a vital role in many industries where security operations are required.
Asset management is not just crucial for software and IT companies. It is also key to any company that relies on software and hardware to keep operations running. This is true for almost every company right now.