TechnologyJuly 10, 2018
Designing industrial networks from a security point of view
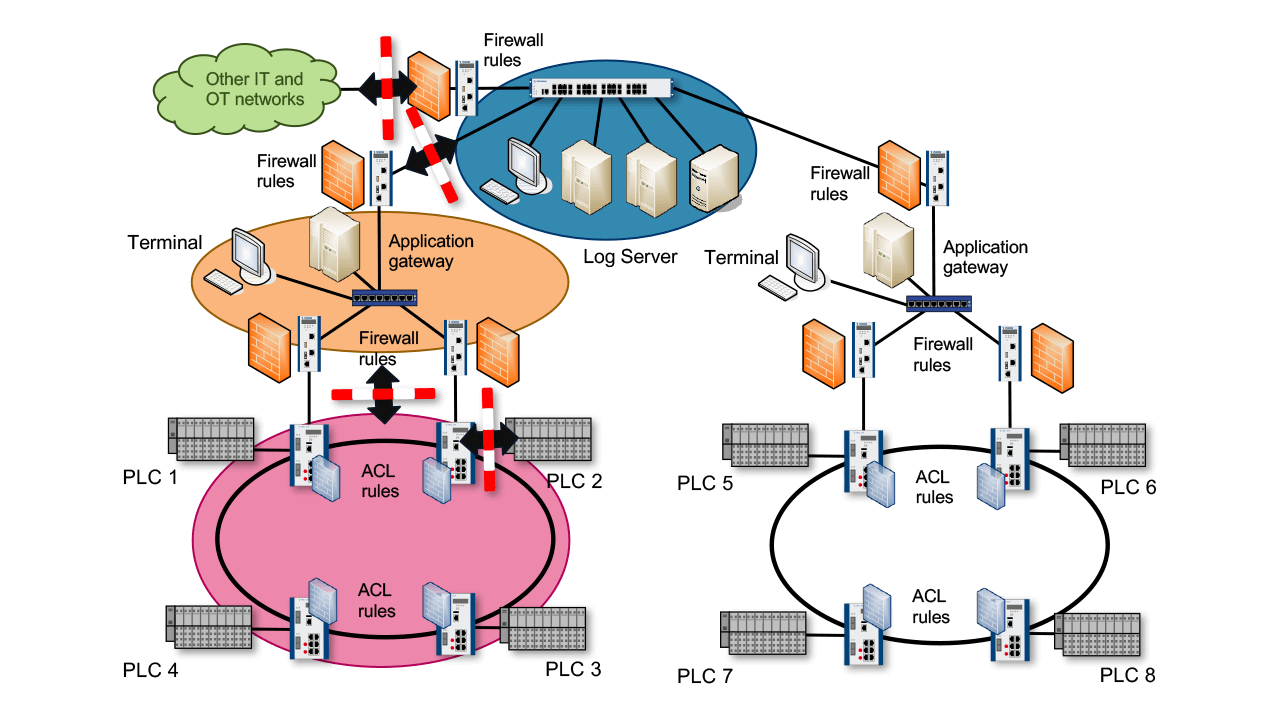
Addressing security during the initial phase of network design is an important step towards creating more secure industrial control systems. Discarding outdated architectures in favor of granular network zones limits an attacker’s freedom of movement within a network and protects critical or vulnerable devices.
INTERCONNECTIVITY HAS DONE WONDERS for the modern industrial facility. The ability to receive real-time data on every piece of machinery and physical asset within the operation has allowed utilities and industrial facilities to ensure higher levels of proficiency and better prepare for maintenance and replacement needs.
Yet, there is also a downside. Interconnectivity has eliminated any form of physical separation between industrial and other networks. Gone are the days when these borders could be relied upon to provide an added layer of security. Today, every component and sensor in a facility is a target for a would-be hacker motivated to penetrate the facility’s defenses.
What was once a blurred line has been completely erased as industrial component manufacturers have already started designing their connectable components based on standard industrial PC systems. This has created a harsh new reality for those charged with maintaining industrial networks. They are now a target and at risk to the same threats as any other network.
Perhaps most concerning, industrial networks tend to keep existing monitoring and control systems in place for years, sometimes going decades without security updates. Reasons can range from the unavailability of patches or a reluctance to change the software.
These variations in software are not without risks and may invalidate existing certifications. The outdated nature of such systems represents a significant challenge as more than 70 percent of all cyber-attacks target known and patchable vulnerabilities, according to the annual Verizon Data Breach Investigations Report (DBIR).
This scenario has created a series of vulnerabilities that must be accounted for. As today’s threats are more sophisticated and hackers are better funded than ever before, industrial networks must be equally adept in protecting soft targets and minimizing the potential for damage in the event of an attack.
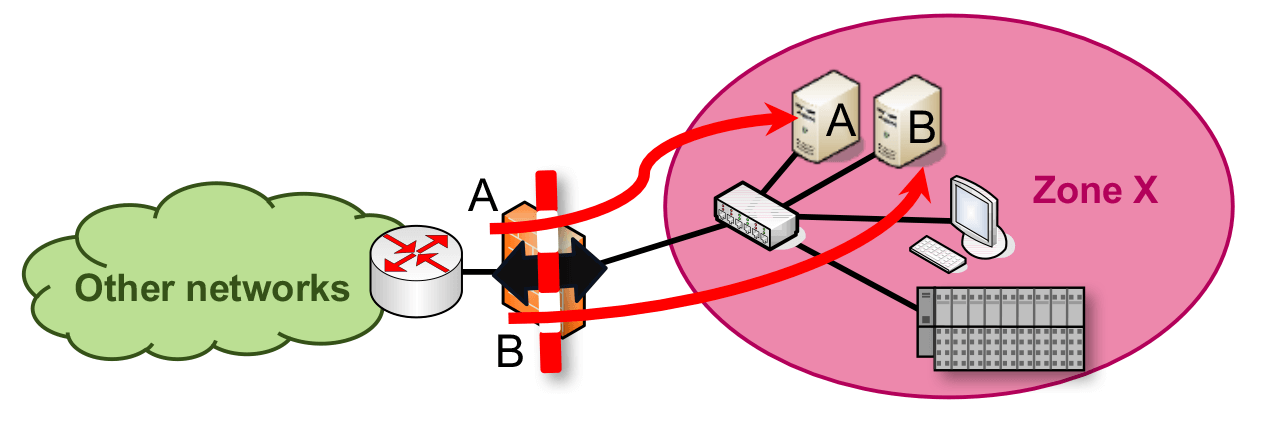
Firewalls and ACLs block unauthorized traffic by filtering traffic based on connection metadata (MAC addresses, IP addresses, port numbers and protocol flags).
Where to start
As with most networking considerations, the most effective place to begin is in the planning stages. Building your network structure from a security point of view will prove to be the most successful approach to thwarting attacks.
Most companies set up perimeter firewalls at the edge of their industrial networks to protect the soft targets in their industrial applications against threats from the internet or from office networks.
Although this is a necessary step and a simple first line of defense to guard against passive attacks on the network, it is also antiquated and considered to be an insufficient measure. Modern network security demands far more than just perimeter security. It requires vigilance at every level of the network.
Comprehensive network security concepts need to account for both different methods of attack and different types of attackers. Attackers tend to fall into two distinct categories: criminal agents and nation state hackers. Each group has very different motivations, so accounting for both is critical in establishing a proper level of network security.
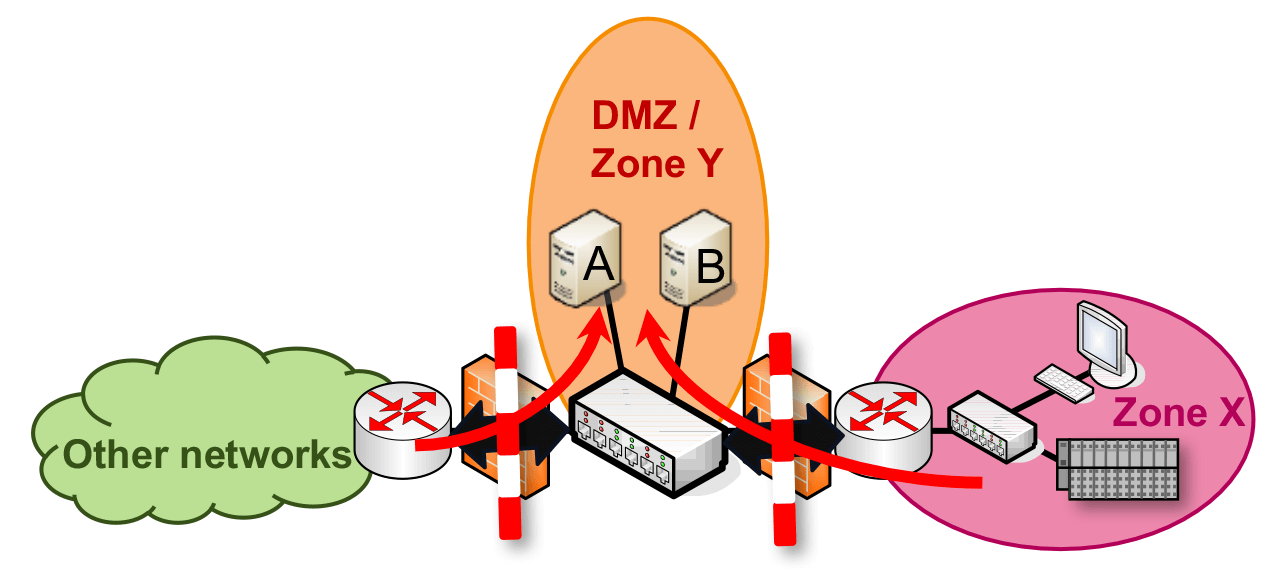
To enable a firewall to be configured in the most restrictive way possible, care must be taken to ensure that the network is divided into sensible zones.
Isolating the threat
There are a couple of constants when it comes to network security. One, you will always be subjected to constant attacks if you are connected to any form of network. Two, no matter how modern your security and defenses are, attacks will get through at some point and time.
Hackers are far too well funded and sophisticated to be completely shut out. When it comes to security, the facility must be correct 100 percent of the time, whereas the hacker only has to be right once. The odds are clearly in their favor. What is critical is how your network is positioned to respond once an attack takes place. Can you quickly identify, isolate and mitigate the threat before it causes damage? That is the key to securing the modern network.
Scenarios where the first line of defense has been compromised, i.e., the firewall at the edge between the production network and the office network or internet, are when attacks can begin to cause significant damage. Once an attacker has penetrated a network, they can quickly gain access to critical areas of the network if the architecture and configuration of the network were created with little or no regard for security. The good news: Implementing a network capable of withstanding an attack is possible if security is considered as early in the network planning stage as possible.
When designing networks, the network infrastructure may be based on a range of architecture patterns. The choice of pattern has a strong bearing on the security of the network and makes all the difference between an easily attackable network and a resilient network.
Given that architecture and topology are the basic pillars of a secure network, industrial security standards – such as the ISO/IEC 62443 family of standards – have been laid down for network design to show plant operators and system integrators how to create more effective network structures.
One of the most important network design guidelines is the principle of “zones and conduits.” Under this principle, an industrial network is segmented into different functional zones and the connections between these zones (i.e., the conduits).
Technical measures need to be put in place to control the zone transition. In most cases, firewalls and access control lists (ACLs) will be the most appropriate method. This network design with sufficiently restrictive zone transitions makes it more difficult to spread from a compromised zone throughout the rest of the network.
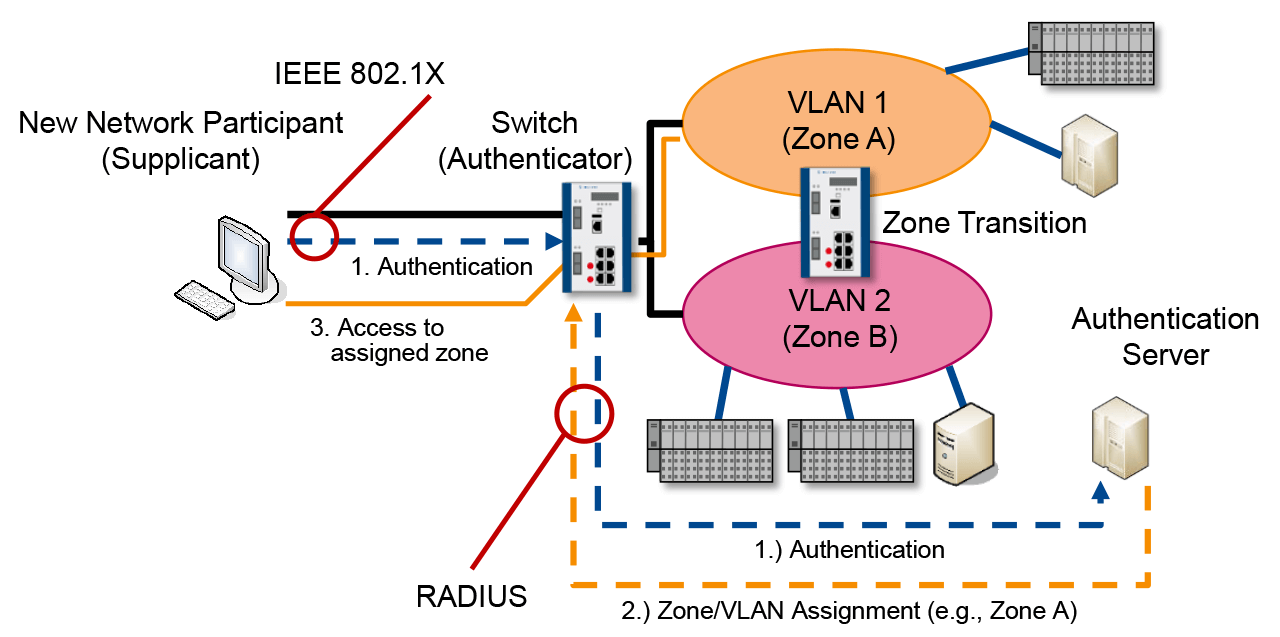
To restrict zone access to authorized devices, protections can be put in place in the form of protocols – for instance, an authentication via 802.1X or physical mechanisms.
In the security zone
A network can be segmented into zones by configuring packet filtering rules at various layers of the ISO/OSI layer model on switches, through firewalls or through application level gateways (ALGs). Firewalls and ACLs block unauthorized traffic by filtering traffic based on connection metadata (i.e., MAC addresses, IP addresses, port numbers and protocol flags).
According to the whitelisting principle, where only known data traffic is allowed through while all other traffic is blocked, a firewall’s rule sets only contain the properties of known and desired traffic. It is therefore not possible to communicate in an uncontrolled way with other devices outside the zone via the zone perimeter (the conduits).
Whitelisting limits the extent to which attackers can have an influence beyond a zone perimeter in the network because they make it difficult or even impossible for them to communicate with potential targets via the conduits.
To enable a firewall to be configured in the most restrictive way possible, care must be taken when designing the network infrastructure to ensure that the network is divided into sensible zones. The zones should be as small as possible, but at the same time, as little communication as possible should take place over zone perimeters. There are various design patterns and anti-patterns in the IT world that are better or worse suited for dividing up a network. These patterns can either strengthen or weaken system security.
Getting physical
Not to be overlooked or underestimated is the physical protection of network equipment. This should always form the basis of any kind of network security.
The effectiveness of a security concept with zones and conduits is largely dependent upon restricting access to the zones. Even the most restrictive firewall at the perimeter of a critical network component will be useless if an attacker is able to connect directly to a sensitive zone by just plugging a device into a switch.
To restrict zone access to authorized devices, protections can be put in place in the form of protocols – for instance, an authentication via 802.1X or physical mechanisms. Network devices, such as switches, firewalls, wireless local area network (WLAN) access points, etc., should be stored in locked cabinets so that unauthorized parties are unable to insert, remove or reconnect cables to gain access to the network or prevent other devices from accessing the network.
Physical protection is also necessary to ensure a basic degree of protection for the availability of network communications in general. If an attacker succeeds in cutting power to a device, resetting its configuration or having an otherwise negative impact on the device, the network can be severely disrupted. It may sound mundane, but physically separating the attacker from all devices protects a network against many kinds of attackers and methods of attack.
Conclusions and common sense
Security is a 24/7/365 day-a-year proposition. Hackers always seem to be one step ahead in their ability to find a fatal flaw or vulnerability in which they can exploit for personal or financial gain. While there is no way to prevent attacks or to fully stop them from penetrating your defenses, an adherence to security management best practices can go a long way in ensuring that damage is kept to a minimum.
Taking security into account during the initial phase of network design is the most important step towards creating a more secure industrial control system. Issues, such as exposed services, must also be incorporated as a matter of principle, e.g., by enforcing best practices, like the implementation of firewalls and the zones and conduits concept.
Discarding outdated “flat network” architecture designs in favor of segmenting granular network zones limits an attacker’s freedom of movement within a network and better protects critical or vulnerable devices against compromised services. When configured properly, your network security measures should act as a serious barrier to any form of attack on an industrial environment.

