TechnologyMay 27, 2019
Cyber security for oil and gas industry applications

Cyber-attacks have increased over time and require a more comprehensive, proactive approach for industry to protect critical systems. Protecting control systems will be an ongoing responsibility that everyone must share by following standards and implementing a defense-in-depth approach to cybersecurity.
The oil and gas supply chain is a globally interconnected environment, moving millions of barrels of crude oil and billions of cubic feet of natural gas on a daily basis. Due to the increasing demand in global energy, the oil and gas industry faces many disputes and challenges in the service sectors of exploration and production (upstream); processing, storage and transport (midstream); refining and processing (downstream); and oilfield applications. One of these challenges is the growing risk of cyber threats.
Today’s industrial Ethernet and wireless technologies have made it easy for oil and gas professionals to share data faster and more efficiently – whether they are on an offshore platform or back in the main office. All of these far-flung locations, spread throughout the globe, are connected via complex, enterprise-wide networks transferring critical data between all areas of production and processing and to the corporate headquarters for planning and scheduling purposes. Connecting control systems with the business world optimizes operations.
However, these complex communication networks distribute data in all directions and to multiple applications, increasing the risk of cyber threats. An accidental virus infection could shut down production, costing millions of dollars in lost revenue. The global supply chain infrastructure is susceptible to numerous risks and threats; any intentional or accidental disruption anywhere along the communication path could result in a catastrophe.
This susceptibility of the communication path begins at the wellhead and ends at the distribution point at the other end of the supply chain. Hackers have a long path on which to find a small back door that allows them entry to inflict potential damage. This is not a simple violation of the companies’ privacy or security.
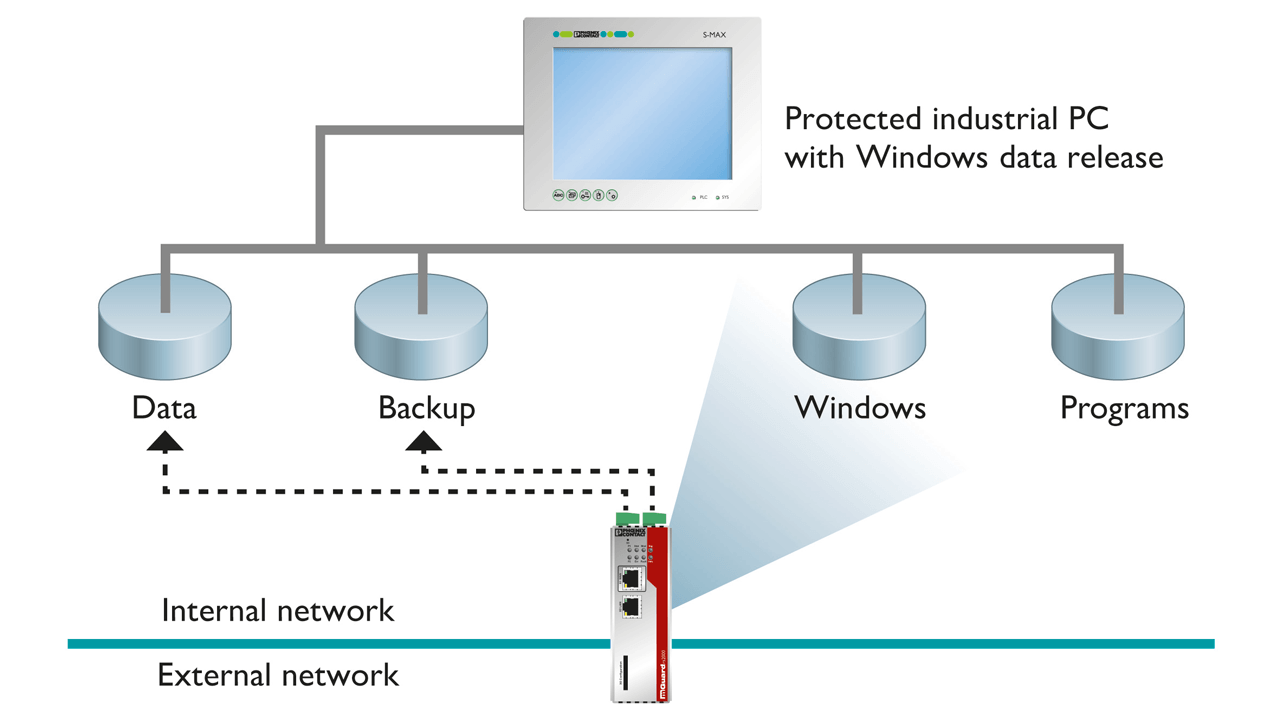
CIFS Integrity Monitoring is an alternative to traditional anti-virus methods.
Cybersecurity guidelines
According to a news release from Tripwire, Inc., 82 percent of oil and gas industry respondents said their organizations have seen an increase in successful cyberattacks over the past 12 months. The study, conducted by Dimensional Research in November 2015, included more than 150 IT professionals in the energy, utilities, and oil and gas industries.
The study also found that 69 percent of oil and gas respondents said they were “not confident” their organizations were able to detect all cyberattacks. Unfortunately, there are numerous examples of cyber risks and threats to the oil and gas industry.
One of the biggest threats appeared in 2012, when the Shamoon virus attacked Saudi Aramco, the world’s leading oil and gas production company. The virus erased data in at least 30,000 of Aramco’s corporate computers. Aramco reported that the objective of the attack was to stop the company’s production, which represents more than 10 percent of world oil supply.
Shamoon is just one example of a threat to strike the industrial world. Other well-known malware includes Stuxnet, Flame and Duqu, but others are likely lurking undetected. A hydrocarbon system could come under cyber-attack for multiple reasons:
- Financial gain: insider information
- Intellectual property theft
- Supply disruption from environmental activists
- Supply disruption from political activists
- Disgruntled employee
- Gaining unlawful access to technology related to production and processing
- Terroristic threat
- Cyber warfare by a rogue nation
The owner-operators must address all of the above points as they begin designing and maintaining a “cyber-secure” control and communications network infrastructure throughout the entire supply chain, from the wellhead to the final distribution point. How will an owner-operator develop, implement and maintain a corporate-wide, global-yet-local cybersecurity strategy of this magnitude? In the new cyber world order, everyone should be involved in the design and engineering of cybersecurity guidelines for existing systems.
This represents a huge challenge for owners and operators. They now need to locate and map out the entire supply chain network and determine what technologies, best practices and programs are suited for the specific system without any production interruptions. Meanwhile, they must meet the cybersecurity guidelines that government agencies have imposed for the specific industry.
Protecting critical process data
Hydrocarbon production, processing and distribution systems have evolved and developed based on a safety culture. Most owner-operators have already implemented a common health, safety and environmental (HSE) culture to ensure that their facilities meet the industry’s needs.
The next step is integrating measures and procedures into this existing system from day one. Protecting the entire digital network infrastructure must become a part of the norm. It is important for the global oil and gas industry to protect its valuable assets. This means that there is an informal security interest for the protection of the flow of oil and gas, which benefits both producing and consuming nations. Supply chains all over the world are regulated by the country of origin. In the United States, the supply chain network is part of the critical infrastructure and is regulated by the Department of Homeland Security and its Chemical Facility Anti-Terrorism Standards (CFATS).
Hydrocarbon companies acknowledge that hackers and malware will get into systems. Knowing this, these organizations must take a proactive approach, focusing on the protection of critical process data. Owners and operators need to point out the location of critical data, identify the characteristics of systems that carry the data, understand vulnerabilities in systems and detect changes in activities that signal potential cyber-attacks.
Cooperation of engineers & IT
Network security is the highest priority of IT staff, but it is low on the radar for most control engineers or plant managers. The discovery of the Stuxnet worm, however, forced industrial plant managers to bring a higher level of attention to the operational risks that chemical, oil and gas, and other critical plants face. Since then, control engineers have realized that they need to take an active role in security, and not leave it entirely in the hands of IT.
To create a secure network, control engineers and plant managers must work together with the IT department and the technology they use. They face the difficult task of placing protective measures around and within existing systems and still maintaining the flexibility of multiple protocols and technologies. A good first step is to completely know and draw your existing network plant and if needed, place it behind the current IT infrastructure.
Recommended best practices include:
- Insulate and isolate communication between the corporate and the plant networks with a router
- Filter data coming in and out with a firewall; this also promotes network segmentation
- Avoid accidental or unauthorized access by blocking and managing access controls
- Mitigate viruses and malware that come into your systems with integrity monitoring scans and detection tools
- Use virtual private network (VPN) technology to send and receive encrypted data from remote locations.
Security in rugged conditions
In the industrial world, productivity drives business. When the Internet started growing, control systems evolved from isolated islands to highly interconnected systems. The concept of “security by obscurity” as a tool to protect control systems from cyber-attacks is not realistic. However, network architectures can be protected and guarded by specific devices coded with the same IT secure technology, but designed to meet the rugged, hazardous conditions that may be present in a hydrocarbon plant.
Today, there are security devices with industrialized hardware and advanced configuration options can provide a defense-in-depth option for critical applications. These devices have sophisticated security capabilities including firewalls with integrated router and VPN. The Common Internet File System (CIFS) is the standard way that computer users share files across corporate intranets and the Internet.
Some industrial security devices include CIFS Integrity Monitoring, an antimalware tool used in industrial PCs to scan Windows-based systems for files that have been manipulated by malware, without the need of updating the database of signatures. Industrial devices can also save and store logs from data packets and information coming in and out of the network for audits with the corresponding federal regulatory agency.
Remote secure, cloud-based portals
A defense-in-depth approach to cybersecurity incorporates multiple layers of protection to keep unwanted traffic off the industrial network. It is proven that diverse layers of protection within industrial networks are a better approach than a single, monolithic one. This defense-in-depth method of protection delays, more than prevents, access from unwanted users. These measures not only connect and protect, but can also be easily integrated into production environments and industrial systems.
No matter what security measures the owner of the hydrocarbon plant takes, there is always a possibility of a breach, so a disaster recovery plan is still critical. This plan should be tested and practiced. Defensive strategies must be monitored and active at all levels of possible attacks: detection, isolation, containment and elimination.
Taking this protection one step further, there are now secure, cloud-based portals that can integrate industrial devices and automated systems directly into the network without modification or planning. A professionally hosted service can give oil and gas system operators easy access to fast and secure remote support, offering complete encryption of data and stateful firewall protection for every site.
Conclusion
Oil and gas companies understand that cyber-attacks have increased over time and that they need to take a more comprehensive and proactive approach to protect their critical systems.
In the constantly changing cyber world, protecting control systems will be an ongoing responsibility that everyone, from the owner-operator to the control engineer to the IT staff, must share. By following federal and industry standards and implementing a defense-in-depth approach to cybersecurity, hydrocarbon professionals will be better prepared to prevent the financial, informational and physical risks that can result from a cyber-attack.


