TechnologyJanuary 9, 2020
Securing OT networks with unidirectional gateways/diodes
Data diodes offer a hardware-enforced solution to defend OT networks and safety systems, using one-way flow of data without allowing returning threats. As always, defensive strategies must still combine people, processes, and technology all working together to support OT network security.
Cybersecurity intrusions into OT (Operational Technology) networks, from malevolent groups are gaining more and more attention. Attacks against safety and critical systems are a growing concern and solutions to secure these systems are becoming critical. Ensuring the safety and availability of these networks are paramount in protecting our modern way of life.
There are mitigations to protect such systems, and this article will present a potential solution leveraging the use of Unidirectional Gateways and Data Diodes.
OT (Operational Technology) networks, also referred to as ICS (Industrial Control Systems) are a unique environment that houses and control systems critical to our modern way of life. OT security engineers have the unique responsibility of maintaining, protecting and securing critical safety systems and infrastructure.
These systems provide comfort, convenience, and functionalities for a high standard of living. Media headlines describing the Ukraine Power Grid attack, the cyber-attack against a German steel mill where serious damages were incurred are illustrations of the need to secure safety systems, devices, and OT networks.
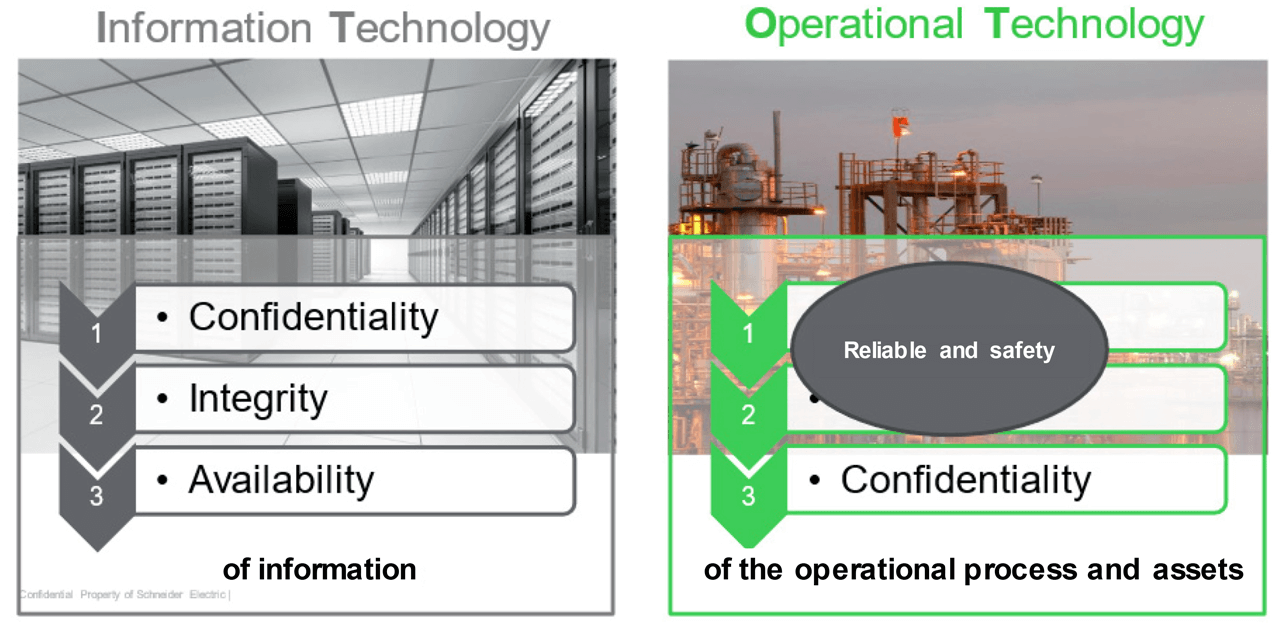
Traditional Information Technology networks or IT use the paradigm of Confidentiality, Integrity, and Availability. The OT world is primarily concerned with safety and reliability. Unlike IT systems, rebooting a PLC (Programmable Logic Controller) that is controlling and monitoring the protection of a nuclear reactor could cause serious safety issues if an unscheduled reboot were to occur. Such use cases are not realized in IT environments.
Automation pyramid and consistency.
Firewalls and routers with properly configured ACLs (Access Control Lists) are widely used to support a defense-in-depth strategy in both OT and IT networks. However, firewalls can be circumvented due to incorrect or badly written rules.
NGFWs (Next-Generation Firewalls) provide greater granularity in rule sets to filter specific applications signatures that go beyond the OSI (Open Systems Interconnection) model layers 3 and 4. They also include anti-virus protection, intrusion detection prevention systems, URL filtering and important proxy capabilities.
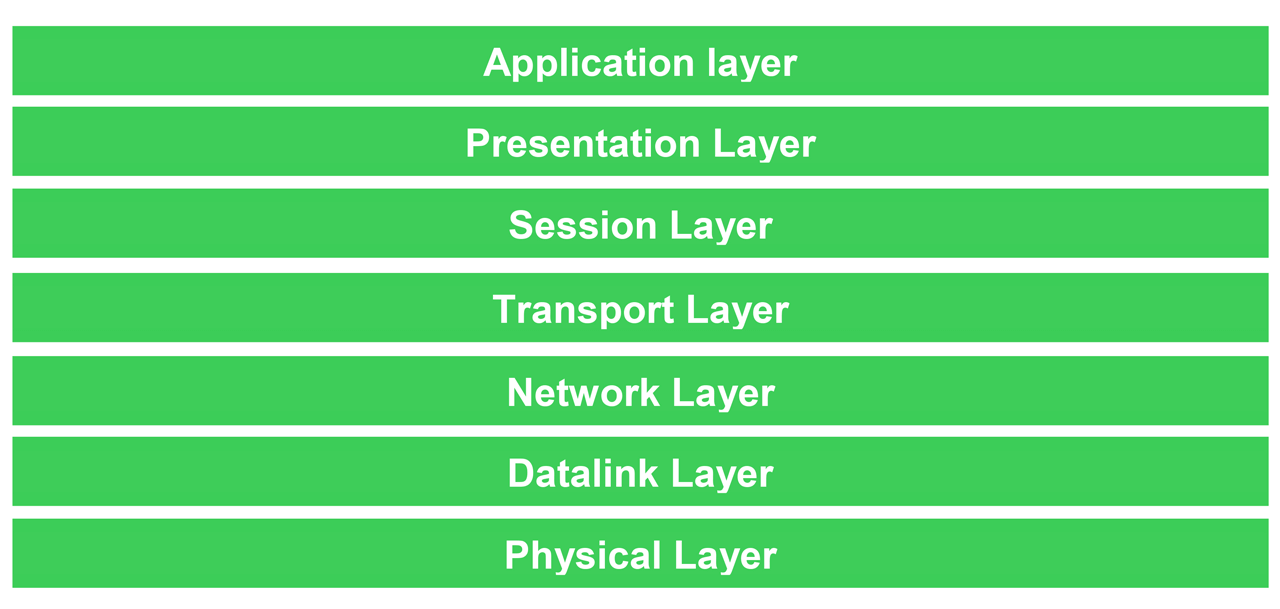
The seven layers of the OSI model.
OSI Model
The OSI model is a conceptual model developed by the International Organization for Standardization demonstrating a standard for computer and networking communications. The OSI model is a conceptual model developed by the International Organization for Standardization (ISO) demonstrating a standard for computer and networking communications.
Physical layer: This layer provides electrical functions whereby mechanical and electrical functions can be enabled or disabled. This layer includes copper and optical cabling. The physical layer translates communications requests from the datalink layer to the hardware operations affecting the electronic transmission and reception of these signals.
Datalink layer: The datalink layer is responsible for handling issues resulting from bit error transmissions. The layer makes sure that data flows without overwhelming the sending and receiving components on the network. This layer also sends transmission data to Layer 3 (Network layer) to be routed. It moves data into and out of a physical link in a network. The Media Access Control (MAC) and Logical Link Control (LLC) are sublayers within the datalink layer.
Network layer: Layer 3 is where routing takes place. The routing of network protocols allows for packet communications across multiple networks. ICMP (Internet Control Message Protocol), OSPF (Open Shortest Path First), and RIP (Routing Information Protocol) are a few examples of protocols operating at the network layer.
Transport layer
This layer provides the transfer of data and communication services for applications. Some of the protocols found in the transport layer are TCP (Transmission Control Protocol), UDP (User Datagram Protocol), ATP (AppleTalk Transaction Protocol), and FCP (Fiber Channel Protocol).
Session layer
The session layer provides the network mechanism that opens and closes mapping communication sessions for applications and processes. Examples of protocols used in this layer are NetBIOS (Network Basic Input/output System, RPC (Remote Procedure Call Protocol), PPTP (Point-to-Point Tunneling Protocol), and PAP (Password Authentication Protocol).
Presentation layer
The presentation layer provides for the conversion of data, encryption, decryption, compression, and character code transition. Protocols include Telnet, NDR (Network Data Representation), X.25 Packet Assembler/Disassembler Protocol, AFP (Apple Filing Protocol), and LLP (Lightweight Presentation Protocol).
Application layer
The application layer provides support for applications and end-user processes. Layer 7 protocols include FTP (File Transfer Protocol), TFTP (Trivial File Transfer Protocol), SNMP (Simple Network Management Protocol), and SMTP (Simple Mail Transfer Protocol), HTTP (Hypertext Transfer Protocol), HTTPS (Hypertext Transfer Protocol Secure), NFS (Network File System), POP (Post Office Protocol), SSH (Secure Shell), NTP (Network Time Protocol), and RDP (Remote Desktop Protocol).
Example of a Data Diode placed between an OT and IT proxies.
Application layer attacks
Attacks against the application layer can come via web browsers, software applications, and email clients. If application signature updates on NFGWs are not properly maintained, attackers can exploit such vulnerabilities before developers can create a patch. Zero-day attacks find flaws in applications such as this. Some examples of famous zero-day attacks are Stuxnet, Sony Zero-Day Attack, and the DNC hack to name a few.
Firewalls, routers, intrusion detection, and intrusion prevention systems do provide a certain level of protection for networks and network subnets and are a key component in a defense-in-depth strategy as well as securing zones and conduits for OT networks.
The air gap theory between OT and IT networks is at best a myth. More and more OT networks are being connected to IT networks and once that connection is made, the security and impact on safety systems on the OT side have been eroded. The 2015 cyber-attack against the Ukrainian Power Grid demonstrated how the attackers got into the IT network, and from there entered into the OT network resulting in the de-energization of half the Ivano-Frankivisk region.
The attackers demonstrated a variety of capabilities, including spear phishing emails, variants of the BlackEnergy malware, and the manipulation of Microsoft Office documents that contained the malware to gain a foothold into the Information Technology (IT) networks of the electricity companies. They demonstrated the capability to gain a foothold and harvest credentials and information to gain access to the ICS network. Additionally, the attackers showed expertise, not only in network connected infrastructure, such as Uninterruptable Power Supplies (UPSs), but also in operating the ICSs through supervisory control system, such as the Human Machine Interface (HMI).
Finally, the adversaries demonstrated the capability and willingness to target field devices at substations, write custom malicious firmware, and render the devices, such as serial-to-Ethernet convertors, inoperable and unrecoverable. In one case, the attackers also used telephone systems to generate thousands of calls to the energy company’s call center to deny access to customers reporting outages.
However, the strongest capability of the attackers was not in their choice of tools or in their expertise, but in their capability to perform long-term reconnaissance operations required to learn the environment and execute a highly synchronized, multistage, multi-site attack.
Unidirectional gateway/ data diode
NIST (National Institute of Standards and Technology) describes the following: “A data diode (also referred to as a unidirectional gateway, deterministic one-way boundary device or unidirectional network) is a network appliance or device allowing data to travel only in one direction.”
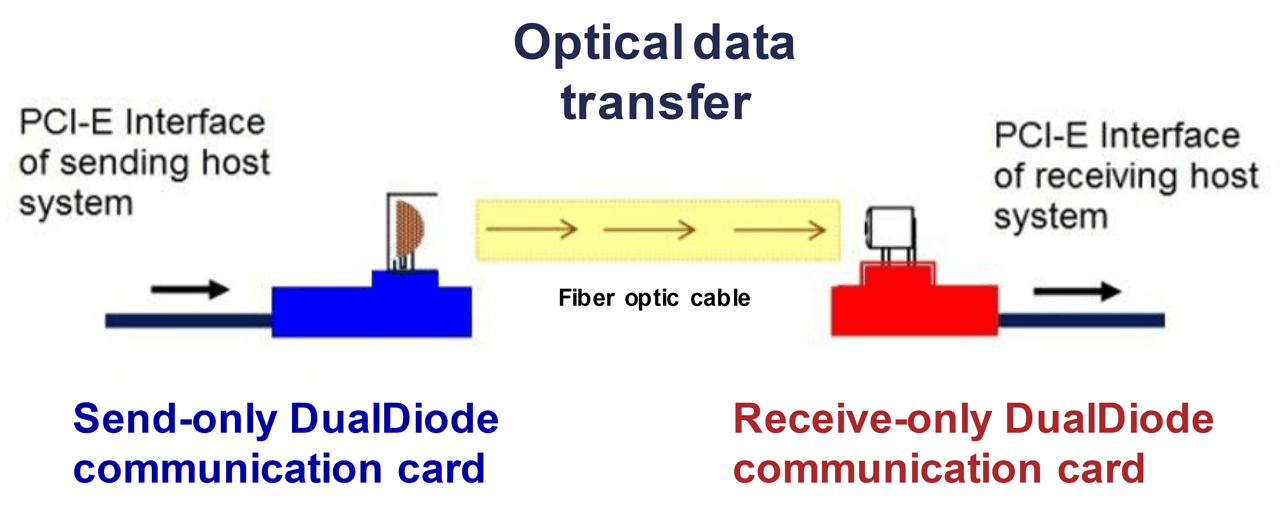
Unlike firewalls, routers and layer 3 switches, data diodes prevent return communications over the physical layer (Layer 1) of the OSI model. An example of a high-level illustration shows the internal mechanism of a data diode where the traffic entering the device from the OT side converts data from copper to the optical fiber. The device then sends the data to the IT side and reconverts that data from the optical fiber to copper then sends it out to the IT network.
Data diodes provide a level of security stronger than other network appliances, such as firewalls. These devices are configured to allow traffic to be transmitted one way only. The following table illustrates some of the differences between firewalls and data diodes.
Data diodes can use a combination of hardware and proxy computers running software on the source and destination networks. Most manufacturers of data diodes support the writing of customized software for various SCADA applications to allow specific information to go through the data diode. The hardware portion of the data diode enforces the direction, for example allowing traffic to travel across the data diode from the OT network to the IT Network. The software running on the proxy computers can replicate databases as well as several ICS protocols.
Data diodes can present a level of network complexity despite being a simple concept to understand. Data diodes provide defense against malevolent agents, negligent users, malware, and viruses. Before installing a data diode, a concise strategy must be incorporated. The objective can be to protect either an entire OT network or a specific safety system, for example, requiring information to be sent out to the IT network for reporting or analysis.
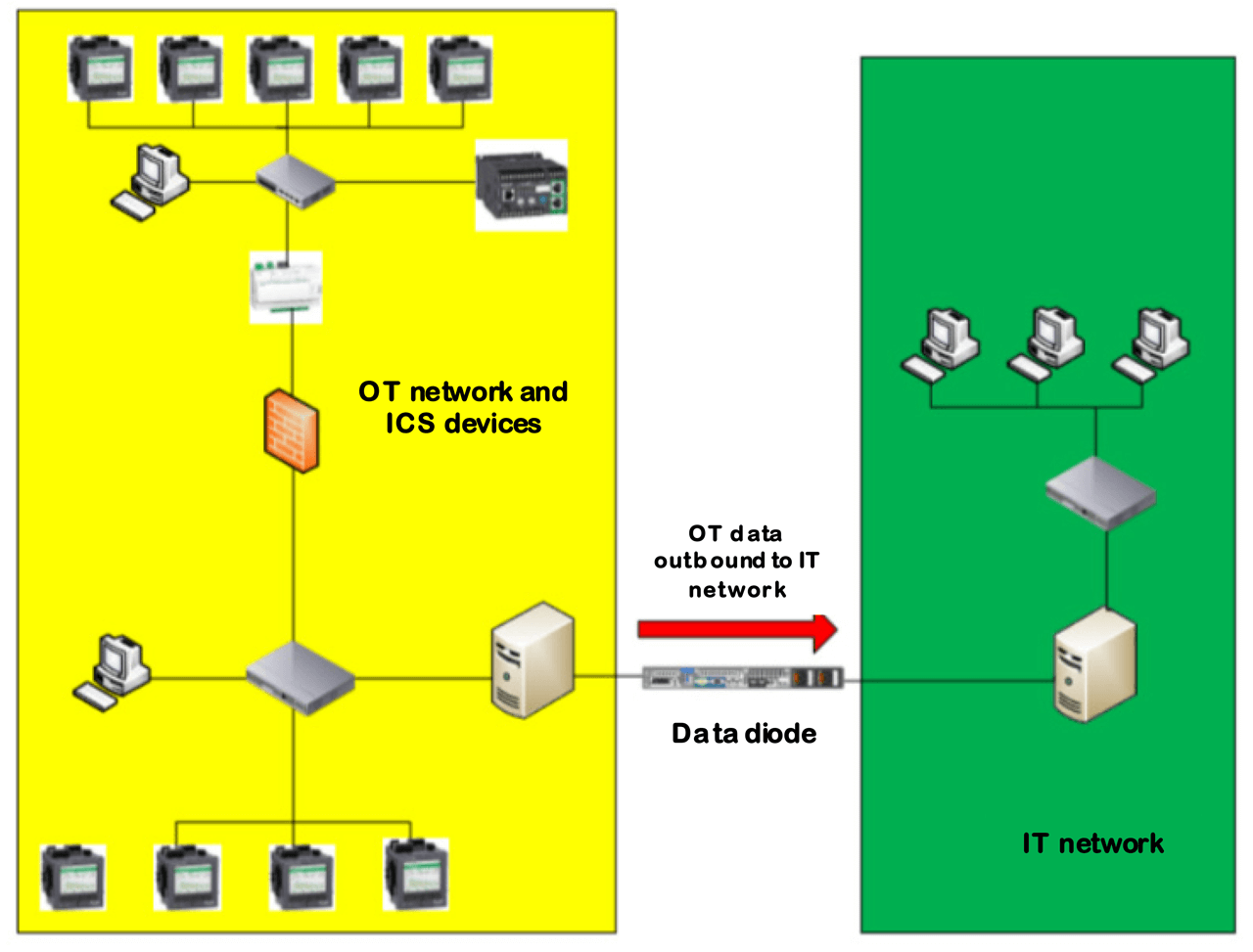
Example of a Data Diode placed between OT and IT networks.
IIoT and Data Diodes
Data diodes can be used for securing networks requiring connectivity to the cloud. A use case requirement would be to have factory information sent to the cloud for advanced analytics, the status of production, and the uptime of process and devices. The data diode would be placed behind the boundary firewall with the outbound proxy forwarding the required information to the cloud. The outbound proxy should be configured with the proper certificates and encryption mechanism to forward the required information in a secure and authorized manner.
From the cloud, authorized personnel can view the information to make any decisions concerning factory operations. One use case, deploying sensors throughout the factory forwarding information to a data aggregator, then forwards the data through the data diode to the outbound proxy, which forwards to the cloud. The firewall is there to filter and route all traffic, with the data diode preventing any inbound traffic from the outside world into the factory.
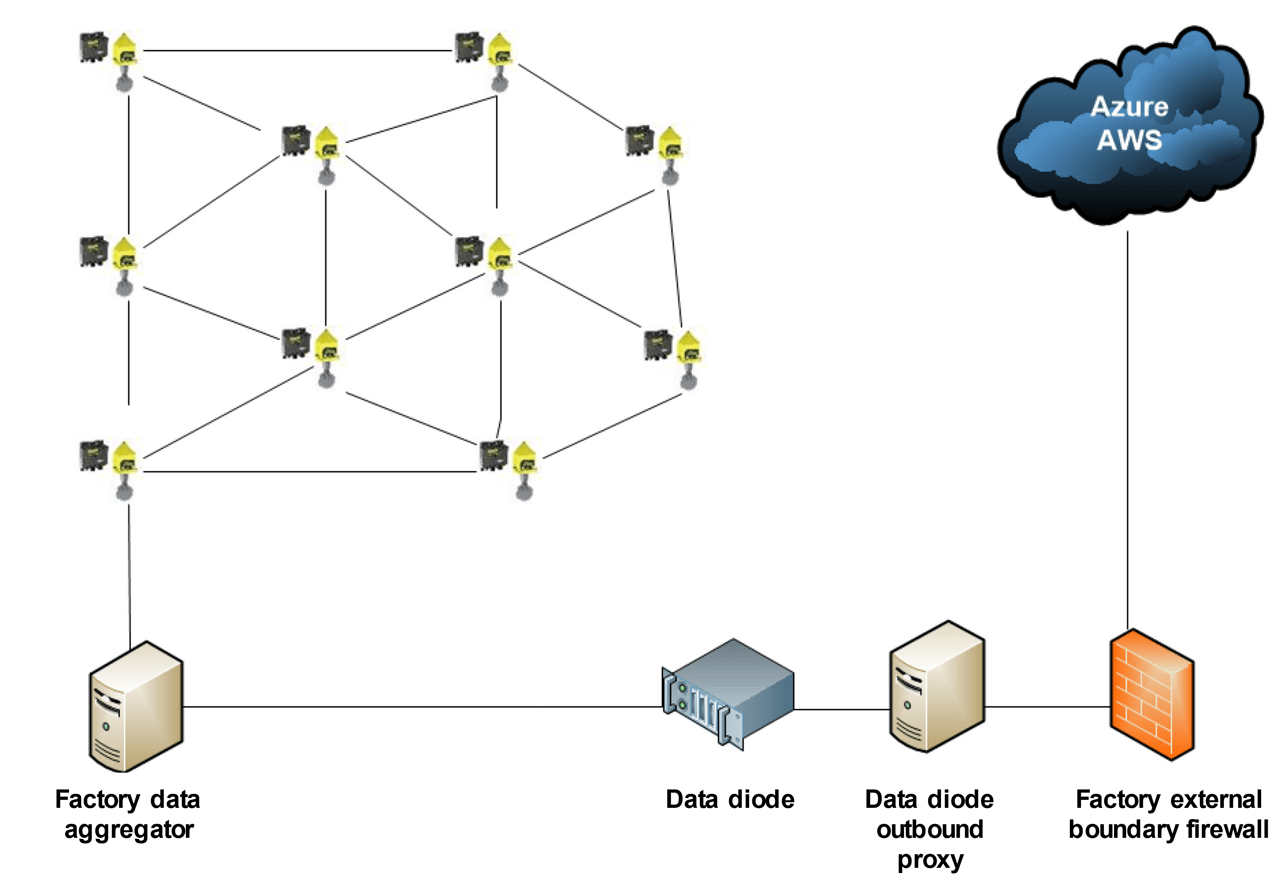
Example of data diode protecting factory external boundary while forwarding data to the cloud.
Conclusion
Data diodes provide a hardware-enforced solution to defend OT networks and safety systems. They allow the one-way flow of data without allowing returning threats into the OT network or safety system. As always, defensive strategies must still combine people, processes, and technology all working together to support OT network security.

