TechnologyJanuary 23, 2022
IT-OT Convergence Special Report 2022

Industry experts weigh in and provide their perspective on the state of IT-OT Convergence in the modern manufacturing plant. This special progress report takes a look at cybersecurity, enterprise data connectivity and how common network diagnostic and management tools can increase IT-OT effectiveness.
Information technology and operational technology departments within industrial manufacturing plants have traditionally functioned independently. The goal of OT was to keep the plant running smoothly, and to support IT-managed business applications within the enterprise. But the world of manufacturing is changing. And to keep up, IT/OT relationships and deployment of technology must change as well.
In this special report, IEB reached out to industry experts to get their insights into the latest insights into IT-OT convergence, cybersecurity concerns, and all of the technical megatrends that are providing new management and diagnotic tools for helping to meet this challenge.
Together, IT and operations teams must go beyond responding to problems. Instead, they are key players in their companies’ transformations, helping to seize new business opportunities that make companies more competitive, more efficient and more secure.

Visionary operations leaders recognize that reams of operational data used to support real-time decision making could create additional value for companies.
Focus on Security
Forging stronger partnerships.
According to Barry Turner, Technical Business Development Manager at Red Lion, cybersecurity is a primary issue for strengthening the IT-OT, and the ability to implement a defense-in-depth strategy. Information Technology (IT) and Operations Technology (OT) personnel within a manufacturing environment often have different priorities, but generally IT departments have experience in this specific area. Education and communication enables them to work together more effectively, and especially to build the future the industrial networks that 5G and Web3 will require.”
IT-OT solutions
“Traditionally the IT and the OT have misaligned priorities when it comes to security. The OT is responsible for making it work as quickly and efficiently as possible, which in many cases is in direct conflict with the IT department’s highest responsibility, security,” Turner told IEB recently. “For that reason, it will be important that OT understand and implement key concepts the IT department has been using for quite some time. For example, defense in depth is a concept that increases the security of a network or application by adding multiple layers of protection from attacks. These layers often come in the form of VLANs, firewalls, and strict user access control.”
Technology benefits
Turner stated that increasing the network and application security by implementing a defense-in-depth strategy will help align both IT and OT and create a more robust application in general. A great way to get started is to build zones and conduits using VLANs, routers, and ideally, monitored access control. So, in terms of hardware, we are talking about routers, layer 2 Ethernet & layer 3 Ethernet switches. Using the Ethernet switches to create VLANs to make smaller networks or zones. Then using routers and firewalls to build a path in and out of those zones. It is also important to be able to have access control and some type of monitoring and alerting.
“Many times, access control can be accomplished by using access control lists which would allow access based on IP or MAC address of a network device. Lastly, the network needs to log and alert when unusual activity is detected,” Turner said.
He added that Syslog is one of many options here. It’s a technology that the IT department is already using and many industrial controls products support including Red Lion’s FlexEdge controller or NT24k Ethernet switch. Adding a layer that can detect and alert when bad things happen will ensure a controls engineer has as much time as possible to take action and hopefully mitigate costly downtime.
Convergence challenges
“Getting this very critical piece right is about education and communication. The IT department has been in this cyber security battle for a few more years than the OT. It’s a good idea to learn from that experience and build it. The IT department typically does not have unmanaged switches in their network as they do not provide features needed for a defense in depth strategy,” Turner said.
“Likewise, controls engineers would be better served to replace unmanaged switches with managed ones that would offer features like VLANs, Access Control Lists, and Syslog. Having managed switches in the network will enable controls engineers to configure their networks in alignment with the IT department. Ensuring they are able to work together, and build the future-state industrial networks that 5G and Web3 will require.”

There is an acute need for providing enterprise connectivity between systems that create data, and the users that distill data into relevant information.
Enterprise data connectivity
Software at the edge can break down barriers.
Arvind Rao, global business leader, Digital Solutions for Rockwell Automation emphasized the need for providing enterprise connectivity between systems that create data, and the users that distill data into relevant information. They key is software for taking operational data, and developing methods to take advantage of it at the enterprise level to drive decision-making.
IT-OT solutions
“Industrial data from plants and equipment is generated in huge volumes, every millisecond, which makes it difficult to capture accurately. When that data is captured, it is often stuck in siloes that make it hard to bring different data sources together,” Rao told IEB recently. “Even when you do accurately capture data and bring it together, a lot of work remains. You need to contextualize data from disparate sources, align timestamps, and prepare data models.”
Rao said that new software at the edge can help break down these barriers by providing connectivity between the systems that create data and the consumers of that data. Once the data can flow easily, data scientists can create actionable industrial performance insights.
“This is the future of IT/OT convergence – connecting data as it’s created to the analytics engines, quality systems, traceability records, and optimization programs that drive industrial efficiency,” he added.
Software that collects, organizes and contextualizes OT data and makes it available to higher-level IT applications and databases, such as FactoryTalk Edge Gateway software from Rockwell Automation, can unlock actionable plant and enterprise-level insights to accelerate IIoT digital transformation. It provides the right foundation to drive edge-to-cloud IT/OT convergence at the enterprise level, so everyone from the shop floor to the top floor can use data to make smarter decisions.
Technology benefits
Every industrial facility has numerous data sources and, many times, these data sources use different communication protocols from different vendors. To get data from the control system to the edge, multiple ingress sources are needed. This can be addressed in many ways, such as native support for the most common industrial communication protocols like EtherNet/IP and OPC-DA, or with multi-protocol solutions like Kepware.
The ingested data will be mapped to data models. More advanced solutions can set up the ingress pathways and create a data model from a controller project file at design time, reducing the need to create data models during commissioning.
Once the data is ingested, it can be processed at the edge or sent to other egress destinations. The more formats and destinations that are supported, the better. Some common destinations include specific applications, like Azure IoT Hub from Microsoft and ThingWorx from PTC and may also include generic protocols to support any destination, like MQTT.
Your priority should be to use one solution that can send data to an on-premises data center and/or the cloud.
Integration challenges
“Using the controller project file allows a more literal translation of the industrial control layer to the data layer, helping OT engineers and IT analysts speak the same language. Instead of ingesting raw, unstructured and uncoordinated data from the control system, using a data model defined in the controller can more accurately and more quickly contextualize information,” Rao said. “That means less time spent preparing or grooming data, and more time on generating meaningful results.”
The FactoryTalk Edge Gateway software leverages a unique smart object capability. This capability is built directly into the industrial control layer and transforms raw data from tags into a logical data structure that is completely configurable by the OT engineers based on the needs of IT analysts and data scientists.
This allows you to automatically build in OT data context at the source, at high speeds of sampling, and maintain that context throughout the IT layer. This increases the data’s readiness for ingestion into the next level of analytics, removing up to 70% of the effort from data engineering.
Convergence challenges
“Industrial organizations have a lot of operational data, but they don’t know how to take advantage of it at the enterprise level to compete better, such as by improving their organization’s resiliency, sustainability and supply chain agility,” Rao said. “While digital transformation initiatives are on the rise in manufacturing, CIOs and CTOs are struggling to make OT and IT worlds play well with each other and tap the hidden insights from the vast industrial data sources.”
The key reason for these roadblocks is the lack of proper correlating context, such as data source, type or timestamp, while capturing high-speed OT data at the edge. Without this critical OT context, captured industrial data has low data integrity, which translates into significantly higher data preparation efforts while building analytical models. To extract actionable insights from this OT data, it needs to be packaged in an interchangeable and flexible data format that can be easily shared between OT and IT applications.
“As it becomes easier to connect the data across the enterprise, the value of IT-OT convergence becomes greater. Smart connectivity at the edge creates that ease,” Rao concluded.
Common tools & procedures
IT-compliant standards & toolchain.
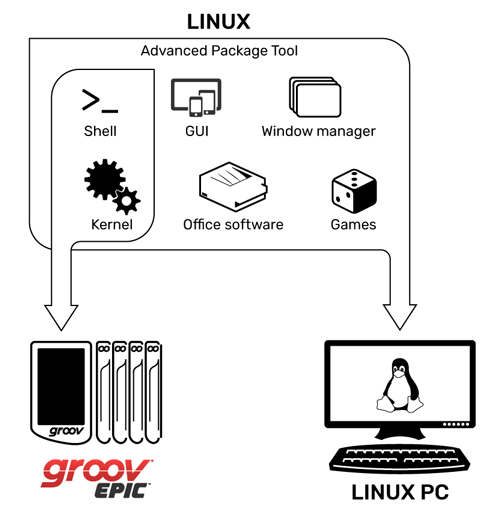
Opto 22’s custom built Linux OS for the groov EPIC includes only the packages required for EPIC’s functionality. This makes it easier to keep installations secure, stable, and up to date.
An important aspect of IT-OT Convergence is not only working more effectively together, but also adopting a common set of standards and tools, especially to deal with cybersecurity but also to manage the network infrastructure as well. Examples would be use of industry standard open protocols, and convergence on a toolset and standards that work for both IT and OT.
IT-OT solutions
The Eclipse Foundation, in its 2021 IoT & Edge Developer Survey Report, noted that Linux is the most popular operating system for constrained devices, edge servers, and the cloud. If this kind of adoption were mirrored by OT hardware vendors, many options would become available to foster convergence with IT systems.
Key among these are networking and cybersecurity technologies, which over time have created sharp cultural divides between OT and IT organizations due to a lack of interoperability. Instead of pushing proprietary protocols, OT should embed IT-compliant standards like DNS/DHCP, network firewalls, and SSL/TLS encryption, so that all devices can be managed using the same tools and procedures.
Technology benefits
Linux is an open source operating system with a significant presence throughout IT and communications systems, including much of the internet; a supportive professional and enthusiast community; and a broad range of libraries for every kind of application. These factors represent a significant difference from the proprietary, closed source operating systems that power many automation devices from the Industry 3.0 generation.
“An IT-compatible toolchain in OT eliminates questions about how to integrate the two organizations, provides greater assurance that they can operate with the same integrity levels, and moves us toward a shared vocabulary and culture about networking and security,” said Josh Eastburn, Director of Technical Marketing, Opto 22.
IT-OT integration challenges
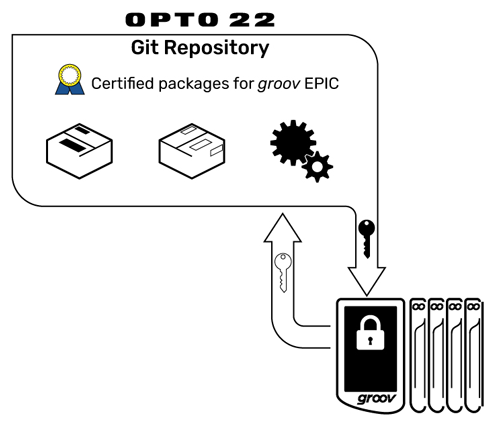
A Linux repository is where code packages are stored ,so developers can add them to applications. Opto 22 signs all code in with a digital cryptographic key indicating it has been approved for use.
Eastburn said that Linux was designed as a modular, open-source implementation of the UNIX operating system. It has a small kernel of essential functions that allow software to communicate with underlying system hardware and a broad library of modules (called packages) supplied by other open source contributors, including enterprises and non-profit foundations, which manage much of the source code.
As such, Linux has been extended, modified, and re-released many times for different purposes and powers everything from small consumer electronics, to websites, to the servers that manage the internet, and even spacecraft. Different flavors of Linux are referred to as distributions. Opto 22 uses tools provided by the Yocto Project to create a minimal, secure OS for our products based on the popular Debian Linux distribution.
Convergence challenges
“Since questions about IT-OT integration come up very often for Opto 22’s customers, it’s typical for us to meet with IT representatives to address concerns about cybersecurity and network architectures,” Eastburn noted. “Our decision to build our edge devices on Linux makes this conversation very straightforward.
Instead of explaining why IT needs to adapt to special OT protocols and procedures, we simply demonstrate how our devices can be managed in the same way that the rest of the network is managed, including things like centralized user access rights (LDAP) and automatic addressing (DHCP). This puts IT at ease and allows our customers’ projects to move forward.”
Standard Ethernet Solutions
Network diagnostic and management tools.
Dr. Al Beydoun, President and Executive Director at ODVA said that IT-OT convergence can be enhanced not only by mutual understanding of key technologies, but also a common set of diagnostic tools and capabilities. Consistent content in a common location, from different devices and different vendors, can be shared using IT tools to create greater IT-OT visibility.
Ultimately, a broad set of skills are needed to optimize industrial operations, and manage the effective transfer of valuable data from the plant to MES, ERP, and cloud systems
IT-OT solutions
EtherNet/IP has played a critical role in IT-OT convergence by providing industrial operations the information needed by management to continue to drive growth and constrain costs in ever more challenging business environments. EtherNet/IP uses standard IEEE 802.3 Ethernet technology and Internet Protocol suite standards to solve critical industrial automation applications.
“Reliance on standard Ethernet technology reduces the differences between the plant floor OT network and the broader enterprise IT network making it easier to transport critical information wherever it needs to go,” Beydoun said. “Furthermore, the object-oriented design of EtherNet/IP via the underlying Common Industrial Protocol or CIP allows for the services and device profiles needed for real time control in an interoperable environment. The object-oriented nature also makes it easier for those with an IT background to work with and to understand EtherNet/IP.”
CIP Security is also a key component of IT-OT convergence as a last layer of defense for EtherNet/IP devices to protect critical infrastructure investments and worker safety. Approaches like permit and deny listing via firewalls along with detection tactics like deep packet inspection are vital components of network security that can be enlisted in the switches that connect OT and IT networks.
However, IT centric approaches alone aren’t enough with bad actors constantly searching for weaknesses in OT networks, developing new malware, and finding more and more success with ransomware attacks. A defense in depth approach that includes the EtherNet/IP device level must be a part of a comprehensive security plan.
Technology benefits
EtherNet/IP has added a Standard Network Diagnostic Assembly to enhance the diagnostic capabilities of EtherNet/IP devices. The Standard Network Diagnostic Assembly creates a scaled architecture concept where network and device diagnostic data that was once spread out in many different locations is now combined together to be more easily accessible. This approach reduces messaging and user programming required to access data. This provides for consistent content in a common location from different devices and different vendors, which can be exposed via IT tools to create greater IT-OT visibility.
Standard Network Diagnostic Assembly Concept
Beydoun said that, with CIP Security, a self-defending device can reject data that has been altered (integrity), reject messages sent by untrusted people or untrusted devices (authenticity), and reject messages that request actions that are not allowed (authorization). CIP Security for EtherNet/IP devices makes use of the IETF-standard Transportation Layer Security (RFC 5246) and Datagram Transport Layer Security (RFC 6347) protocols in order to provide a secure transport for EtherNet/IP traffic.
TLS is used for the TCP-based communications such as diagnostics and commissioning, and DTLS for the UDP-based transport communications such as I/O data. User Authentication is provided via the OpenID Connect standard, with Role-Based Access Control (RBAC) being enforced with the CIP Security capable devices.
IT-OT integration challenges
The EtherNet/IP Standard Network Diagnostic Assembly combines ten different attributes of three different object classes into one location. One message is required instead of 10 messages per device in order to retrieve all of the information.
Making it easier for diagnostic and prognostic analysis tools/systems to utilize data that is already available in EtherNet/IP devices is one way to realize the benefits of IT-OT integration. The reduction in messages minimizes traffic and therefore required bandwidth, which is important for existing OT networks that are seeing the addition of new devices and traffic.
“Reduction in user programming, application development complexity, and changes to devices on the network allows for more valuable data to be transported from devices to the cloud for analysis and action to improve the production process,” Beydoun said. “The Standard Network Diagnostic Assembly is the first profile-independent definition of assembly instances in CIP that have data applicable to any device providing a higher level of data standardization.”
From a security perspective, CIP Security provides the last mile of security-related requirements and capabilities for EtherNet/IP devices. With the reality that not every EtherNet/IP device requires the same type of security or can support the associated resource requirements, CIP Security defines the notion of a Security Profile. A Security Profile is a set of well-defined capabilities to facilitate device interoperability and end-user selection of devices with the appropriate security capability.
| Security Properties | EtherNet/IP Confidentiality Profile |
CIP User Authentication Profile | Resource-Constrained CIP Security Profile |
| Device Authentication | X | X | |
| Trust Domain | Broad – group of devices | Narrow – Users/Roles | Broad; option to be Narrow via Gateway or Proxy |
| Device Identity | X – (Identity of User) | X – (Via PSK) | |
| Device Integrity | X | X | |
| Data Confidentiality | X | X | |
| User Authentication | X | Via Gateway or Proxy | |
| Change Detection (Audit) | |||
| Policy Enforcement (Authorization) |
Fixed | Via Gateway or Proxy |
Convergence challenges
Beydoun added that “IT-OT convergence is a requirement to stay competitive in a future where cost pressures and resource constraints will continue grow. Data must securely traverse from the plant floor to the edge and the cloud in order to continuously optimize the business.”
He said that the challenges of differing priorities regarding data confidentiality versus network uptime have become a moot point as converging networks have proven that data must remain confidential for security purposes and the production line has to keep going for cost reasons. The merging of expertise ranging from well experienced controls engineers with mechanical and electrical engineering backgrounds to workers graduating today with software training is a requirement for IT-OT convergence.
“Ultimately, all of these skillsets are needed to optimize industrial operations and to transfer valuable data from the plant to MES, ERP, and cloud systems,” he added. “EtherNet/IP and CIP Security are key underpinnings to the connection of lower level to upper-level networks to stay globally competitive and to ensure the preservation of both workers and assets.”

