TechnologyJune 1, 2021
Industrial Cyber Security Special Report
Special report in the Industrial Ethernet Book explores how manufacturing companies are leveraging new technology to protect machinery, networks and corporate data. Industry experts weigh in on the latest new technologies and applications.
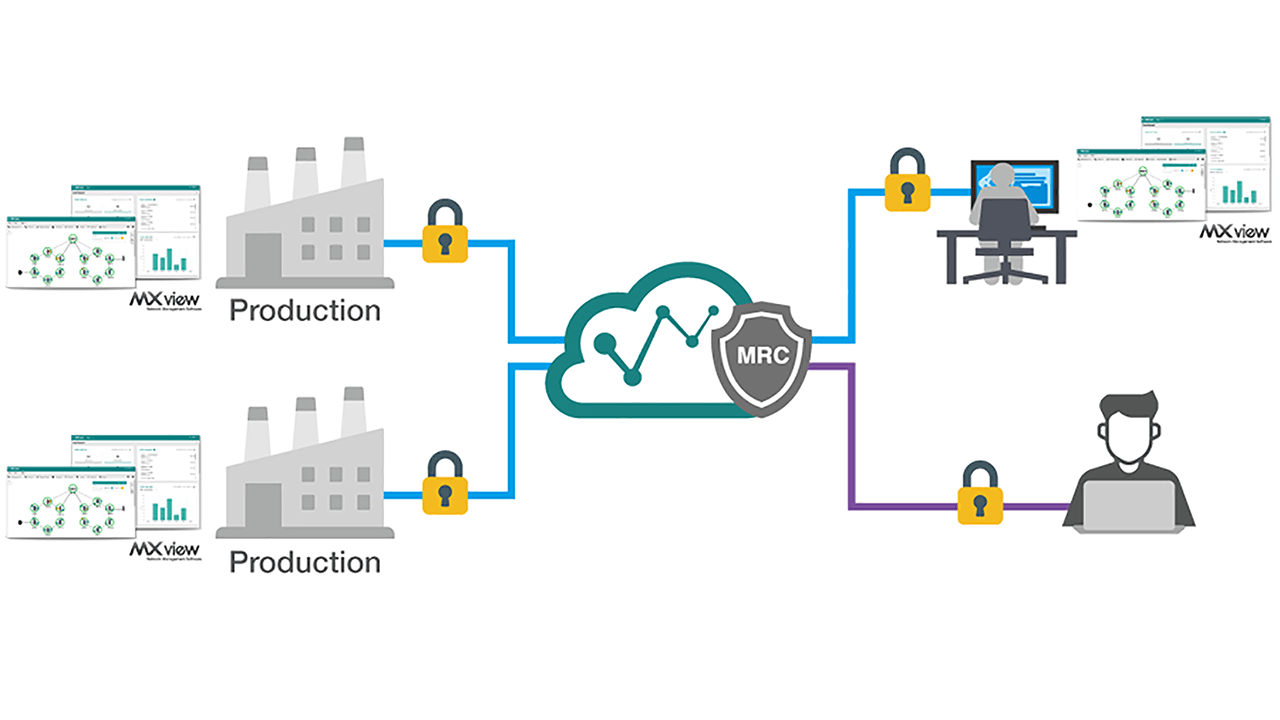
Securely Managing Remote Operational Technology Networks
Experts in edge connectivity, industrial computing, and network infrastructure solutions offer advice on how to help leverage OT technology while minimizing cyber threats.
Learn More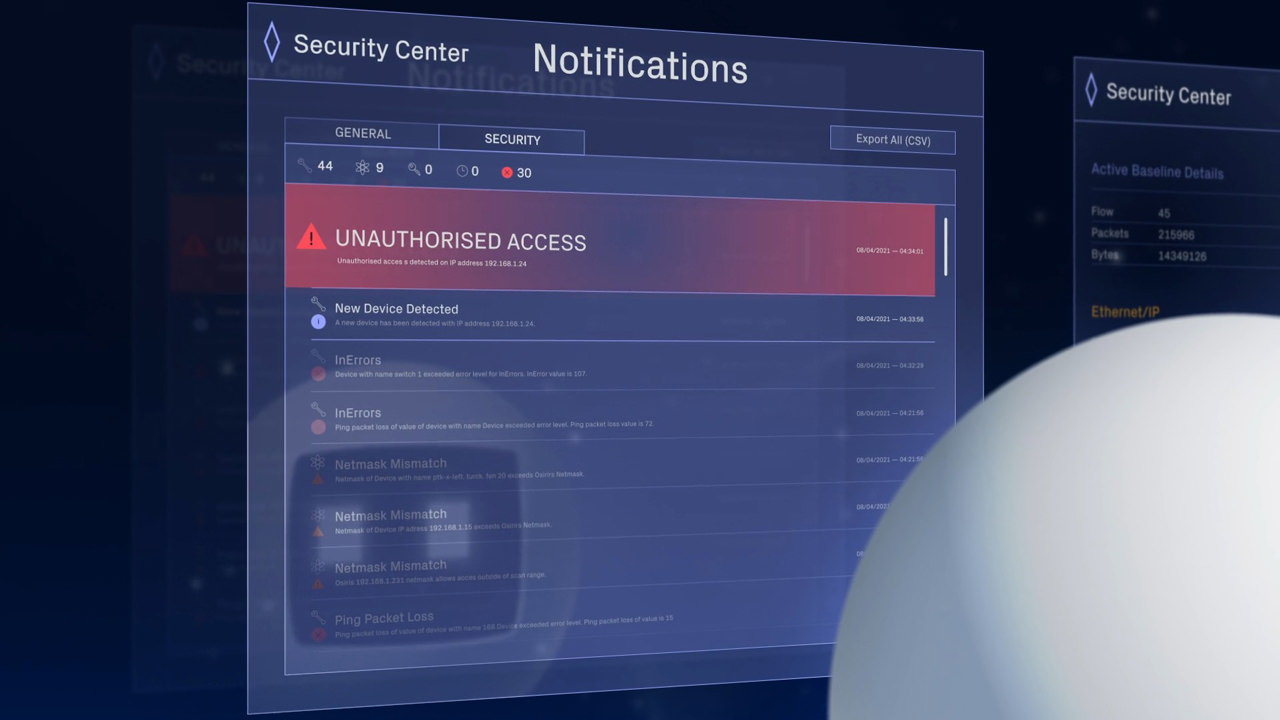
The first line of defence for industrial networks
Technology solutions are providing companies ways to eliminate network vulnerabilities and strengthen security, bridging the gap between OT and IT and sparking widespread interest in industry.
Learn More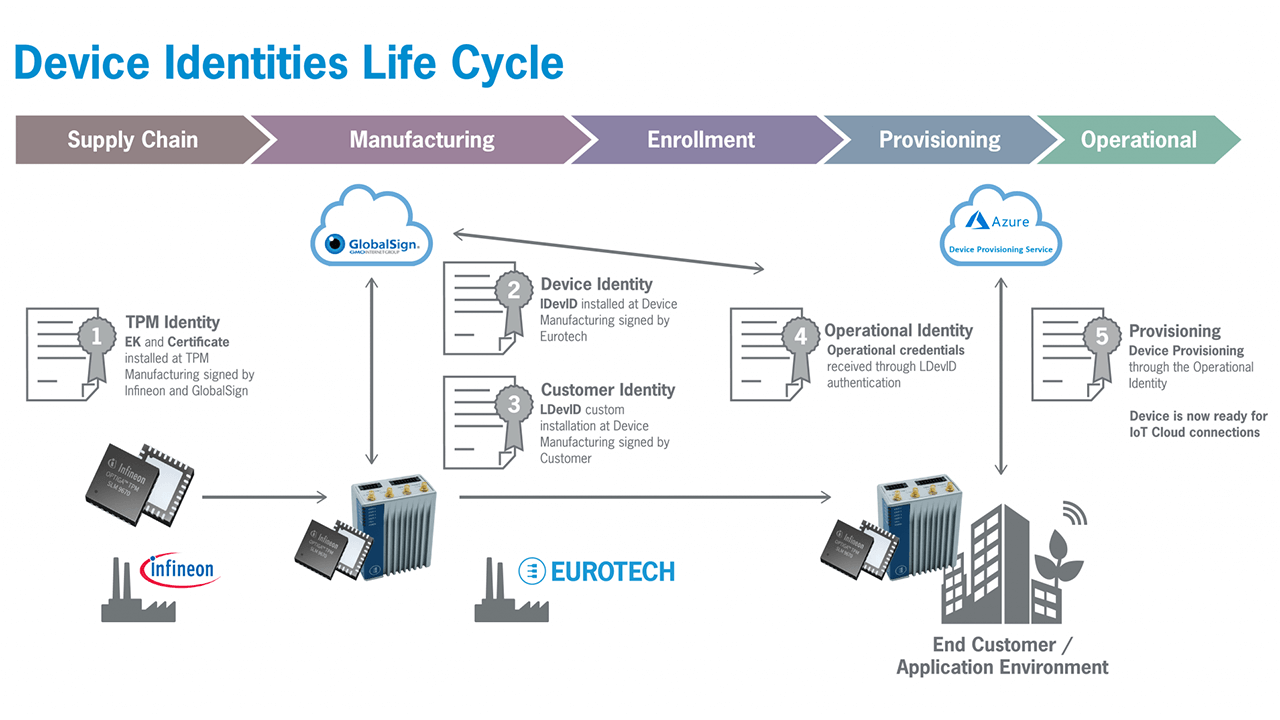
’Chain of trust’ security solutions for IoT device identities
Eurotech is collaborating with Infineon Technologies, Microsoft and GlobalSign to develop a ’chain of trust’ security solution for IoT device identities.
Learn More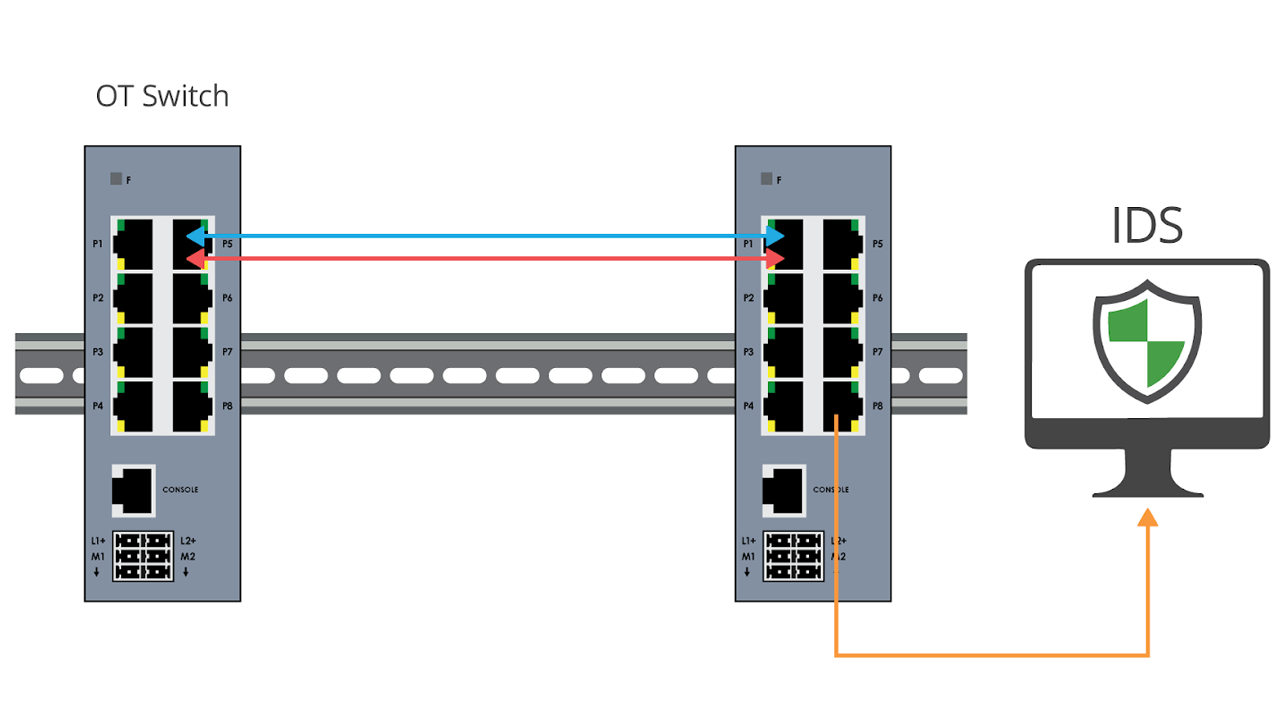
TAP vs SPAN: packet visibility challenges in OT environments
The convergence of Operational Technology (OT) with Information Technology (IT) has exposed challenges for the industrial space, including increased vulnerability to cyber-attacks and network blindspots.
Learn More
Reboot network security to enable digital transformation
he greatest risk lies in the manufacturer’s ability to secure the production environment and the end-to-end connectivity between the plant and the cloud-based services and remote users.
Learn More
Device level security for critical automation applications
Adding an extra layer of defense, particularly for motion applications, is an inexpensive way to make your facility a more hardened target.
Learn More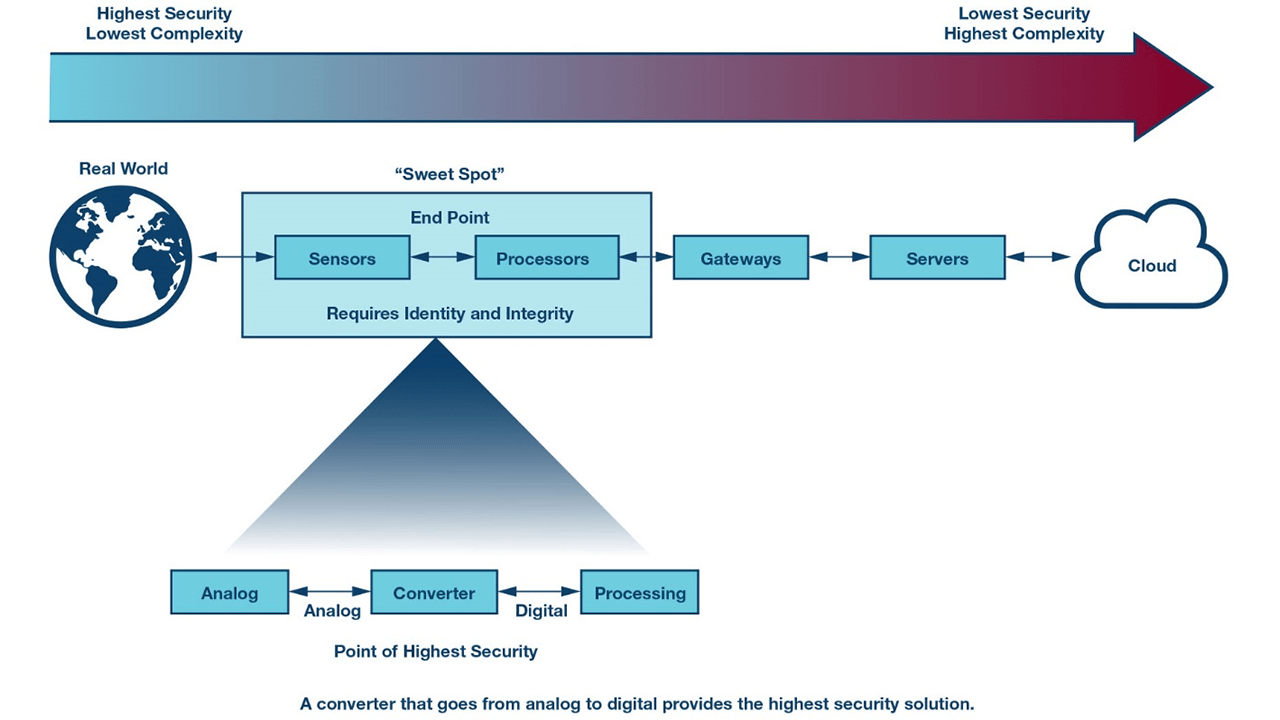
Cyber security strategies to secure the real world
Extending cyber security to the connected edge is a key strategy for industry. The devices at the edge need to be more capable, moving the analytics further to the edge and increasing functionality, autonomy, and connectivity.
Learn More
CIP Security supports resource-constrained EtherNet/IP devices
ODVA announced CIP Security, the cybersecurity network extension for EtherNet/IP, has added support for resource-constrained EtherNet/IP devices including device authentication and data confidentiality.
Learn More