TechnologyJuly 10, 2018
Benefits of IIoT and Industry 4.0 for secure remote connectivity
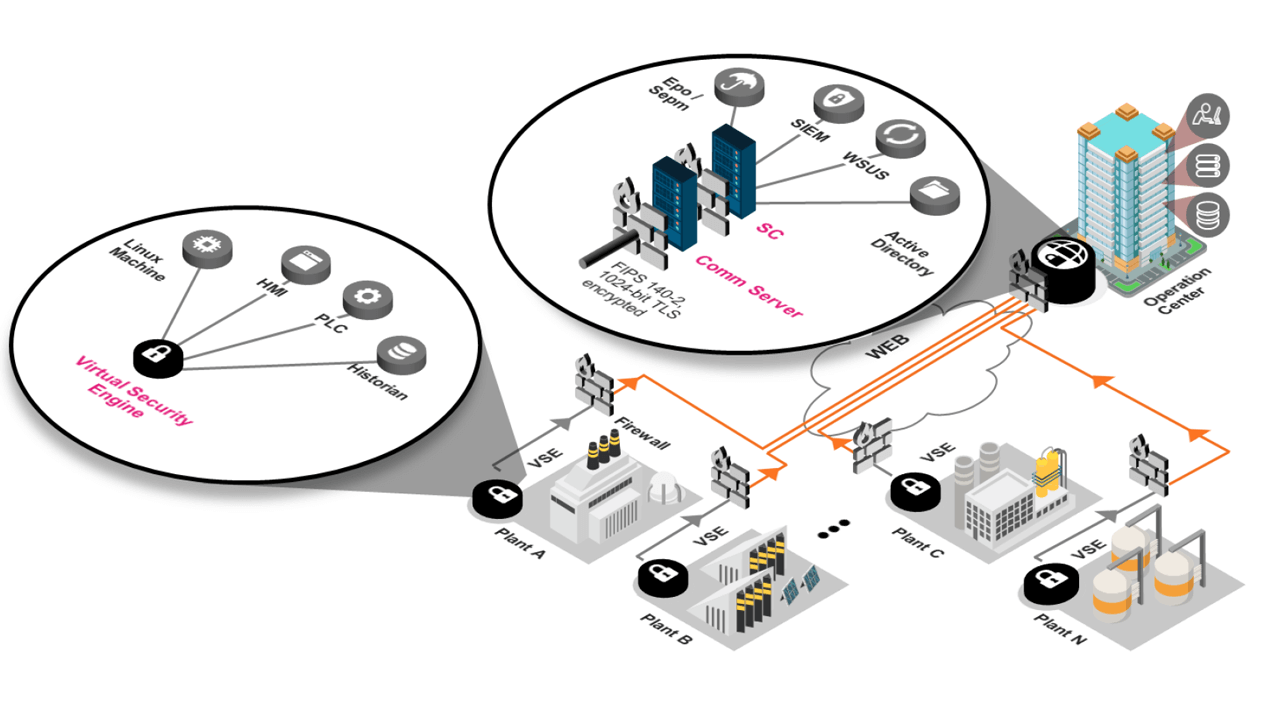
Combining IIoT and Industry 4.0 with cyber secure remote access represents the next wave of innovation and considerable operational advantages. A comprehensive secure remote access platform can minimize risks and costs while maximizing the rewards, such as increased efficiencies, and timely responses.
Companies today have opportunities unlike ever before. The emergence of the Industrial Internet of Things (IIoT) and Industry 4.0 provide data useful for a countless number of reasons leading to, improved efficiencies, maintenance, and innovation; resulting in cost reduction. With the ever growing connected nature of industrial plants and assets, there is an inherent risk of attack.
Many new attack vectors provide unforeseen ways into facilities and networks, with serious consequences. The best option to ensure compliance across plants is a top-down cyber security solution. This will ensure uniform security policies and provide the most secure solution for your business.
Securing remote access
Many industrial corporations are granting privileged remote access to vendors, operators, integrators or other third-party service providers. This often leaves gaps that introduce significant security risks. The frequent mismanagement of remote-access by industrial corporations is creating multiple backdoors into industrial plants and manufacturing facilities. While blocking this access is particularly tempting for CISOs, its removal, in most cases, would lead to an acute loss in productivity and a significant reduction in vendor agility and incident response times.
The current waves of industrial innovation, the industrial Internet of things (IIoT) and Industry 4.0, have boosted companies in ways that were never considered before, such as the advent of smart factories, the bolstering of business process visibility, and increases in productivity and overall operational efficiency. These waves have led to massive growth in the number of things connected to operational networks.
Industrial corporations face an ever-compounding challenge to manage and secure remote access to their operational technology (OT) and industrial control systems (ICSs). The requirements for compliance and proper governance demand that systems be protected from incidents that can impact operation, and cause additional operational costs.
OT remote access cannot simply be viewed as an extension of standard IT remote access. ICS assets, if compromised, pose extreme risk to operational safety, integrity and efficiency. With the potential for malicious as well as accidental incidents, it is crucial that corporate ICS network managers work in partnership with their vendors, integrators and Managed Security Service Providers (MSSPs) to maintain compliance and vigilance. Chief information security officers (CISOs) must have full control over the access details of every vendor and operator requesting access to their networks, whether the request is internal or external, for local or remote access.
In this article, we explore how industrial corporations can plug the numerous existing, vulnerable entry points into their networks. We examine how remote access has spiraled out of control, and the many challenges faced with this often costly and unnecessarily complex issue. We will attempt to define the components for the ultimate remote access solution, maximizing security while minimizing costs. This solution adopts a unique holistic approach, reducing the risk while maintaining the reward of secure remote access. We challenge the conviction that there is no complete method to securely and cost-effectively provide robust remote access to ICS and OT networks.
lloT & Industry 4.0
Many CISOs and CIOs struggle to balance the benefits of IIoT and Industry 4.0 with the inherent security risks involved. Plants will become smarter and increasingly connected. Vendor and integrator access will steadily become a “necessary evil” as operators will need access to the ICS assets they oversee.
As the number of connected assets and machinery increases, so does the need for a secure remote access platform that will enable efficient and secure management of these devices. When remote connectivity risks are properly managed, industrial companies can enjoy many extensive benefits.
Why risk at all?
Multiple types of remote users need to access ICS networks. Securing access to industrial networks is no trivial task. Understanding operator roles can have significant impact on how the remote access strategy evolves. In addition, the sheer number of remote connections must be managed in order to ensure only authorized activity is happening in the operational domain. In most control systems, the roles that require remote access to control assets may include, but are not limited to:
- Plant security engineer
- Security support and systems engineers
- Security specialists and maintenance engineers
- Equipment vendors
- System integrators or MSSPs
Complex industrial corporations often have many sites, each with hundreds to thousands of connected devices. Vendor operators could be required to connect and access these devices at any given moment. The number and purpose of remote access sessions continues to grow exponentially, given that every connected device needs to be compliant with security standards, requires support, maintenance (prevention, fixing, and troubleshooting of problems), and updates. Due to the prohibitive costs associated with onsite vendor and integrator visits, many of these actions are best performed remotely.
The security risk to ICS networks is ever-present; the greater the number of sites and ICS assets, the greater the need for a single, centralized security solution. Billions of smart devices are becoming connected: The number of connected smart devices is exploding, with 30-50 billion devices predicted by 2020.
Managing secure remote access
Notwithstanding the IIoT’s tremendous potential, organizations must overcome numerous, potentially disruptive issues, evolve operations and delight customers – all while increasing the bottom line. The transformation this implies is huge.
Maintain remote entity compliance
Today, many industrial companies rely on integrators or device vendors to maintain compliance with security governance and procedures for their own devices and assets, such as PLCs or HMIs. However, the industrial corporations have little insight or impact on the security compliance or standards of the vendors accessing their OT networks.
Visibility and security measures
Many industrial corporations do not know how many or even the nature of all devices connected across their sites and plant environment. Part of the security equation involves how operational assets are accessed and managed; including how the cyber security posture of a control system can be effected if the management of remote access is not understood by a business or is conducted poorly.
A fundamental principle of securing remote connectivity is to know your assets. With continuous growth in remote connectivity to the network, visibility needs to be comprehensive, up-to-date and automated. After all, unknown devices cannot be secured.
Balancing the risks and rewards
While lloT brings huge value potential, organizations must overcome a multitude of issues. The challenge is to avoid letting the volume of connected devices and associated security issues impede the race to enable IIoT. This is a crucial issue for an OT network manager. The partial solutions and workarounds used today are not the answer. What is needed is a single, centralized solution that diffuses risk and empowers businesses to forge ahead towards Industry 4.0.
Industry needs to restore order
Many industrial companies have inadvertently opened up their remote access network to back doors from a host of third parties, vendors, integrators and other service providers – the number of which seem to be multiplying at an uncontrollable rate. In many cases, network backdoors have been transformed into “revolving doors”, introducing serious risks. In addition, there are significant, multifaceted issues involved with enabling access by so many remote operators.
The challenge to manage and secure the exponential number of connected entities is creating confusion and disorder. Many CISOs and OT security teams have been simply overwhelmed by the complexity of trying to manage and attain operational efficiency while maximizing security. Outsourcing services does not relieve the CISO of their responsibility to ensure that appropriate controls are in place to protect valuable assets. When multiple vendors and platforms connect remotely to the OT network, the latter needs to contend with multifarious issues and risks. The below list presents several inadequacies in current solutions but is by no means exhaustive:
VPN access
VPY typically gives full network access, via a secure tunnel, to a vendor or integrator who has been authenticated. In some cases, there is no way to prevent the vendor from viewing any asset or device on the remote operational technology (OT) network. In addition, uncontrolled third-party devices can spread malware to an entire subnet or network that is made available through the tunnel.
Lack of role-based security
Once authenticated and authorized, an operator can execute privileged actions and it may be difficult to monitor or control what they actually do. The inherent security and business risks associated with giving third-part operators privileges that they do not require include harm done to data, as well as charges for work not performed whether these issues are malicious intent or unintentional.
Operator security standards
Vendor security standards are partially, or not known at all to the ICS operators. Standards may even be lax to the point that passwords are stored on sticky notes, systems may not be patched and antivirus definitions out of date.
Vendor sites not necessarily secure
When a vendor has an interior platform, multiple inbound and outbound ports may have to be opened on the firewall. End users should be aware that the vendor could be exposed to untrusted and hostile environments. A compromised vendor network could enable an attack to piggyback on a trusted connection into the control system.
Automated inventory compliance Often, the CTO or CISO have little or no visibility into the growing number of field assets. An OT network is especially vulnerable in this situation. Without control over remote access, third-party operators have the ability to maliciously or accidentally cause harm.
Noncompliance of vendor’s solution
When the vendor remote access solution does not comply with the vendor’s security policy, there is serious risk of a backdoor opening into the industrial site. When there are multiple vendors, this risk may increase exponentially.
Accountability over vendors
The lack of an up-to-date access event log data is an inherent hurdle in securing remote access to industrial corporations and OT networks. It is often difficult to track who and when someone logs onto a system; security controls may be insufficient to control or limit who can connect to a specific device. Stakeholders can have practically no visibility of who is currently connected to their networks and connected assets.
Multiple entry points out of control
Both the deliberate creation of remote access “workarounds” and unintentional manifestations of access pathways by a remote access solution is a critical concern for all those tasked with securing industrial companies. The “necessary evil” for remote access does not necessarily have to result in unmanaged risk.
Comprehensive secure access
Industrial operators are struggling to protect their highly complex multisite and multivendor SCADA networks, despite the great potential of IIoT to propel companies with increased efficiency, decreased onsite maintenance and associated cost savings. The growing surge in connected devices is serving to increase the already dire need to securely manage and maintain control of multiple remote connections.
Managing remote access security in this era of industrial hyper-connectivity creates a challenge to mitigate the risks by providing a secure cost-effective solution, based on known challenges and the increasing risks associated with rapidly evolving needs of industrial corporations. Consider the following advantages that many companies have incorporated into their cyber security operational frameworks.
#1 Deploy a single, centralized, secure remote access solution
A siloed, plant-by-plant approach to security compliance, discovery and protection can be extremely costly and often leads to a lack of critical information. Deploying one single, centralized platform to locate and secure all field devices and remote access points enables management across all connected vendors and devices in order to ensure compliance.
Key requirements
- AAA role-based security to enable privileged access
- Real-time supervision, session termination and recording
- Automated inventory and asset discovery
- Cost reduction and increased efficiency for multiple vendor access
- Password vault to securely store privileged credentials and prevent operator account credential sharing
#2 Flexible authentication, authorization and secure schema
Access permissions should be managed incorporating the principle of least privilege and separation of duties to limit risk. Access to assets and associated facilities is limited to authorized users, processes, or devices, and to authorized activities and transactions. Network integrity is protected, incorporating network segregation where appropriate.
Key requirements:
- Role-based security for vendors/operators
- Granular activity permissions limited to certain assets and tasks
- Centralized authentication – Active Directory Integration (SSO)
- Firewall friendly – single port, single direction access (TCP: 443-outbound)
- TLS 1.2 encryption of all communications
- “Hyper tunnel” – vendor and protocol agnostic communications
- Controlled environment for secure file transfer, patches and updates
#3 Transparent Auditing and Accounting
Plant-wide approved security policies are distributed and deployed per site, delivering continuous visibility across all locations, along with alerts on security vulnerabilities and compliance issues. Access privileges are defined per each asset, and remote access sessions may be aborted. A full audit trail enables plant administrators to view past events.
Key requirements:
- Real-time session supervision
- Remote session termination
- Recording & logging of session activity
- Remote access sessions using VNC or RDP
- Complete audit trails and forensics
#4 Complete Visibility and Automated Inventory
A fully automated process provides full visibility of network assets, ensuring security procedures and plant-wide policies are adhered to. Inventory may be checked to verify that compliance work was carried out, and additional security essentials such as: patching, log collection, remote access, and compliance reporting are also managed.
ey requirements:
- Automatic discovery down to L2 and L3
- Configuration collection
- Change monitoring & management
- Classification & labeling
- Visualization
- Assets labelling
- Detailed reporting
Case Study – Oil & Gas Company
 A case study illustrates the deployment of a centralized, secure remote-access solution. OGC is a large oil and gas company, with 47 sites on four continents and over 80 vendors connecting to plants on a daily basis. The company was aware of the high operational costs and the lack of control over what the many vendors were and were not doing as they performed their tasks. OGC was looking for a solution to address three main areas:
A case study illustrates the deployment of a centralized, secure remote-access solution. OGC is a large oil and gas company, with 47 sites on four continents and over 80 vendors connecting to plants on a daily basis. The company was aware of the high operational costs and the lack of control over what the many vendors were and were not doing as they performed their tasks. OGC was looking for a solution to address three main areas:
- Vendor Accountability: improving control over vendors connecting, including auditing, verify all work performed, and supervising it
- Secure Remote Access: controlling access to all of the company’s sites, including password control, centralized authentication, and asset visibility
- Cost Reduction: as a derived benefit from the deployed solution
The Solution
OGC deployed a remote access security solution that included the following components.
For vendor accountability:
- Full audit
- Real-time supervision and session termination
- Remote access granted by plant personnel
- Remote access sessions conducted with Virtual Network Computing (VNC) or Remote Desktop Protocol (RDP)
For security:
- Centralized authentication via Active Directory Integration
- Plant security dashboard
- Deployed policies per plant
- Designation of access privileges per asset
- Management control of remote access
- Continuous monitoring of field assets
Results
A few weeks after deploying the solution, OGC noted a cost reduction resulting from the decrease in resources required to follow up the vendors’ work and managing the site connections. Vendors completed their work faster and thus had time for carrying out additional tasks. The site manager reported that they had a much fuller picture regarding what was being done at their sites and that the new solution handled unified plant security compliance, as well.
Conclusion
IIoT and Industry 4.0 represent the next wave of innovation bringing considerable operational advantages. The exponential growth in connected devices and smart machines demands a corresponding increase in secure remote access to support and maintain compliance. A comprehensive secure remote access platform can minimize risks and costs associated with lloT, while maximizing the rewards, such as increased efficiencies, and timely responses. It will enable strategic companies to discover, detect, and address all possible threats, and forge ahead with industry 4.0.

