TechnologyMay 27, 2019
Holistic cybersecurity for Industrial IoT applications
Industrial IoT (IIoT) offers the promise of business outcomes through the use of innovative technology. The challenge for industrial operations is to develop a balanced security stance to take advantage of IIoT innovation while maintaining the integrity of industrial security best practices.
No single product, technology or methodology can fully secure IIoT applications. Protecting IIoT assets requires a holistic security approach to help address different types of threats. This approach uses multiple layers of diverse technologies for protection and detection, applied at different levels of IIoT architectures, while being implemented by different personas.
This article will provide an overview of a holistic IIoT security framework. This framework incorporates aspects of IEC-62443 and NIST 800-82, leverages CIP Security for security zoning, addresses OT and IT personas, and enables secure connectivity from smart devices to smart machines/skids to cloud applications.
IoT opportunities / challenges
Industrial IoT (IIoT) offers the promise of business outcomes through the use of innovative technology such as mobility, collaboration, analytics and cloud-based services. The challenge for industrial operations is to develop a balanced security stance to take advantage of IIoT innovation while maintaining the integrity of industrial security and safety best practices.
There are many aspects that could impact the reliability and security of Industrial IoT architectures:
Connected Architectures: Smart IIoT devices which enable smart skids/equipment/machines, which in turn enables smart plants, but also smart IIoT devices connected to on premise applications (e.g. historians, analytics) or connected to cloud-based applications (e.g. analytics, dashboards).
Convergence: This is not just technology and networks, but also cultural and organizational convergence of different personas, specifically IT and OT, groups that had little interaction in the past are now collaborating to share best practices.
Industrial standards that apply to both networking and security.
Cybersecurity Threats: growing cybersecurity threats (types and actors) increase the risk to protect the availability, integrity and confidentiality of data within IIoT architectures.
Powerful, yet simple to use tools are readily available to novice threat actors.
Scalable, reliable, safe, secure and future-ready Industrial IoT architectures require an ecosystem.
Protecting assets requires a holistic security approach to address different types of threats. Layers of technologies offer protection at different levels of IIoT architectures.
OT-IT collaboration
Converged Plantwide Ethernet (CPwE) reference architectures have been helping industrial operations converge their many disparate operational, processing and production systems into a single control and information platform, utilizing a single Industrial IoT network technology, which is EtherNet/IP.
The content of CPwE is relevant to both operational technology (OT) and information technology (IT) disciplines. CPwE consists of documented architectures, best practices, design guidance and configuration settings to help industrial operations with development and deployment of a scalable, reliable, safe, secure and future-ready plant-wide industrial network infrastructure.
Standard network and security technology by the IEEE and IETF is used by both IT at the Enterprise and operational technology (OT) for IIoT applications.
However, there are cultural differences in how the technology is applied that should be accounted for. Examples of differences would be traffic types, data prioritization, time synchronization, resiliency and security policies and procedures.
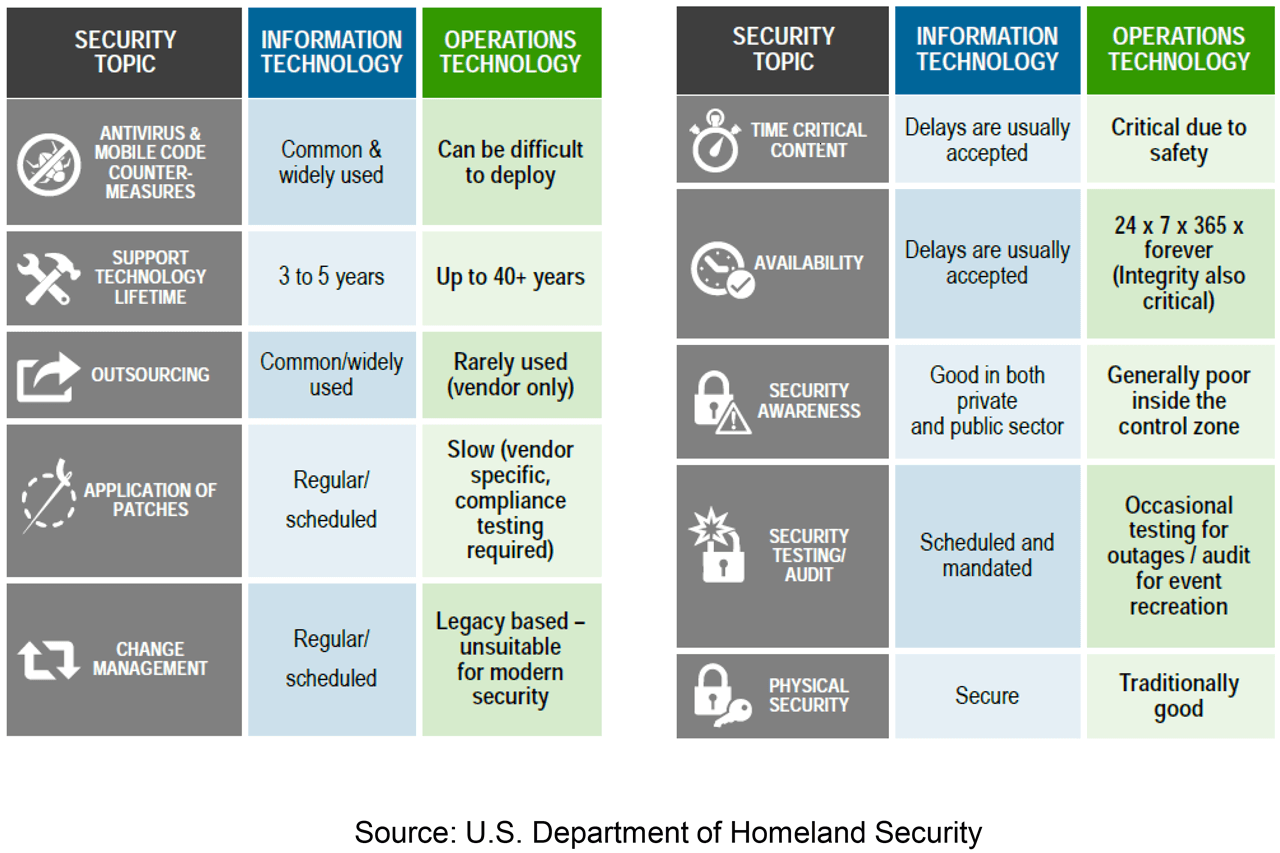
Cybersecurity – OT vs. IT.
Cybersecurity – OT vs. IT
Due to IACS application requirements, there are differences in how the technology, policies and procedures are applied between OT and IT that should be accounted for when developing an industrial security program. The following is a high-level summary:
Technology Differences:
- Software and hardware toolsets
- Varying implementations of Layer 2/3 network services may create incompatibilities
- Availability, Performance, Traffic Types, Security
Cultural Differences:
- Availability SLA (service level agreement): Minutes/Hours vs. Hours/Days
- Policies: Security, QoS and NAT, Multicast
- Skill-gaps – workforce development
- OT personnel lacking knowledge of IT skills and requirements
- IT personnel lacking knowledge of OT skills and requirements
- Lack of Industrial IT personnel that bridge the gap between OT and IT
- Challenges with Industrial IT talent recruitment, development and retention
Functional Differences and Incompatibilities between IT and OT:
- Technologies: resiliency, security
- Products: QoS policies
- Applications: WebEx & Skype vs. SCADA
- Solutions: network access control vs. application access control
Industrial Security Trends
World Wide Threat Assessment -2015: Director of National Intelligence James Clapper delivered this summary to the House Permanent Select Committee on Intelligence on September 10, 2015: “Cyber threats are increasing in frequency, scale, sophistication and severity of impact. Several nations have undertaken offensive cyber operations against private sector targets. Cyber threat cannot be eliminated; rather cyber risk must be managed. The likelihood of a catastrophic attack is remote at this time; rather, we envision an ongoing series of low-moderate level cyber-attacks which will impose cumulative costs on U.S. economic competitiveness and national security.”
According to the U.S. DHS, industrial operations led the way in 2016 for reporting cyber incidents – e.g. manufacturing, energy, water, transportation, chemical and food and agriculture. There was a broad range of infection vectors reported. Spear phishing, enabled by social engineering, was the most commonly reported.
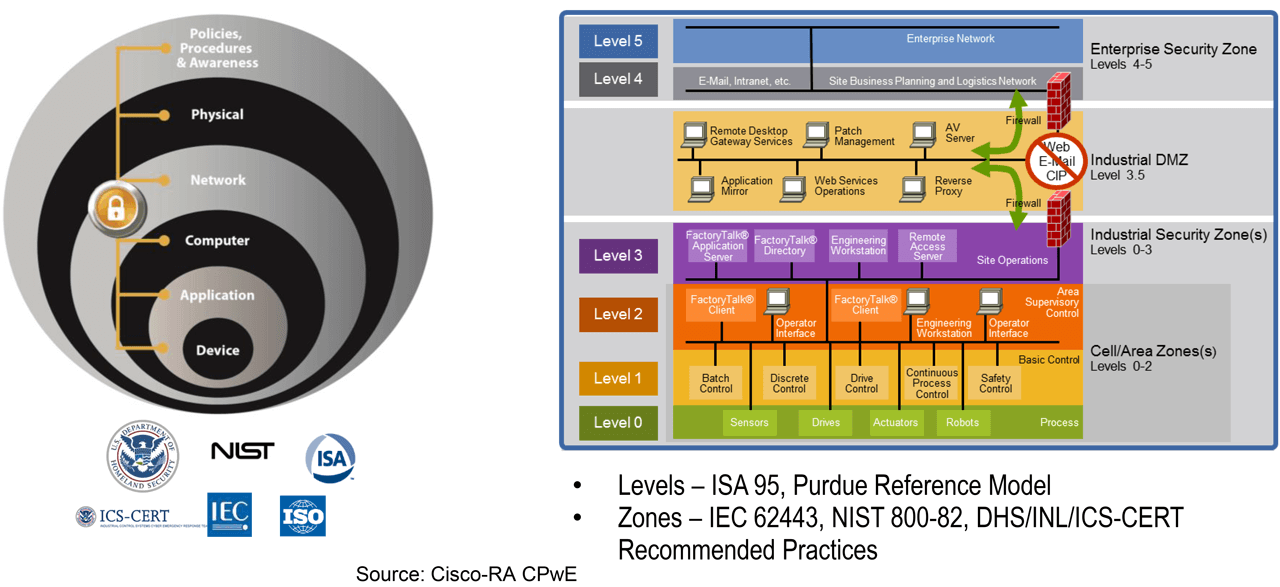
Holistic and Diverse Plant-wide Security – CPwE Logical Model.
Cost vs. risk vs. productivity
One continuing trend is the need to balance cost vs. risk vs productivity. Every industrial automation and control system (IACS) application is unique to some degree. One size does not fit all when it comes to risk tolerance and stance on availability, safety and security. What is acceptable by one industrial operator may be unacceptable to another and vice versa. IIoT architectures should support scalability, which includes the degree of holistic and diverse industrial security technologies applied at different levels of a plant-wide security architecture. Scalable security comes in many forms. Based on risk mitigation requirements, several diverse technology options are available for threat detection and prevention to help industrial operations meet their tolerance to risk.
The challenge for industrial operations is to develop a balanced security stance to take advantage of IIoT innovation while maintaining the integrity of industrial security and safety best practices. Business practices, corporate standards, security policies and procedures, application requirements, industry security standards, regulatory compliance, risk management policies, and overall tolerance to risk are all key factors in determining the appropriate security stance.
Utilize safety and security standards to help assess the required security stance to meet the application requirements:
- Alignment with industrial functional safety standards such as IEC 61508, IEC 62061 (SIL), ISO 13849 (PL), CIP Safety
- Alignment with industrial security standards such as IEC-62443 (formerly ISA99), NIST 800-82 , ICS-CERT and CIP Security
The need for early, open and two-way dialogue within industrial operations, especially between OT and IT, is critical for the success of IIoT projects. One size does not fit all when it comes to risk tolerance and stance on availability, safety and security.
Holistic and Diverse Plant-wide Security – CPwE Logical Model.
Established security standards
There are multiple organizations, consortia and government agencies that provide or reference industrial security standards and recommended practices. Each has the common threads of:
Security Zones: organizing industrial operations into functional or security zones, with strong segmenting of industrial operations from business (enterprise) networks.
Defense-in-Depth: this approach uses multiple layers of diverse technologies for protection and detection, applied at different levels of IIoT architectures, while being implemented by different personas.
IEC 62443 and NIST 800-82 is a series of standards, not just a single standard.
IEC 62443:
- General: general information which is applicable to industrial operations, System Integrators, and IACS vendors.
- Policies and Procedures: most applicable to industrial operations.
- System: most applicable to system designers (e.g. 3-2 for security zones and secure conduits) and system implementers (e.g. 3-3).
- Component / Product: IACS vendors.
NIST 800-82:
- Identify: development of policies and procedures to govern industrial operations, awareness and training for industrial operators, IACS asset inventory, IACS network discovery
- Protect: multiple layers of diverse technologies for threat protection
- Detect: multiple layers of diverse technologies for threat detection
- Respond: policies and procedures to govern industrial operations, awareness and training for industrial operators
- Recover: multiple layers of diverse technologies for IACS and asset archiving
Holistic diverse plantwide security
No single product, technology or methodology can fully secure IIoT architectures. Protecting IIoT assets requires a holistic security approach to help address internal and external security threats. This approach uses multiple layers of defense (administrative, technical, and physical), using diverse technologies for protection and detection, applied at different levels of IIoT architectures, while being implemented by different personas, by applying policies and procedures that address different types of threats.
To understand the security and network systems requirements of an industrial automation and control system (IACS), this document uses a logical model to describe the basic functions and composition of an IACS application. The Purdue Reference Architecture and ISA 95 are common and well-understood models that use Levels to segment devices and equipment into hierarchical functions. The concept of operational Levels has been incorporated into many other models and standards in the industry. Based on this segmentation of the plant operations, standards such as IEC 62443, NIST 800-82 and ICS-CERT recommended practices organize the operational Levels into Security Zones. This is a representation of the CPwE Logical Model.
Multiple layers of defense-in-depth for IIoT architectures include, but are not limited to:
- Education and Awareness Programs: training of OT personnel on established industrial security/safety policies and procedures including how to respond to a security incident.
- Physical: limit physical access to authorized personnel only: control room, cells/areas, control panels, IACS devices – e.g. locks, gates, biometrics.
- Network: restrictive access, hardening, traffic flow analysis and traffic inspection.
- Computer Hardening: patch management program, white listing of IACS applications, restrict admin privileges, removal of unused applications/protocols/services, closing unnecessary logical ports, protecting physical ports.
- Application: restrictive access, trusted communications, hardening, and monitoring.
- Device Hardening: trusted communications, change management with disaster recovery, data encryption, and restrictive access.
The CPwE Industrial Security Framework helps to provide a holistic, scalable, diverse and incremental architectural best practices:
- Defense-in-Depth: architectural best practices for holistic and diverse threat detection and protection
- Alignment with industrial security standards:
- IEC 62443, NIST 800-82, ICS-CERT
- Different Personas:
- OT – e.g. Control System Engineers
- Industrial IT – Control System Engineers (OT) in collaboration with IT Network Engineers, OT Engineers with IT skills, or IT with knowledge of OT requirements.
- IT: e.g. security architects in collaboration with OT.
- Scalability: IIoT smart device to IACS application, IIoT smart device to Level 3 Site Operations, IIoT smart device to on premise analytics in the enterprise, and IIoT smart device to cloud-based applications.
OT Persona – Plant-wide Security
Industrial security should be holistic and not treated as a bolt-on afterthought for new IIoT architectures. However, there are many solutions available to help industrial operations incrementally improve the security stance for their legacy IIoT architectures.
- Hardening for Level 0-2 IACS devices: policies and procedures, physical measures, electronic measures, encrypted communications, trusted communications (CIP Security).
- Zoning: segmenting devices and applications into functional and security zones, CPwE Logical Model, Layer 2/3 switch hierarchy with access control lists (ACLs), virtual local area networks (VLANs) for Layer 2 networks, Layer 3 network address translation (NAT) devices, and industrial firewalls.
- Port Security: network and IACS devices, both physical and electronic.
- Application Hardening: application access control, trusted communications with possible whitelisting.
- Industrial Firewall: zoning (access control for protection) of OEM skids/equipment/machines, zoning (access control for protection) of legacy networks with legacy IACS devices which have little to no security capabilities, and inspection of both IIoT and non-IIoT traffic.
- Status and Monitoring: inventory and asset management of both IACS and network devices.
Plant-wide zoning to support:
- Functional / Security Areas
- Smaller broadcast domains
- Smaller fault domains
- Smaller domains of trust
- Application micro-segmentation
- Alignment with IEC 62443-3-2 security zones and secure conduits model.
- Alignment with DHS/INL/ICS-CERT best practices.
- Segmentation of different and potentially incompatible Industrial IoT Technology.
- Establish a building block approach for scalability.
Application / Device Security:
- CIP Security, part of a holistic and diverse defense-in-depth security approach
- Connections between Trusted Endpoints:
- Reject data that has been altered (integrity).
- Reject messages sent by untrusted people or untrusted devices (authenticity).
- Reject messages that request actions that are not allowed (authorization).
- Capabilities:
- System management
- Micro-segmentation
- Device-based firewall
- This does not replace the need for network security, e.g. firewalls, network access control, and zoning.
OT/IT Persona – Plant-wide Security
Multiple layers of defense-in-depth for IIoT architectures threat detection and prevention should include, but not limited to:
- Computer Hardening: patch management program, whitelisting IACS applications, restrict admin privileges, removal of unused applications/protocols/services, closing unnecessary logical ports, and protecting physical ports.
- Network Infrastructure: hardening, access control and resiliency.
- Wireless LAN (WLAN)
- Equipment SSID
- Plant Personnel SSID
- Trusted Partners SSID
- Pre-Shared Key
- 802.1X – (EAP-FAST)
- 802.1X – (EAP-TLS)
- CAPWAP DTLS
- Remote Access Server: for central policy enforcement for plant, enterprise and remote access.
- Status and Monitoring: health status of IACS and network devices.
IT Persona – Plant-wide Security
Multiple layers of defense-in-depth for IIoT architectures threat detection and prevention should include, but not limited to:
- Network Access Control: centralized authentication, authorization and accounting (AAA), identity and mobility services, and software-defined segmentation.
- Plant-wide Firewall Management: industrial firewalls and firewalls within Industrial Demilitarized Zone (IDMZ).
- Active Directory: genesis of identity and access control policy.
- Status and Monitoring: traffic flow analysis and traffic inspection.
- Plant Firewalls: active/standby, inter-zone traffic segmentation, ACLS, IPS and IDS, VPN services, portal and remote desktop services proxy.
- IDMZ best practices: data brokers for reliable and secure communications, TLS proxy, application mirror, reverse proxy, remote desktop gateway server.
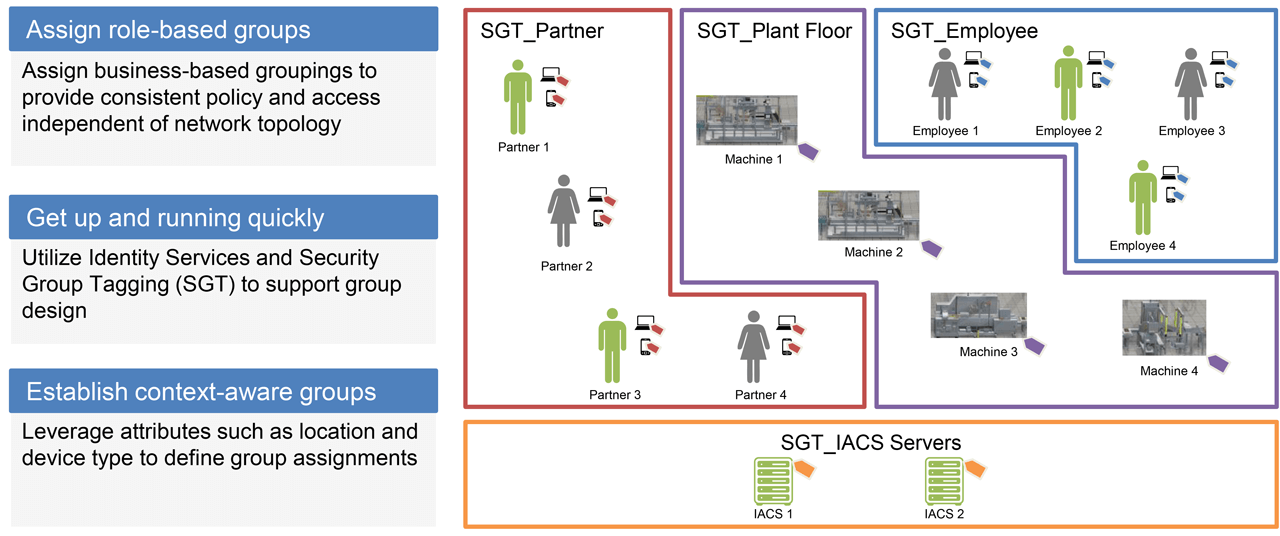
Network Security – Segmentation (Zoning) – Functional Areas / Security Groups for IIoT architectures.
- Traditional method utilized VLANs (switch port based) with static ACLs.
- Authentication, Authorization and Accounting (AAA) services added the capability of dynamic ACLs to static VLANs (switch port based). This method provides for limited programmability and automation capability.
- Source-Group Tag Exchange Protocol (SXP) with AAA services offers capability of dynamic programmability and automation since the SXP is bound to IACS endpoint and not the switch port.
Traffic flow analysis for IIoT
- Flow: unidirectional stream of packets between a given source and destination.
- IP Flow Information Export (IPFIX), were a flow record is created and cached in the industrial Ethernet switch (IES).
- Provides data about traffic flows: who, what, where, when, and how
- Network Monitoring and Anomaly Detection
- Application Monitoring and Profiling
- User Monitoring and Profiling
- Network Planning
- Security Analysis
- If one field of incoming packet is different, a new IPFIX record is created in the local IPFIX cache.
- Flow analysis, not packet analysis. Lightweight footprint, this is NOT a Full Packet Capture (PCAP).
- Various IPFIX Versions
- Traditional NetFlow (TNF): fixed info to identify a flow.
- Flexible NetFlow (FNF): user defines how to identify a flow.
- IETF Standard, RFC 5101, 5102, 6313 – IP Flow Information Export (IPFIX)
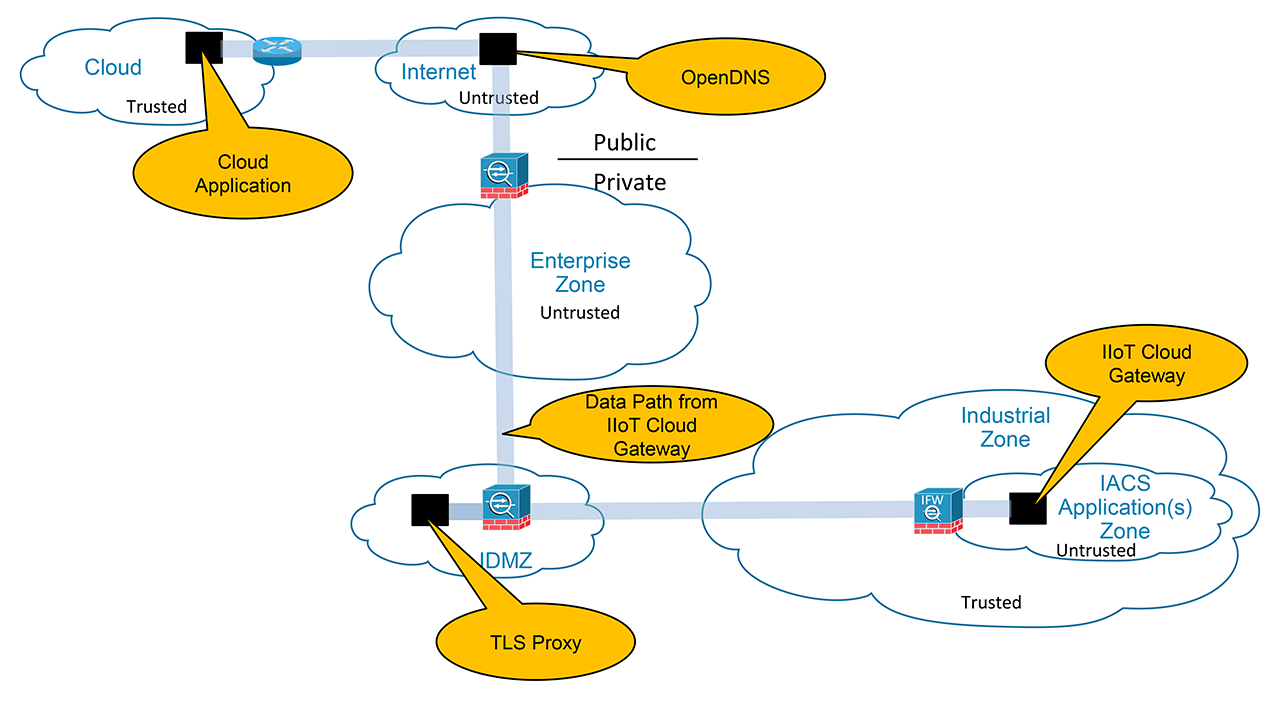
Cloud-based services help to enable data collaboration and remote monitoring of dashboards by plant personnel and/or trusted industry partners (for example, system integrator, OEM or contractor) for IACS applications within IIoT architectures. A holistic industrial security stance is necessary in order to help protect the integrity of safety and security best practices while also helping to enable restricted cloud-based services.
Industrial operations should also ensure that the cloud provider and internet service provider (ISP) are trusted. They are required to protect connectivity and data per the industrial operator’s security policies.
An IIoT Cloud Gateway should communicate with a Cloud application via Transport Layer Security (TLS). In keeping with the Industrial Demilitarized Zone (IDMZ) concept of brokered services, a TLS proxy should be located in the IDMZ. The IIoT security architecture should use the IDMZ with Firewall(s) and replicated services to buffer the Industrial Zone from the Enterprise Zone. Industrial Firewall(s) should also be implemented to enforce security policies within a Cell/Area Zone to protect the Industrial Zone from the IIoT Cloud Gateway ingress/egress point.
This security architecture is recommended for operators that require cloud-based connectivity yet have a lower tolerance to risk. Some operators may already have a TLS proxy located in their Enterprise DMZ that buffers their Enterprise Zone from the Internet. This security architecture could be implemented to leverage that existing TLS proxy. A third option is to have a TLS Proxy located in the cloud like the Cisco Umbrella Intelligent Proxy.
Reliable Secure Remote Access for IIoT
- Balanced Security Stance
- Multiple layers of diverse technology
- Edge firewall with access policies
- IDMZ best practices
- Identity services for AAA
- Remote access server
- Security zoning
- Enabling Remote Asset Management
- Protecting Integrity of Safety and Security Best Practices
No single product or methodology can fully secure IIoT architectures. Protecting IIoT assets requires a holistic security approach to help address internal and external security threats. This approach uses multiple layers of defense (administrative, technical, and physical), using diverse technologies for protection and detection, applied at different levels of IIoT architectures, while being implemented by different personas, by applying policies and procedures that address the different types of threats.
One size does not fit all when it comes to risk tolerance and stance on availability, safety and security. What is acceptable by one industrial operator may be unacceptable to another and vice versa. IIoT architectures should support scalability, which includes the degree of holistic and diverse industrial security technologies which are applied at different levels of a plantwide security architecture. Scalable security comes in many forms. Based on risk mitigation requirements, several diverse technology options are available for threat detection and prevention to help industrial operations meet their tolerance to risk.
The challenge for industrial operations is to develop a balanced security stance to take advantage of IIoT innovation while maintaining the integrity of industrial security and safety best practices. Business practices, corporate standards, security policies and procedures, application requirements, industry security standards, regulatory compliance, risk management policies, and overall tolerance to risk are all key factors in determining the appropriate security stance.

