TechnologyJanuary 28, 2019
Encryption technology provides solutions for Ethernet security
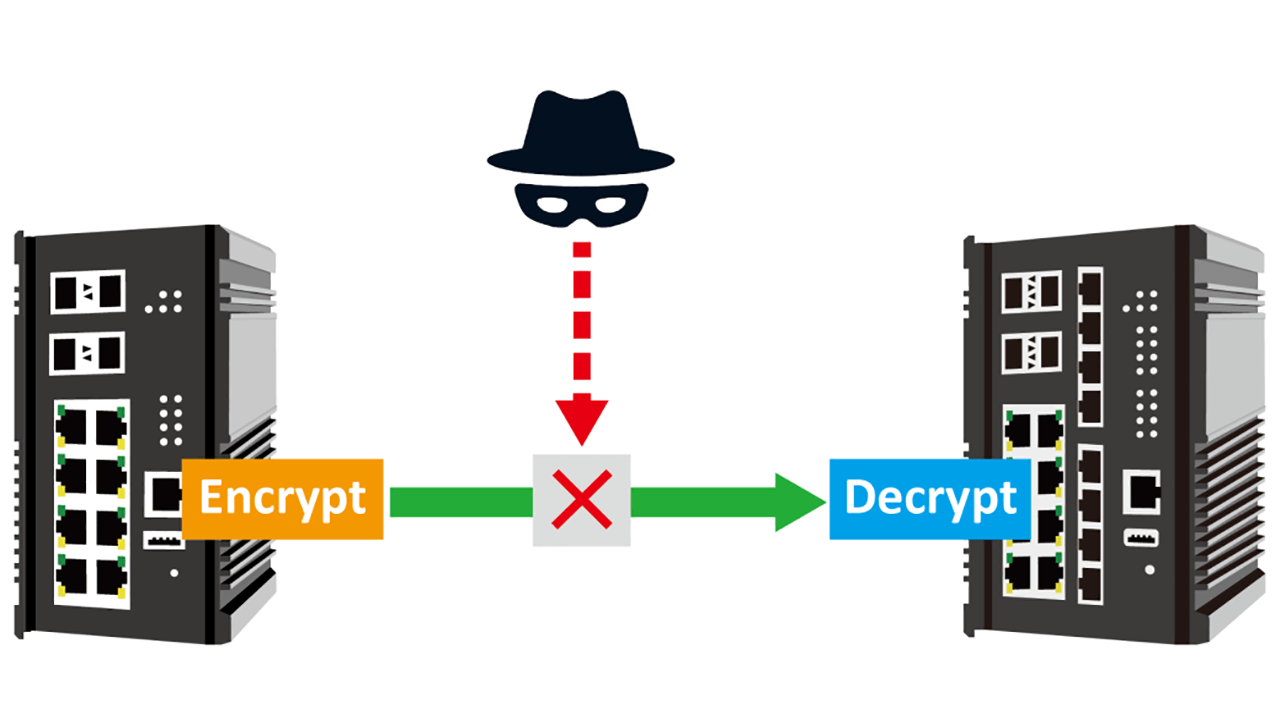
Cyber security is a considerable issue in the Industrial Networking that is demanding more and more attention. The IEEE 802.1AE standard, MACSec, is an efficient and high cost-performance ratio solution for Ethernet links to prevent “Man in the Middle” attacks and external threats from frame tampering.
The security of communication is becoming more and more important because of the projected growth in the number of IIoT devices. There are also risks for Local Area Networks (LAN) as someone may capture frames and tamper with them (typically called “man-in-the-middle” attacks).
Companies have used tunnel or physical layer encryption to protect data from attack, in the past. But for end-to-end tunnels like IPSec, more resources are needed for encryption and decryption. Effective key management and large numbers of keys can cause heavy loading for the server when using end-to-end tunnels. For physical layer encryption, the encryption method implemented by vendors and devices from different vendors may be unable to communicate with each other.
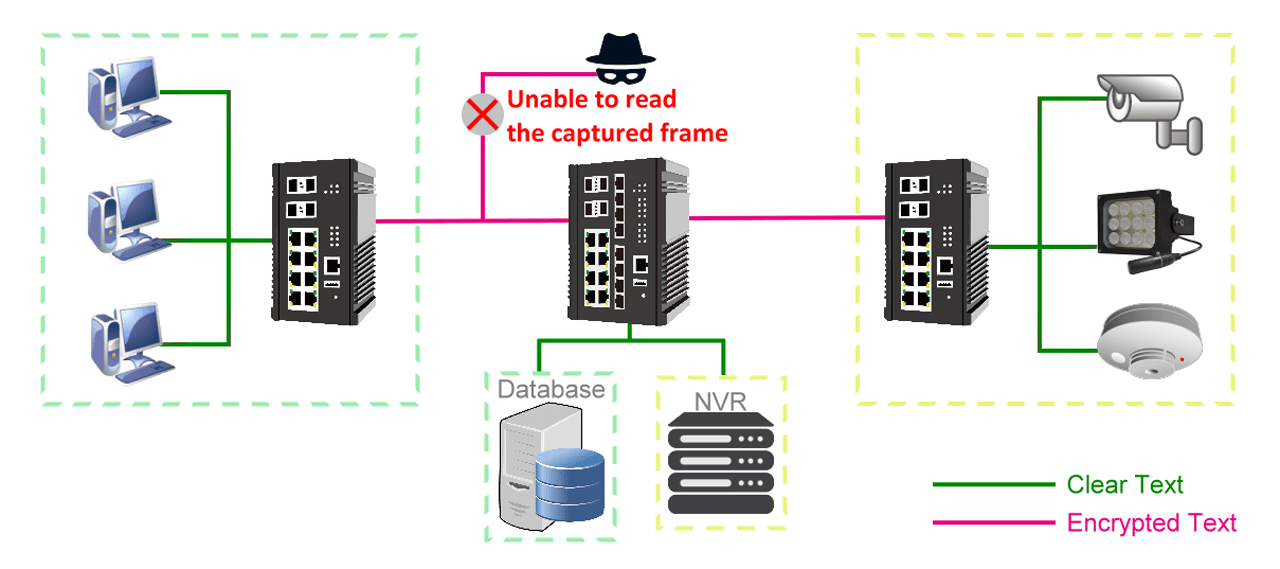
Users usually establish a VPN tunnel to protect data. But the resources and maintenance costs required for a VPN tunnel is much higher and systems are harder to setup.
MACSec L2 encryption
The MAC Security (MACSec) is an IEEE standard defined as 802.1AE where all devices that follow the standard can communicate with each other. MACSec is a MAC layer (layer 2) encryption and decryption method to provide secure communication on an Ethernet link.
MACSec works by adding a security tag into the standard Ethernet frame and then encrypting the content by keeping the source and destination MAC addresses. Any device that doesn’t support MACSec will see this frame as an Ethernet frame, and forward it to the destination.
In standard 802.1AE, the position of the secure tag is designated and fixed. MACSec products from Konten Networks can detect the location of 802.1Q tag and the position of the 802.1AE header can be configurable.
The encryption will be done before the frames are sent out and the decryption will be done after the frames are received on the MACSec enabled ports. Otherwise, the 802.1AE header will be added on the left of the 802.1Q VLAN tag. We can prevent the frames from man-in-the-middle attack due to the frames are encrypted during the transmission. MACSec uses AES-128 cipher suite for the encryption and decryption in the IEEE 802.1AE standard and also defines a higher secure algorithm–AES-256 in IEEE 802.1AEbn. Default support for AES-256 encryption provides protection.
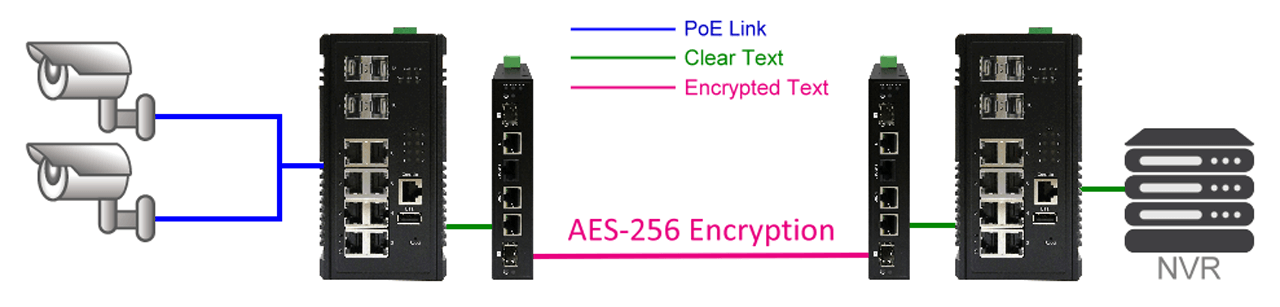
System designers can install one new encryption device, and frames can be encrypted before transmission and decrypted (incoming) without replacing network devices.
Benefits of MACSec
Because MAC Security is an IEEE standard, users can use the devices with MACSec from different vendors to extend current application. A network device hat supports MACSec provides a more secure communication for the Ethernet link.
The AES-256 encryption makes frames unable to be tampered with, even the frames are captured. Encryption and decryption are served by hardware. Therefore, the efficiency of crypto is much higher than if it was served by software. Its hop-to-hop architecture reduces the loading and CPU calculations required, so the system can work with the same performance as usual.
The format of MACSec frames is the same as standard Ethernet, so even network devices without MACSec receives a MACSec frame, and can forward the frame to the destination MAC address.
MACSec devices from Konten Networks also provide five useful counters for statistics and analysis. The number of non-security-tag packets (InPktsNoTag) and the number of bad-security-tag packets (InPktsBadTag) are helpful for checking malicious packets and monitoring the health of the network.
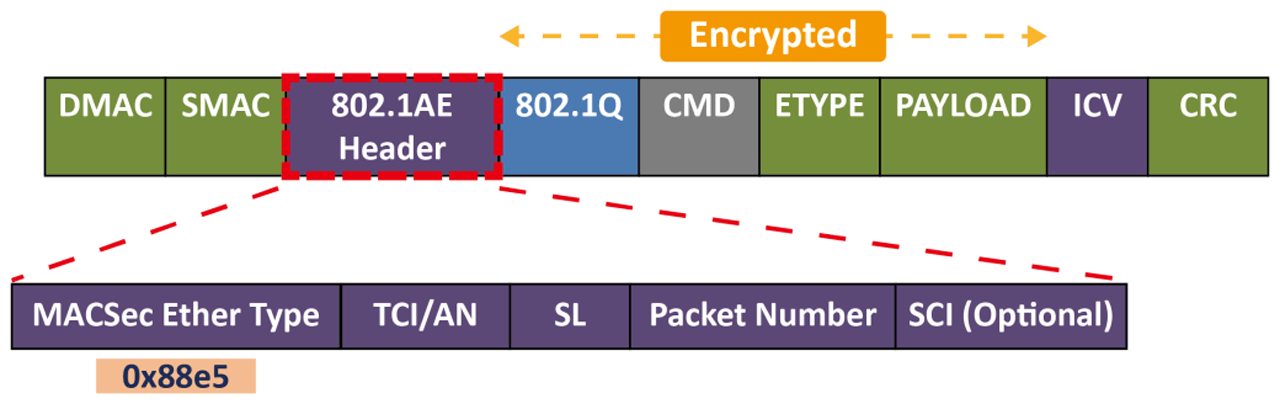
MACSec is a MAC layer (layer 2) encryption and decryption method for secure communication on an Ethernet link.
MACSec applications
It’s dangerous to transmit sensitive data in clear text without any protection; the data may be captured or sniffed by the attacker during transmittal. The attacker can tamper with the content of the frame and then send it back to the link. The user and also be misled when they receive a fake frame and make a wrong decision. Users usually establish a VPN tunnel to protect the data. However, the resources and maintenance costs of VPN is much higher and the administrator needs to have more technical background to setup the environment.
MACSec is a replacement for hop-to-hop encryption and decryption. Users only have to do some simple configurations and the key number of MACSec channels is much less than the key number of a VPN tunnel.
The encrypted data is hard to crack, so the attacker is unable to read and tamper with the frame even they can capture or sniff the link.
For existing applications, system designers can install just one new encryptor network device, and the frames can be encrypted before transmitting out. Incoming frames can be decrypted, without replacing any network devices.
Conclusion
Because of supporting hardware, encryption and decryption are efficient and save CPU resources for other communication protocols and tasks. The design of a standard Ethernet frame format using security tags becomes an effective extension for network devices without MACSec to both protect and provide higher levels of Ethernet security.

