TechnologySeptember 15, 2022
Industrial Cybersecurity 2022 Special Report
In this special report, industry experts provide their perspective on trends and innovations in Industrial Cybersecurity. Security on the factory floor is the utmost priority, with IT pushing down new technology solutions to meet networking demands, new levels of IT/OT convergence and expanding IIoT requirements.
Industrial Cybersecurity has become one of the hottest topics and a driving need for users and suppliers of industrial automation. Security has always been a priority but the complexity of solutions required, given new and dire threats in the computing world along with the new application requirements driven by the continuing emergence of the IIoT, has resulted in an unprecedented need for new ideas, technology solutions and new levels of IT-OT cooperation and convergence.
In this special report on Industrial Cybersecurity, the Industrial Ethernet Book has reached out to six industry experts to gain their insights into the the trends in security, applications and challenges for automation engineers.
Field-level cybersecurity
Becomes a prerequisite to further open up industrial networks.
According to Dirk Fischer, Software Product Manager at Hilscher, the trends in industrial cybersecurity are focusing on the needs created by IT/OT convergence, IoT application requirements and security extensions for field-level devices.
“Historically, industrial cybersecurity in automation systems has concentrated on controller-to-controller communications and using dedicated IT/OT gateways, with systems segmented into interconnected zones,” Fischer told IEB recently. “Today, integrators are primarily applying cybersecurity to the interfaces of these zones. These segments typically include operations technology (OT) industrial networks, and their device intercommunications are generally unprotected. Integrators are installing firewalls and strict, on-premises access control to increase security in this space.”
“Segmentation is a good strategy to prevent incidents from spreading and it reduces risks. However, it does not solve the issues at hand,” he added.
User groups, standardization bodies and technology providers are working on extensions to secure OT-level communications. These extensions include field devices, servo drives, IO-devices and small sensors, to name a few, and they are equipped with security capabilities. With new, heightened security functionalities, network nodes will be able to authenticate each other and data can be protected against tampering to ensure that only trusted devices can communicate. Furthermore, even data encryption is possible to protect confidential information.”
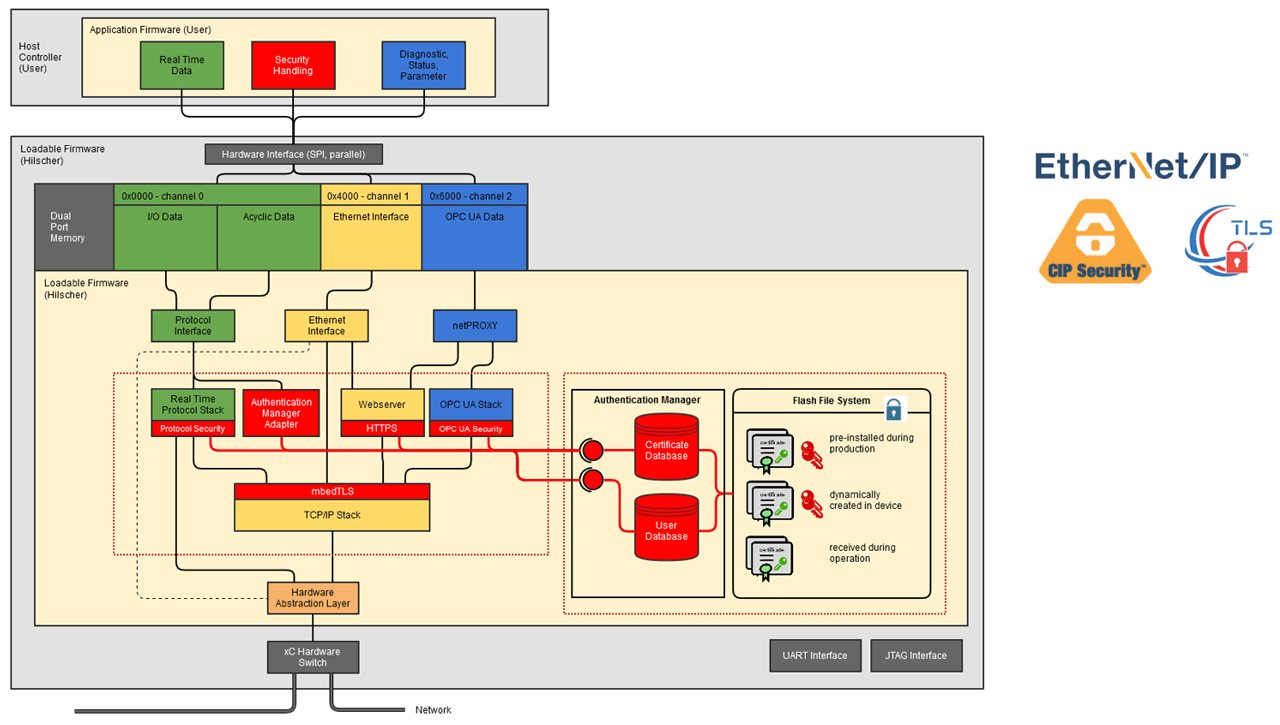
Hilscher has already implemented such cybersecurity standards into its communication protocol stacks. Devices based on the multiprotocol netX chips that feature security-enabled hardware and firmware make use of these advantages.
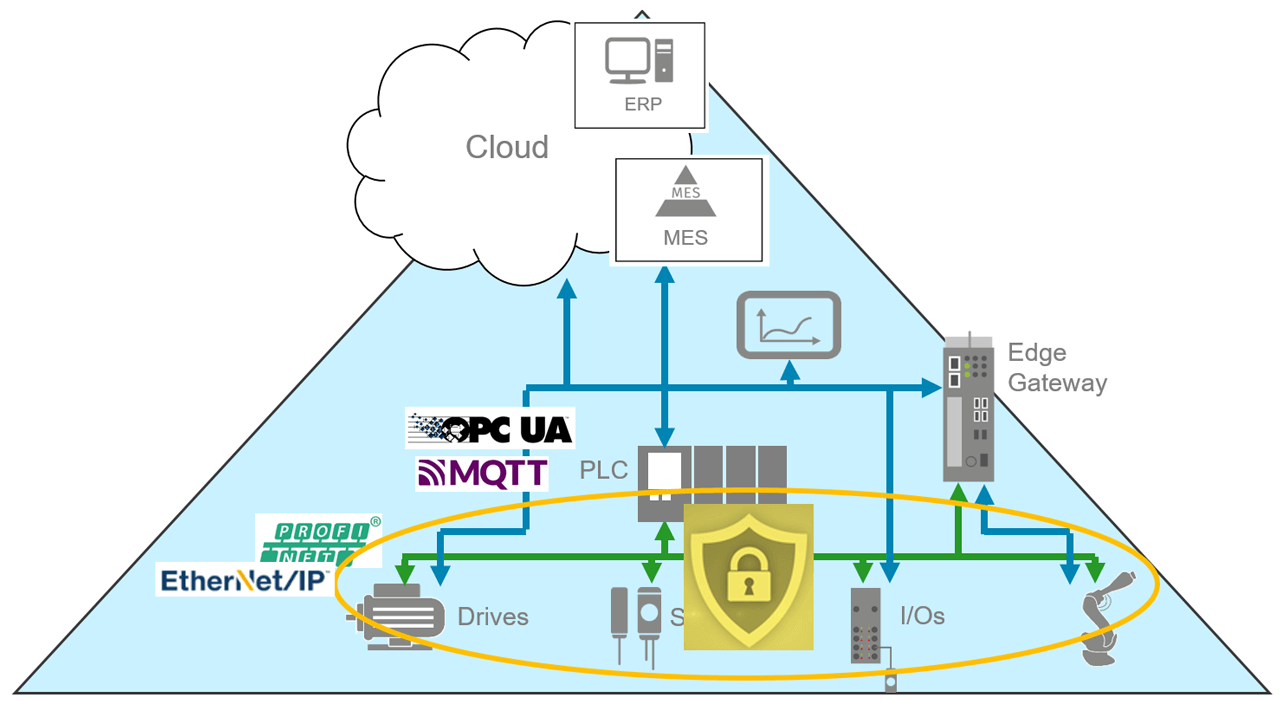
Industrial automation networking architectures now face a wide array of challenges from protecting the cloud down to the need for field-level cybersecurity.
Industrial cybersecurity benefits
Fischer added that field-level security is a prerequisite to further open industrial networks towards enterprise networks and the internet, and access to field-level data increases production process transparency and visibility. This enables new technologies to increase productivity.
One simple application is asset management, while device condition monitoring, remote diagnostics and predictive maintenance are other potential applications that enable system operators to save time and money.
“New business models are possible when applications in the cloud can directly access the field level. Machine builders can release their products and charge customers by production quantities rather than selling a machine. This will lead to more flexibility in production processes — factories could offer individualized products down to a lot size of one,” Fischer said.
Controlling physical access to industrial facilities is difficult, expensive and sometimes impossible when systems are distributed over large areas like chemical process automation systems. But, cybersecurity protected networks could make physical access restrictions obsolete. A communication channel that prevents infiltration allows a system to be exposed to the public without risks.
Fischer added that it is expected that authorities worldwide will increase mandatory requirements related to cybersecurity functions for industrial automation equipment going forward.
Device makers must follow these upcoming requirements, and can benefit from Hilscher solutions since cybersecurity functions are transparently integrated into the protocol stacks. This alleviates a lot of development-engineering responsibilities — an API interface can be used for security certificate handling.
“Segmentation is a good strategy to prevent incidents from spreading and it reduces risks. However, it does not solve the issues at hand. User groups, standardization bodies and technology providers are working on extensions to secure OT-level communications. These extensions include field devices, servo drives, IO-devices and small sensors, to name a few, and they are equipped with security capabilities.” Dirk Fischer, Software Product Manager, Hilscher
Cutting-edge technologies
Fischer said it isn’t necessary to reinvent the wheel in order to provide security functions to field devices. OT can borrow well-established security methods and standards from the IT world. One example is EtherNet/IP CIP Security, which makes use of proven SSL/TLS technology and its underlying methods, to secure IP-based real-time Ethernet communication. It uses the same cryptographic algorithms like Advanced Encryption Standard (AES), Rivest–Shamir–Adleman (RSA) or Diffie-Hellmann Elliptic Curve Cryptography (ECC) — which are all already established in IT systems. This is similar to PROFINET security and other industrial Ethernet-based communication standards.
“However, technologies must be adapted to the unique requirements of OT networks such as determinism, guaranteed timing behavior and long maintenance intervals,” he said. “But this adaptation is a difficult task, as OT devices typically have limited resources in terms of CPU performance, memory and available space.”
For this reason, Hilscher includes dedicated security hardware support to its netX 90 multiprotocol communication controller. Security-enabled firmware makes use of a hardware accelerator for encryption functions to unburden the CPU and guarantee deterministic real-time behavior.
Hilscher also provides the protocol firmware as a monolithic binary, running independently on a dedicated CPU on the netX communication controller. Users won’t have to hassle with library integration, enabling fast time to market.
When asked about specific application areas that the newest Industrial Cybersecurity solutions are targeting, Fischer said that field-level cybersecurity is potentially important for all segments of the industrial automation market. As discussed earlier, every system operator who wants to benefit from IT/OT convergence must consider field-level cybersecurity. Automation system operators must reduce the high-cost risks caused by cyberattacks.
“Authorities will define systems rules, beginning with critical infrastructure, and certain security levels will be mandatory in such systems. This shows there is a market demand for all kinds of security-enabled automation equipment such as servo drives, sensors, valves and IO-systems. These components, and others like them, will have to meet IEC 62443 requirements,” Fischer said.
“Hilscher’s solution is ideal for device makers as it provides a ready-to-use protocol firmware with integrated security functionality that helps them equip their devices quickly at a low cost.”
Meeting the challenges
Real-time Ethernet protocols are common and widespread in automation systems. But Fischer said that implementing them requires constant maintenance since the compliance test specifications are constantly adjusting and expanding. Security extensions add another level of complexity, because even if device integrators are familiar with the protocol specifications, the latest cybersecurity extensions require a lot of time to build knowledge, train and implement. The Hilscher netX 90 with security protocol firmware is a solution for this problem.
Handling security certificates poses another challenge. Each device in a secure network requires certificates which must be initially deployed (transferred to and stored on the device), then updated in regular intervals. Typically, this task is the operator’s responsibility and it should occur during normal system operation. But there are different approaches to address this issue.
“Operators may want full control over certificates and keys because they are using a public key infrastructure (PKI) or they might want to leave key generation and certificate signing to the device maker,” Fisher said. “Therefore, component manufacturers must provide flexible solutions for their products. The security-enabled protocol firmware from Hilscher provides a flexible certificate manager which supports a variety of different uses and enables the freedom to adapt to individual requirements and use cases.”
IT-like cybersecurity solutions
New functionality and solutions a necessity for users of industrial automation.
Arun Sinha, Engineer at Opto 22, said that the trend toward Industrial IoT, Digital Transformation and Industry 4.0 is a key driver behind new industrial cybersecurity solutions.
“The promise of the IIoT is that data is an asset to the enterprise. Specifically, it is not the data in and of itself but rather what actionable insights can be developed from that contextualized data,” Sinha said. “The proliferation of machine learning and artificial intelligence solutions are facilitating the use of this data in applications like predictive maintenance. That said, the processing and modeling of data is often in the cloud, but the data originates at the edge.”
He added that what is enabling these new industrial solutions is the move toward bringing more IT-like cybersecurity functionality and capabilities into edge of network devices. Advances in cybersecurity on industrial devices help you build a scalable architecture, while providing the tools and methods necessary to make your system as secure as possible from a network access standpoint. This can be done while maintaining the flexibility that is needed in an automation implementation.
As a result, a key benefit that new solutions for industrial cybersecurity offer is interoperability with IT systems, software and cloud applications with a similar level of security. Digital Transformation is predicated on previously siloed and locked down data being made available to applications and tools outside of the industrial control system network. Traditional PLCs are inherently not secure as they were not designed to exist or share data outside of the manufacturing network.
“The fundamental idea with Digital transformation or Industry 4.0 is to bring operational data from these systems onto IT networks for where software, tools and applications reside that are related to business processes. Only then can an enterprise look to improve their business through increased efficiencies, reductions in costs and improvements in quality,” Sinha added.
Bridging the gap
“Essentially this comes down to the now somewhat clichéd phrase of bridging the gap between operation technology and information technology. For this to become a reality, the systems on the manufacturing network need to be viewed from a cybersecurity perspective in the same way as those on the information technology network.”
His viewpoint is that traditional control systems are unsecure, and require other measures to be implemented, such as firewalls, air gaps and other forms of protection. New cutting edge solutions for industrial cybersecurity allow industrial control systems to be managed from a cybersecurity perspective like all other IT devices on the network. What makes these new systems unique are features on board such as dual network interfaces to separate trusted and untrusted networks, a fully configurable firewall, a built-in VPN client, secure data communications options like MQTT, user account management and security certificates.
Unlike the traditional controllers, processors, and computers typically used in automation or industrial internet of things (IIoT) applications, cutting edge control systems are increasingly built upon a custom, industry-specific build of the open-source Linux® operating system. Though it sounds counterintuitive, an open-source OS is in many ways more secure than a closed one. These products might only include only the operating system components necessary for its purpose, which reduces attack vectors. Contrast this limited vulnerability with Windows, for example, which includes components for all kinds of purposes.
Best practices suggest the build of Linux on the system be cryptographically signed with the manufacturer Private Key. That means that any firmware or software package a hacker might try to upload to the controller will not be accepted. Further, because of the number of developers working on Linux, vulnerabilities tend to be addressed very quickly—far more quickly than they can be at an individual software company with a limited number of developers.
Application targets
Sinha said that two specific application areas that the newest industrial cybersecurity solutions are targeting include remote asset monitoring and extracting additional value from legacy systems.
“Remote monitoring by industrial end users is not new, and is common in verticals like water and wastewater, oil and gas and mining. Over the decades we have seen communication methods in these industries evolve from things like satellite, unlicensed radios, fiber optic and cellular and then eventually to standard internet technology,” he said. “With this came the need to protect these networks using IT technology such as VPNs, DMZs and firewalls. The newest industrial cybersecurity solutions include moving some of these technologies into the control system itself, thus flattening the architecture and minimizing complexity.”
As digital transformation proliferates, there is an increasing need to connect to, secure and extract value from traditional control systems that were not inherently designed for cyber security, which is the vast majority. Newer secure control systems with tools on board like Inductive Automation’s Ignition Edge IIoT or Telit’s Devicewise can connect to these systems non-invasively and communicate with tags while at the same time adding an additional layer of security. This securely unlocks siloed data that can now be accessed by higher level applications for things like OEE, ML and AI.
Bridging OT and IT networks raises concerns about overall network performance. Next generation pub-sub communication protocols such as MQTT largely address this issue. MQTT with Sparkplug B data format is lightweight, reports by exception, uses a unified namespace and supports store-and-forward technology, securely.
“For an automation engineer that wants to gather, process, and share operational data from industrial equipment on premises or located remotely, cybersecurity is a big worry. Their systems and equipment—and the data in them—are essential and sensitive, and they need industrial internet of things (IIoT) devices and software that protect them,” Sinha added. “Advances in industrial cybersecurity give automation engineers the ability to advance digital transformation projects while at the same time ensuring that their devices on the OT network are safe from security vulnerabilities.”
He added that there is often a misconception that industrial cybersecurity is a product, whereas in fact it is a process. For all digital systems, security is a complex issue with different implications depending on the organization and the system. Security requirements constantly change as the system evolves, and building security into the system design is key.
“For some automation engineers, myself included, there is a bit of a skills gap with regard to IT systems, software, tools and security,” Sinha concluded. “This gap though is closing, as automation and IT professionals are respectively learning each other’s technical skills to the extent necessary to complete successful, cybersecure digital transformation projects.”

“There exists a large number of IT cybersecurity solutions like central user management, digital certificates, and endpoint detection. With increasing computer power and software and protocol support, industrial components and systems support such solutions as well and may even become integrated into solutions. This will significantly help in increasing the cybersecurity from both the technical and the organizational perspective.” Dr. Lutz Jänicke, Phoenix Contact
Technical & Organizational Needs
Well-rounded perspectives shape good security practices.
According to Dr. Lutz Jänicke, Corporate Product & Solution Security Officer for Phoenix Contact, said that new technologies and process improvements need to act together to create effective industrial cybersecurity solutions.
“There exists a large number of IT cybersecurity solutions like central user management, digital certificates, and endpoint detection. With increasing computer power and software and protocol support, industrial components and systems support such solutions as well and may even become integrated into such solutions. This will significantly help in increasing the cybersecurity from both the technical and the organizational perspective,” Jänicke told IEB.
He added that it should also be noted that security of industrial components, according to IEC 62443-4-1/2, is advancing. In the process industry, concepts like the NAMUR Security Gateway address the conflict to allow process monitoring without interfering with the core process automation.
“It should however be pointed out that technology is only one part. Having good security processes in place stays the most import aspect,” he said.
Potential impact on manufacturing networks
“Having tools like good asset and device management definitely helps to improve operation and situational awareness. If technically feasible, zero trust concepts help with end-to-end security, a sensor on the endpoint that can be used to detect security violations will help, too. It however turns out, that endpoint security solutions become ever more complex and thus can create problems on their own,” Jänicke said. “Ever seen a security tool tagging and blocking some of your applications on your PC? Imagine this happening on an industrial system shutting down a factory line. Also, cybersecurity solutions in the office environment are not real time critical beyond annoyed users. Performance impacts may not be tolerated as easily in industrial environments.”
He added that applying “cutting edge” technologies is itself a challenge and may be not the best way to go. IEC 62443 typically relates to clauses like “commonly accepted security industry practices”, which already expresses that maturity should be considered. When closely following implementation projects involving for example zero trust concepts with Detection and Reaction (xDR) capabilities, it quite often can be observed that unwanted side effects occur. This is especially true considering that automation equipment is not IT equipment based on some standard operating system in a default deployment but very often is individually designed.
And, indeed, basic concepts like defence in depth with zones and conduits, network segmentation with security appliances or enabled PLCs, supported by secure operating processes, is state of the art.
“Indeed, the focus should be put onto the demand side. Highest demands come from those areas having the greatest risks. There are critical infrastructures, for which cybersecurity by now is also a regulatory requirement,” Jänicke added. “Electrical energy, being the basis for infrastructure services, being most prominent. Process industry is facing high risks. Large manufacturers for example in the automotive industry might face significant damage in case of cybersecurity incidents and therefore are increasing their security posture as well.”
Still, the higher the risk, the more weight is put into the maturity of the security concepts and solutions applied. In any case regulatory requirements regarding operators as well as suppliers of IT/OT components will be imposed or intensified in the future.
Automation engineering challenges
The main challenge for automation engineers is keeping track of unknown attack surfaces, which continue to increase due to the growing digital footprint of industrial companies, which can lead from a single machine standstill and an entire plant standstill to an overall standstill of business operations. A second crucial challenge is uncertainty in assessing current risks and the impact on business operations.
“A security-conscious company has an organization in which security officers and automation engineers work together conducting a business impact analysis and assessing current risks. However, building a security-conscious organization is difficult and must be mandated by top management,” Jänicke concluded.

Cybersecurity For Industry Overall Visual
OT/IT and IoT Integration
Amplifying the need for comprehensive security solutions in automation control networking.
Franz Köbinger, Marketing Manager – Industrial Cybersecurity for Siemens AG, said that the combination of the need for IT/OT integration and state of the art security functions in automation systems is rising to meet the challenge of today’s cyber threat environment.
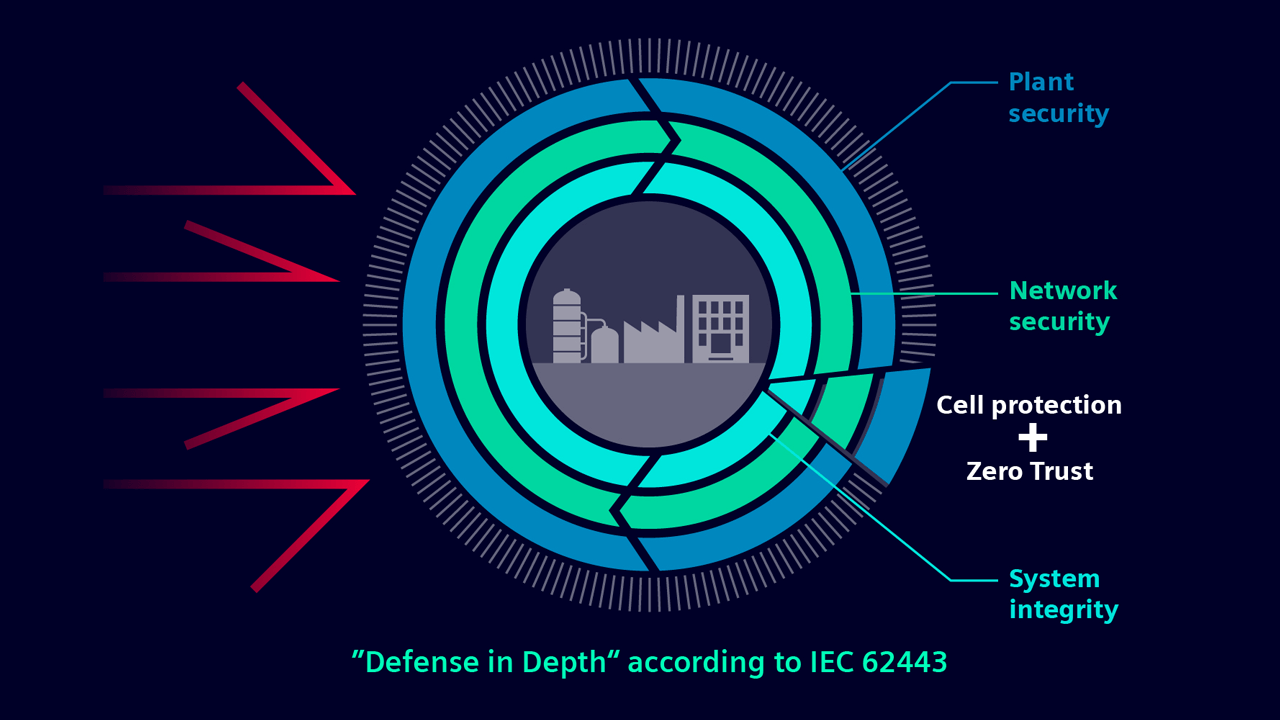
“As automation components have become part of the IoT, and due to the nearly complete OT/IT integration, it is necessary to integrate state-of-the-art security functionalities in automation systems to improve their capabilities against cyber-attacks,” Köbinger said. “So, more and more IT security standards will be used in OT as they are connected and face the same cyber-threats, now. Such technologies are, for example, certificate-based secured communication like SSL or OPC UA protocol, which will be used for data exchange between controller and other systems. Another example is the use of zero-trust principles to provide immediate and secure access to the OT environment and, in combination with other measures such as cell protection, to implement an effective defense-in-depth concept.”
He also cited specific benefits that new solutions for industrial cybersecurity offer, and the potential impact on manufacturing networks.
Köbinger said that “the use of proven, state-of-the-art security technologies in automation systems enhances the security standards in OT significantly. And this is necessary as up to now there is a gap in between OT and IT security standards. The IT is much longer connected with the Internet or other unsecure networks while the OT was usually separated and formed often ‘communication-islands’.“
But he added that, with digitalization, this changed quickly and completely. Now, the OT faces the same cyber-threats as the IT, which means it also needs the same protection. And there is no alternative or way back to avoid the digitalization or connectivity as the advantages are too great. But to use and unleash all the possibilities it is necessary to have an adequate protection which needs to be kept up to date to avoid plant standstills, production losses or data theft and manipulation. It is necessary to protect all relevant levels: the network, the system integrity of automation systems like Controller, HMI or IPCs, but also the training of people and processes for e.g., vulnerability management or intrusion detection. The integration of security functionalities in automation systems is a great advantage and step forward to an effective and easy to handle holistic security concept for manufacturing.”
“Cutting edge cybersecurity technologies are proven to be effective against cyber-threats and attacks. Unless there are vulnerabilities, which are not fixed and thus can be exploited by malware or hackers. Therefore, it is necessary not only to rely on the security technologies, but also to establish a multi-layered security concept which cannot be broken by a single vulnerability as it combines several independent security measures.
The application of some security technologies in industrial environments needs to be connected to IT security applications or at least this can offer advantages. For example, the user management for automation systems can be connected to a central user management in IT like active directory to avoid laborious and different management of the user. Or the use of the PKI for secured communication and authentication with certificates.”
Applications & Challenges
Specific application areas are the protection of critical infrastructures like food & beverage or water/wastewater. But also, every production site and OT network needs to be secured by the newest industrial cybersecurity solutions as they were also targeted by malware and hackers.
All the time and everywhere. The contribution to the overall performance of the network depends on specific conditions and cannot be answered in general terms. But this is usually not a big problem. Much more interesting is the contribution to the overall usability and production performance. In most cases the availability is the highest protection goal in OT to keep the production running.
Therefore, the main task of security measures is to keep malware and hackers out and avoid disturbances in every way. On the other hand, security measures also decrease the usability of the automation systems. Therefore, the implementation of security measures needs to be easy to use and consider the specific requirements in OT – e.g., a configuration assistant or wizard can help the automation engineers to handle the security configurations of automation systems.
“Industrial Cybersecurity requires more coordination with IT and more knowledge and awareness of automation engineers,” Köbinger added. “Also, cybersecurity is a 24/7 task and must always be kept up to date. Especially the vulnerability management is a challenge when security patches need to be installed in a running production. However, this can be supported by specific security services, for example, and a holistic security concept can enable a later update when production is still protected, and the exploitation of a single vulnerability is not possible.”
Open, standard technologies
Future proof industrial cybersecurity solutions.
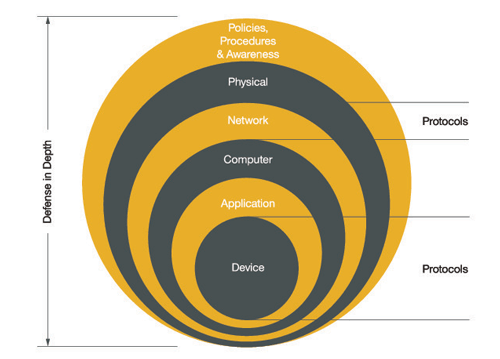
ODVA Defense In Depth Graphic
According to Dr. Al Beydoun, ODVA President & Executive Director, key technology trends are enabling new Industrial Cybersecurity Solutions.
“Open, standard technologies are the key to robust and future proof industrial cybersecurity solutions. The continuous updating, improvement, and reliance upon open security standards by an immense number of users located globally across industries is one of the main reasons to avoid creating proprietary solutions that still require the same level of investment and updating, but by a much smaller user group,” Beydoun told the Industrial Ethernet Book recently.
He added that data transfer security standards such as IETF Transport Layer Security (RFC 5246) and Datagram Transport Layer Security (RFC 6347) are a core underpinning of automation security. Transport Layer Security (TLS) uses cipher suites that determine the algorithms used for initial key exchange, encryption of application messages, and authentication of application messages. These algorithms can be understood as highly complex mathematical problems that enable messages to be secretly coded, which can then be solved or decoded by knowing a unique key. These security algorithms are constantly being updated to become more complex over time in order to stay ahead of the efforts of bad actors.
Additional open, standard technologies such as OAuth 2.0 and OpenID Connect can enable cryptographically protected token-based user authentication, JSON Web Tokens (JWT) can be used as proof of authentication, and X.509 certificates can provide cryptographically secure identities to both users and devices.
Benefits of new industrial cybersecurity solutions
CIP SecurityTM, which is a cybersecurity network extension for EtherNet/IPTM, includes robust, proven, and open security technologies including TLS (Transport Layer Security) and DTLS (Datagram Transport Layer Security); cryptographic protocols used to provide secure transport of EtherNet/IP traffic, hashes or HMAC (keyed-Hash Message Authentication Code) as a cryptographic method of providing data integrity and message authentication to EtherNet/IP traffic; and encryption as a means of encoding messages or information in such a way as to prevent reading or viewing of EtherNet/IP data by unauthorized parties.
CIP Security also uses several open, common, ubiquitous technologies for user authentication, including OAuth 2.0 and OpenID Connect for cryptographically protected token-based user authentication, JSON Web Tokens (JWT) as proof of authentication, usernames and passwords, and X.509 certificates to provide cryptographically secure identities to users and devices.
Additionally, CIP Security can provide information assurances for resource-constrained devices by requiring fewer mandatory features. Adding device level security provides a last level of defense for your most critical motion control devices.
“CIP Security relies upon profiles to allow only the necessary capabilities to be added to a device. A Security Profile is a set of well-defined capabilities to facilitate device interoperability and end-user selection of devices with the appropriate security capability,” Beydoun said.
Secure Hash Algorithm (SHA)
Beydoun added that a Secure Hash Algorithm (SHA) is an interesting example of a cybersecurity technology to examine in greater detail. The original data is transformed from its original state using a hash function into a new fixed-size piece of hashed data that is completely different. The goal of the hash function is to create a one-way transformation so that the resulting values can’t be changed back into the original data by a bad actor. SHA-1, SHA-2, and SHA-3 are SHA examples that are progressively stronger in encryption and require larger data outputs when moving from -1 to -3.
Security benefits of SHAs also include the avalanche effect where changing a few details in the original message will cause a massively different output message making it difficult to guess the input string along with tamper resistance given that slightly altered files result in a changed output hash that can alert security to the presence of a bad actor.
“Keep in mind though that no matter how tough a single cybersecurity technology is to defeat that it can eventually be overcome with enough time and resources. That’s why a holistic defense in depth security strategy is so important to adopt. Staff training, physical lockouts, network switch firewalls and deep packet inspection, updated computer virus protection, patched applications, and device defense such as CIP Security all play a role in keeping intruders out,” Beydoun said.
CIP Security is designed to be able to be used for those devices where the risk to life, property, and operations is the most critical. This means that CIP Security can be deployed in only those zones where workers could potentially be hurt by motion equipment, in devices that could reveal product recipes or manufacturing process secrets, or in lines that could cause great environmental damage. Further, CIP Security is designed so that different profiles can be applied where needed. For example, the User Authentication Profile may not be applied in a device which doesn’t have strong needs for user authentication yet does have high performance optimization needs.
Network performance can be affected with the addition of both integrity and confidentiality protection of CIP Security. Specifically, it’s not uncommon to see around a 15% reduction in I/O packet capacity or approximately a 45% decrease in standard message capacity. It’s especially important to plan for a change in capacity when using a CIP Security proxy to add protection to an existing device. Given that the security ciphers add additional traffic to the network, it’s important to assess where security is needed the most and what other network changes might need to be made to ensure adequate bandwidth for operations.
Beydoun said that another issue is that automation engineers are facing a steady increase in the number of cyberattacks. Since 2020 the number of cybersecurity complaints that the United States Federal Bureau of Investigation’s IC3 (Internet Crime Complaint Center) receives daily has increased from 1,000 to over 3,000 today.
The enhanced connectivity that less expensive and smaller chips have enabled via IIoT and Industry 4.0 has both increased the amount of valuable data that business leaders are able to access to improve their manufacturing operations as well as the vulnerability of production facilities to bad actors.
“Cybersecurity is an incredibly important business risk that can either be addressed proactively at a much-reduced cost or as a prohibitively expensive reactive measure to try to get manufacturing back online, to manage the press and customer reaction of a down facility, and to attempt to create an effective security strategy all at once,” Beydoun concluded. “Conducting regular threat assessments using the STRIDE model and creating a defense in depth strategy is a best practice to ensure uninterrupted revenue growth in today’s highly connected industrial environment.”
Driven by Connectivity Needs
Increased use of IIoT devices and cloud systems spur innovation.
Patrick O’Brien, CFSP, CACS, Safety and Cybersecurity Engineer at exida LLC is a member of the International Society of Automation Global Cybersecurity Alliance (ISAGCA) told IEB that industrial environments are continually evolving to meet new production demands.
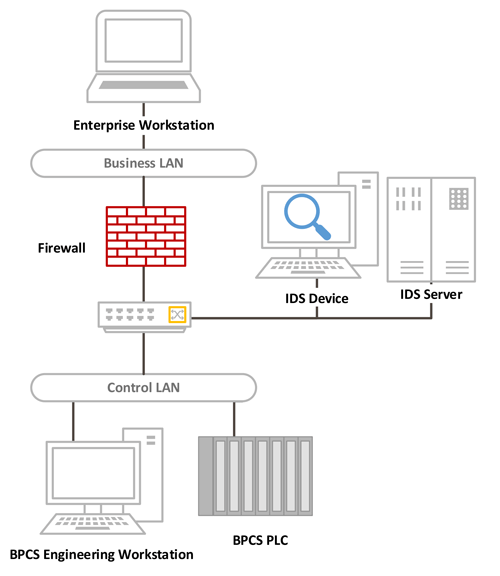
Industrial Cybersecurity vulnerabilities.
“Current trends include increased connectivity, increased use of IIoT devices, and increased use of cloud systems. As industrial systems are becoming more connected, this increases both the need for stronger security features and opportunities to introduce new cybersecurity solutions. This has also led to an increased focus on improving security capabilities for embedded components, including IIoT devices, devices with enabled wireless technologies, as well as traditional industrial components distributed control systems (DCSs), programmable logic controllers (PLCs) and safety instrumented systems (SISs),” O’Brien said.
“For these security features, we are seeing a major trend towards adoption of international standards, such as the ANSI/ISA 62443, which include clear requirements for embedding security features directly into these components. This is allowing not only for the systems to be built more secure from the start, but it is also providing the opportunity for newer solutions to be migrated from the traditional IT space to OT environments without resulting in a loss of system availability.”
 O’Brien added that building security capabilities directly into components has many benefits over “bolted-on” security measures after a component has already been developed. Built-in security features are more effective against sophisticated cybersecurity attacks, easier to implement for end users, do not have the potential compatibility issues of security measures added later and requires less ongoing support. This is a major cost saving advantage, considering the time required to implement and the cost of additional security measures.
O’Brien added that building security capabilities directly into components has many benefits over “bolted-on” security measures after a component has already been developed. Built-in security features are more effective against sophisticated cybersecurity attacks, easier to implement for end users, do not have the potential compatibility issues of security measures added later and requires less ongoing support. This is a major cost saving advantage, considering the time required to implement and the cost of additional security measures.
Improved compatibility with newer protection technologies such as endpoint detection and response (EDR) or security information and event management (SIEM) are more effective than traditional measures and have the features to successfully identify and prevent malicious activity sooner.
Identifying potential cybersecurity attacks sooner offers major improvements for the performance of manufacturing networks, because this allows operating personnel to respond to issues before a cybersecurity issue leads to a loss of production or physical damage. In industrial environments, where an hour of downtime can cost tens of thousands of dollars this makes an enormous difference.
When asked to explain what makes cutting edge cybersecurity technologies unique, he said a fundamental difference between traditional cybersecurity technologies and emerging technologies is the use of AI to make real-time decisions about whether a behavior is normal or malicious.
This can be applied to running software programs by EDR, to network traffic with intrusion detection systems (IDS) or next-gen firewalls, and user behavior by SIEMs.
“While traditional anti-virus is only effective against a list of known attacks and known malicious programs, EDR solutions can analyze new programs as they are run to determine if they are potentially malicious or not. Because existing anti-virus definitions are rarely updated in many industrial environments, and the constantly changing threat environment, EDR solutions are often much more effective,” he added.
When deciding how to apply these technologies to the industrial environment, the key question is: How can I improve the effectiveness of my cybersecurity protections, while maintaining the reliability and availability of my industrial network? While each of these technologies has the potential to improve cybersecurity, they can also lead to performance concerns if they automatically block programs or network traffic that are needed for the control system to run.
Industrial environments should start by applying these new technologies to monitor and alert an identified user of suspicious activity but should rarely be used to automatically block this activity.
One example from the user-behavior analysis side, would be a remote user logging on to address a critical production issue. An administrator logging in remotely outside of working hours to make a critical change to keep operations running or help start up after an issue, has all the markings of a malicious attack to a SIEM system (remote access, outside of normal working hours, administrator privileges, change to critical configuration file), but in this case the activity is completely valid. Instead of automatically blocking the action, if the system generates an alert instead, it provides time to respond in an actual cybersecurity event, without hindering the availability of critical systems.
O’Brien said that one difference between traditional IT networks and industrial environments is the widely varied use of different industrial protocols and the diverse components (sometimes with incompatible communications) that often need to be married together to create a functioning industrial environment.
“A big area of focus for industrial cybersecurity solutions is to adapt a traditional IT protection so that it can recognize the different industrial specific protocols and signatures,” O’Brien said. “Without this step a technology that works perfectly well in the IT environment will have limited potential to identify specific threats to the industrial environment (e.g., malware targeting common industrial vulnerabilities or unusual network behavior).”
“Another trend that is helping in part to address this concern is the standardization of many components across different industries to a set of common cybersecurity requirements. As the ANSI/ISA 62443-4-2 requirements for auditable events are incorporated, more products are following industry standard formats for event reporting. This is a significant benefit for industrial network monitoring applications and SIEMs as it allows for a direct connection of information from the industrial cybersecurity assets themselves into the protection technology, streamlining the implementation process and making the newer technologies effective for industrial use.”
Challenges for automation engineers
O’Brien said that, although much of the focus in cybersecurity issues is on the technology side, it is also a very human problem. Automation engineers often aren’t provided with the necessary training to identify potential cybersecurity issues or to effectively deal with them.
Automation engineers are already extremely loaded with responsibilities for keeping the industrial system up and running, and rarely have the additional bandwidth to address the additional burden of cybersecurity concerns. Any solution for industrial cybersecurity first needs to address these issues by providing the necessary competency development and training for users on the awareness of cybersecurity concerns for industrial networks and understanding of the cybersecurity protections that will be used.
This also needs to include appropriate resource planning for the ownership of cybersecurity protections and the time required to maintain them.
Legacy systems
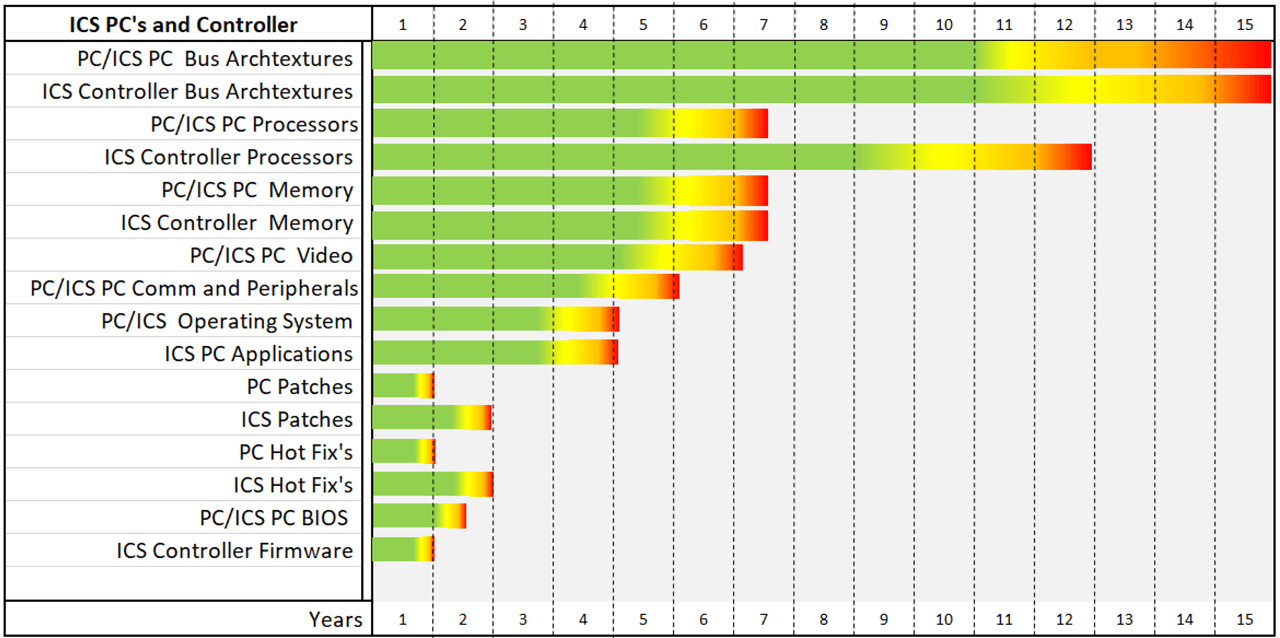
A second fundamental challenge for industrial cybersecurity is the prevalence of legacy systems. Many industrial components are expected to operate without significant change for 15+ years as opposed to the typical 3-5 year turnaround for IT equipment. The inability to make frequent changes to industrial systems due to network availability concerns, operational constraints, and abundance of legacy equipment, means automation engineer are always a step behind the latest threats.
“However, newer technologies directly combat this concern by having the capability to automatically analyze new behavior and respond, improving the effectiveness of the protection measures themselves and limiting the reliance on slow-to-update technologies. This helps to reduce the amount of ongoing support time required by automation engineers and can automate many of the activities that had to be manually completed in the past,” he added.


